Thank you for booking a demo!
We’re excited to help you take the first step toward seamless compliance and stronger trust. Our team is prepping a personalized walkthrough to show how Strike Graph empowers you to manage robust compliance programs — while streamlining workflows, improving collaboration, and cutting out unnecessary work.
You’ll receive a confirmation email with your scheduled meeting details shortly. In the meantime, if you have any questions, feel free to reach out via chat.
We look forward to connecting soon!
Highly Recommended
"Their reporting and monitoring features let us keep a close eye on our compliance efforts, spot any hurdles, and measure how far we've come. It's been a real game-changer for managing our compliance projects"
"I have been thrilled with the progress and process of interacting with Strike Graph as a whole"
“The most helpful aspect of Strike Graph is its ability to automate compliance processes and provide clear, actionable insights. It saves our team a significant amount of time and effort, allowing us to focus on other critical tasks. The customer support is also excellent, providing prompt and effective assistance whenever needed."
Why choose Strike Graph?
Efficient compliance management
Streamline audits and certifications with tools designed for fast, reliable results.
Expert guidance at every step
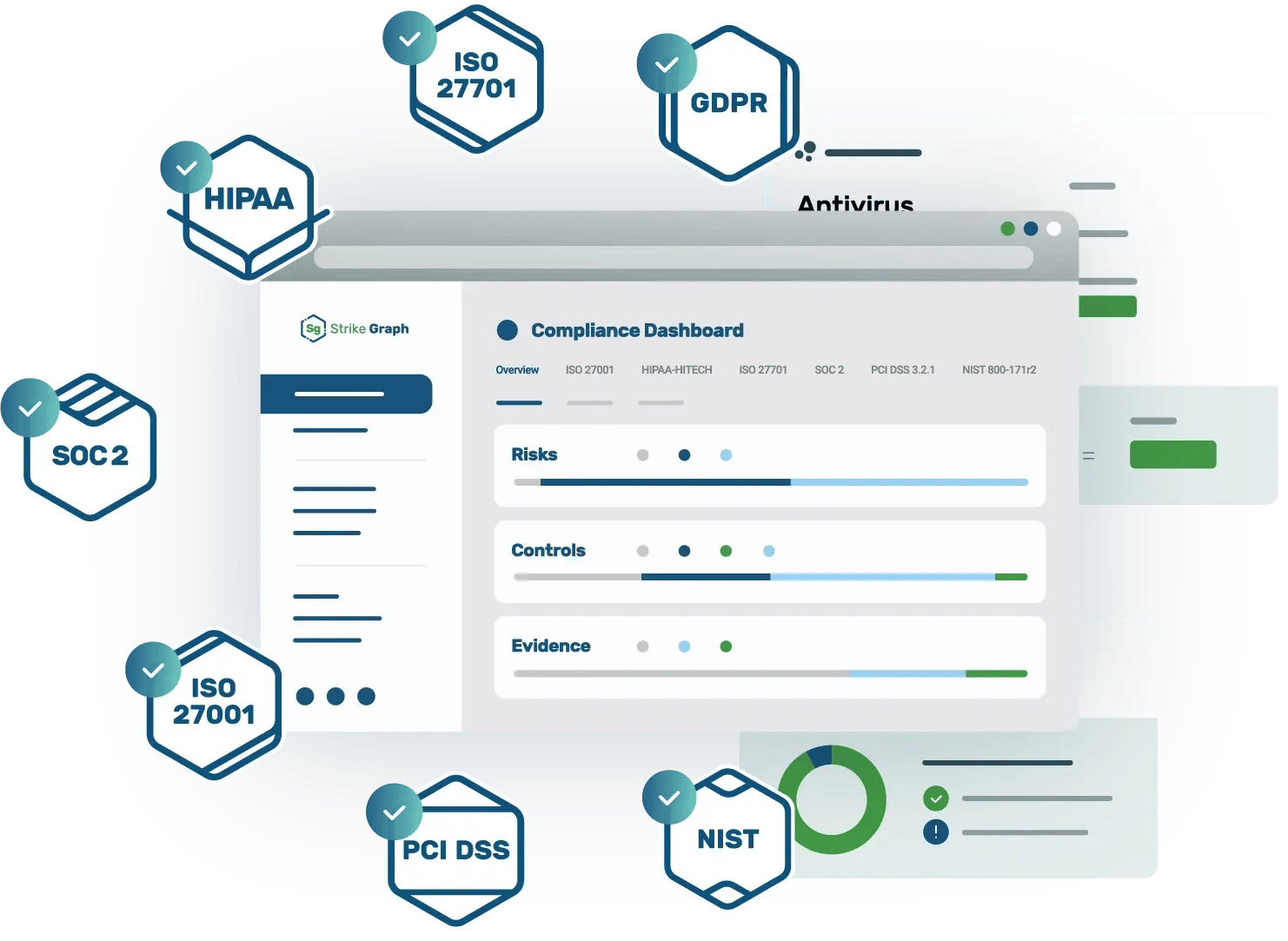
Build trust and align your processes with industry-leading frameworks like SOC 2, ISO 27001, and more.
Powerful Insights
Leverage Verify AI to automate evidence management and reduce human error. Achieve compliance milestones with intelligent dashboards & reporting.
Additional Resources
Our extensive library of resources will answer all your questions from CMMC, SOC 2 to GDPR.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)








