In today's digital age, where data breaches and privacy concerns are ever-present, establishing and maintaining trust with stakeholders and customers is paramount for any business. The way you do it is with TrustOps.
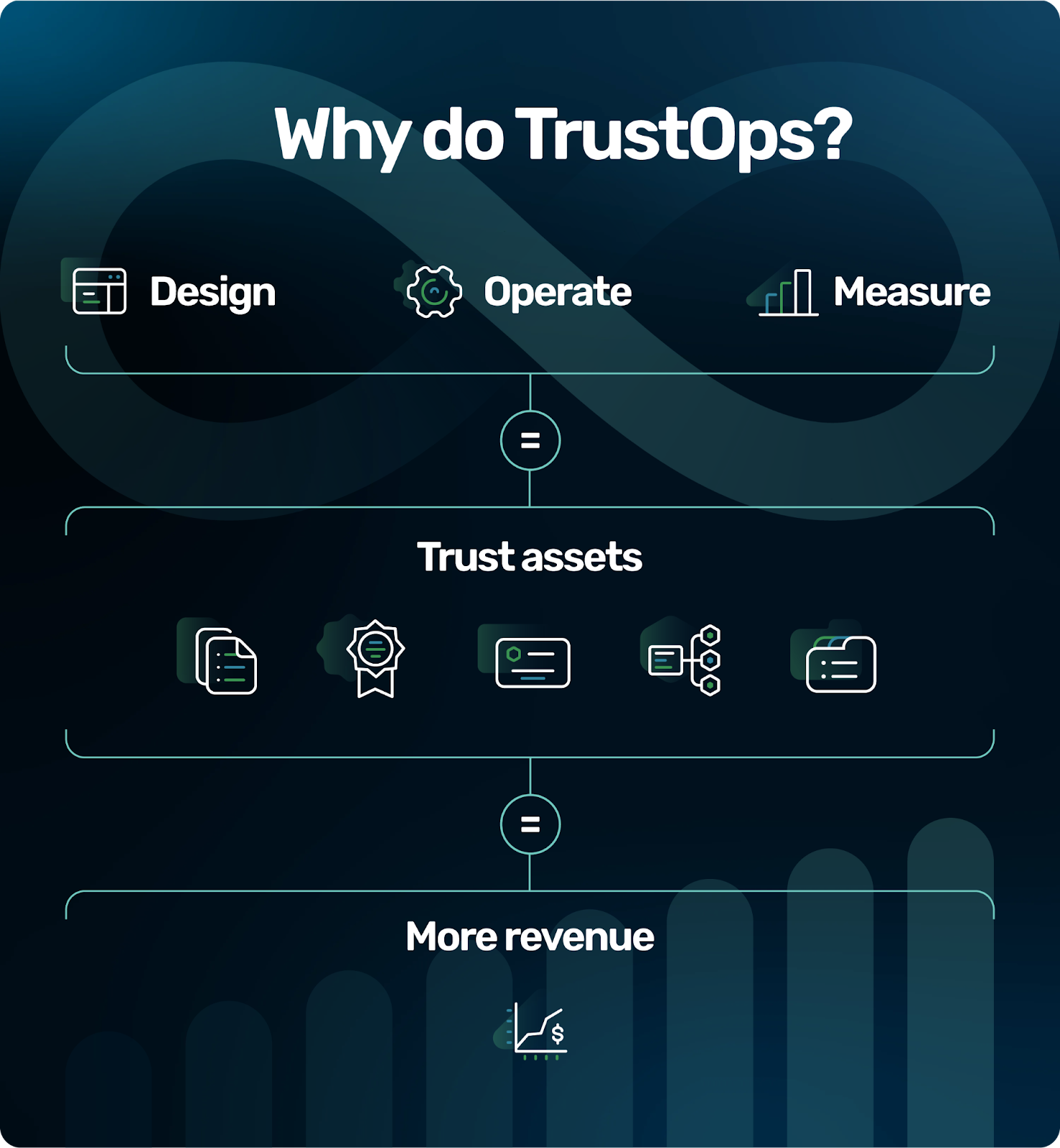
TrustOps isn't just about implementing security measures; it's about creating a comprehensive strategy that encompasses every aspect of your organization, from HR to cybersecurity. It involves adopting a control-centric security plan, ensuring cross-organization participation, and a practical implementation model that cycles through designing, operating, and measuring.
This guide goes beyond introductory information to delve into the intricacies of TrustOps, offering insights into its fundamental concepts, practical implementation strategies, and the role of tools like the Strike Graph platform in simplifying and enhancing this process. Whether you're a small business or a large enterprise, understanding and applying TrustOps can significantly elevate your security posture and build lasting trust with your audience.
What is TrustOps?
Let's start by defining what TrustOps is.
Essentially, TrustOps refers to the intentional, holistic, centralized, and transparent approach to security and privacy that helps your business build and maintain trust with your stakeholders and customers. The reason TrustOps is so powerful is that it makes your security and other trust-building efforts measurable — in terms of both cost and benefit. This means you can plan, monitor, predict, and compare your trust-building activities more effectively.
What does TrustOps look like in action?
TrustOps is not a linear process — how could it be in the ever-changing data security and privacy landscape? Instead, here at Strike Graph, we approach TrustOps from a design-operate-measure perspective. A successful TrustOps team moves in and out of these phases, often overlapping, to meet the dynamic security demands of its company.
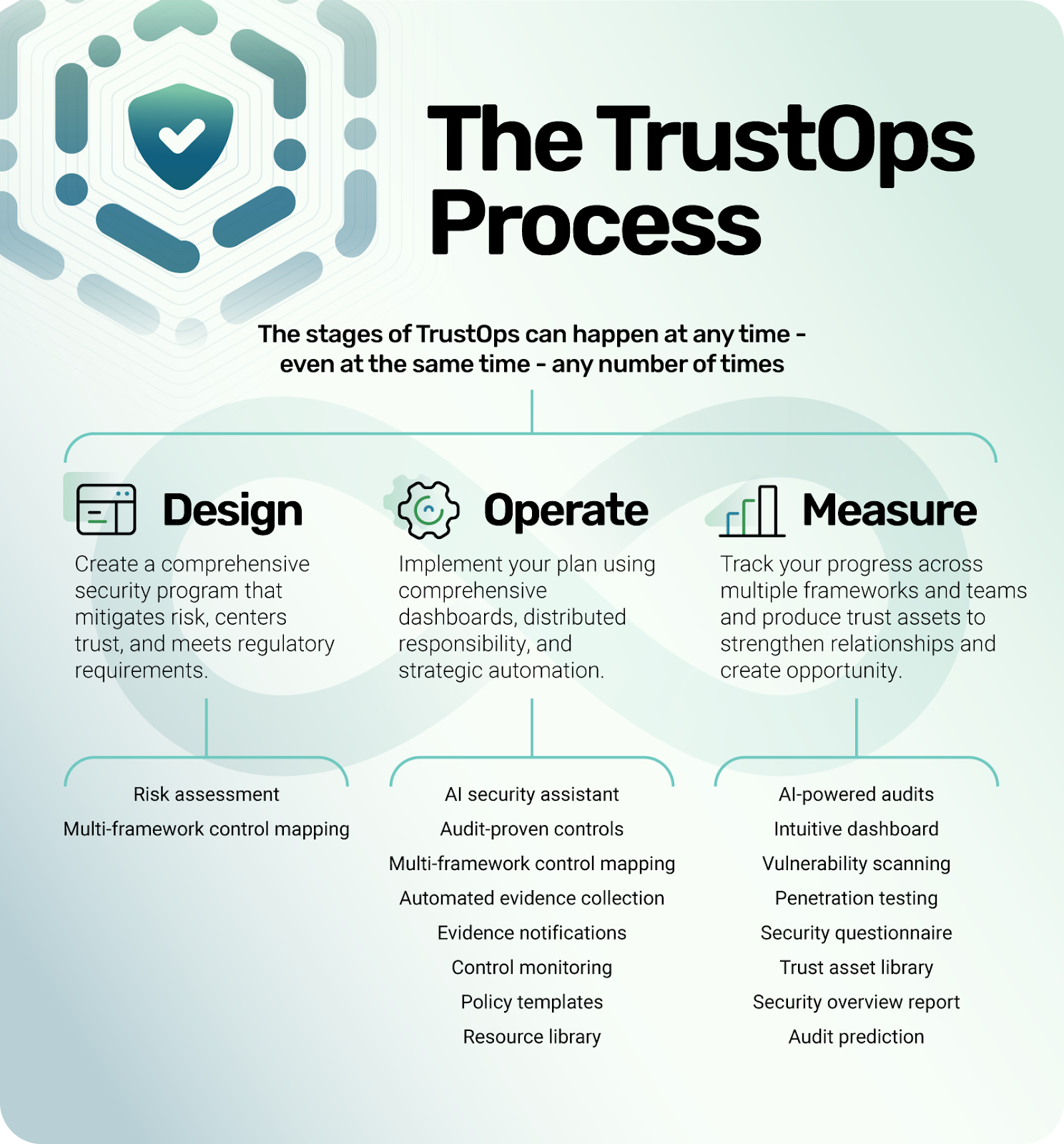
At the most fundamental level, you can think of the phases in this way. During the design phase, your team will create the security structures and strategies that will allow your company to build trust. The operate phase is when your team will implement the actions defined in the design phase, actively mitigating your risks. The measure phase (which you can also think of as the certify phase) is when you’ll conduct audits and other assessments to prove that your TrustOps program is working and identify gaps that need to be addressed.
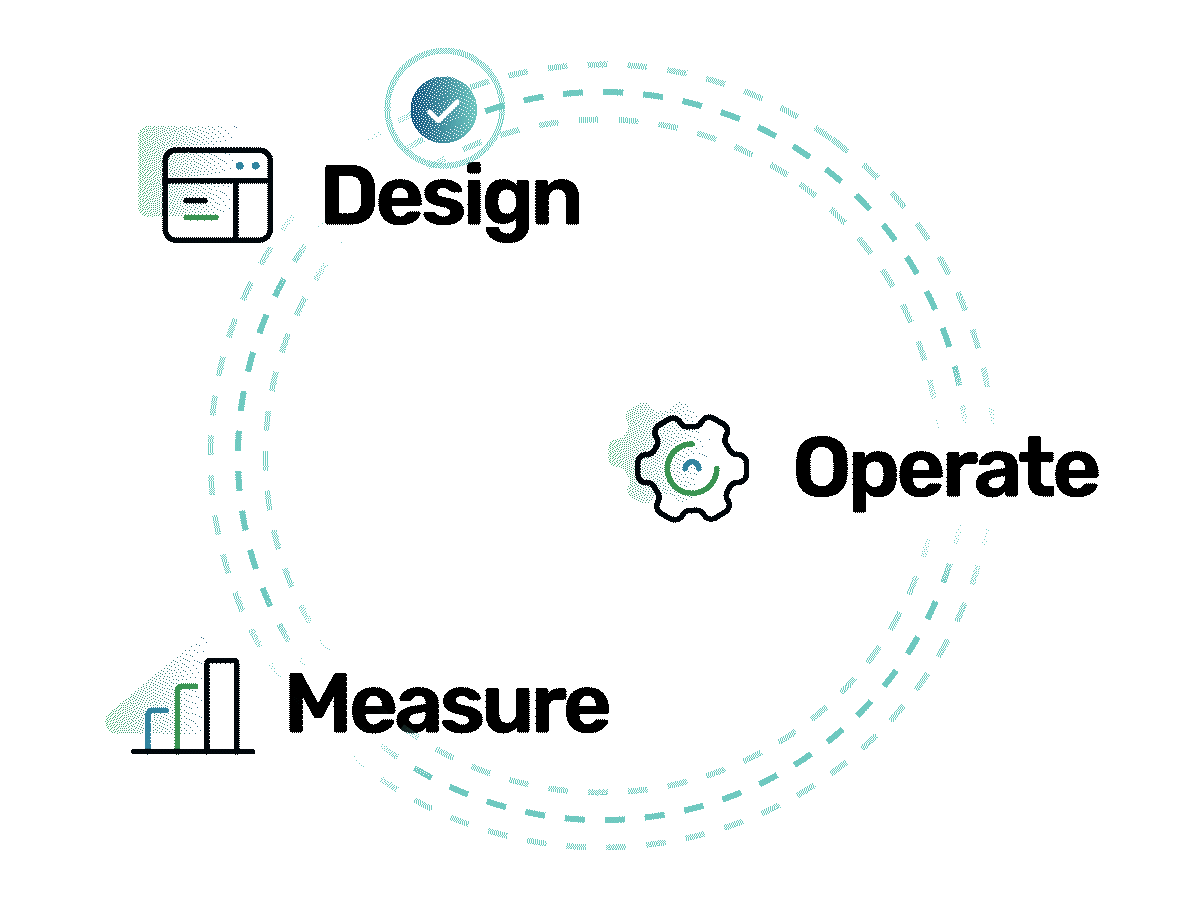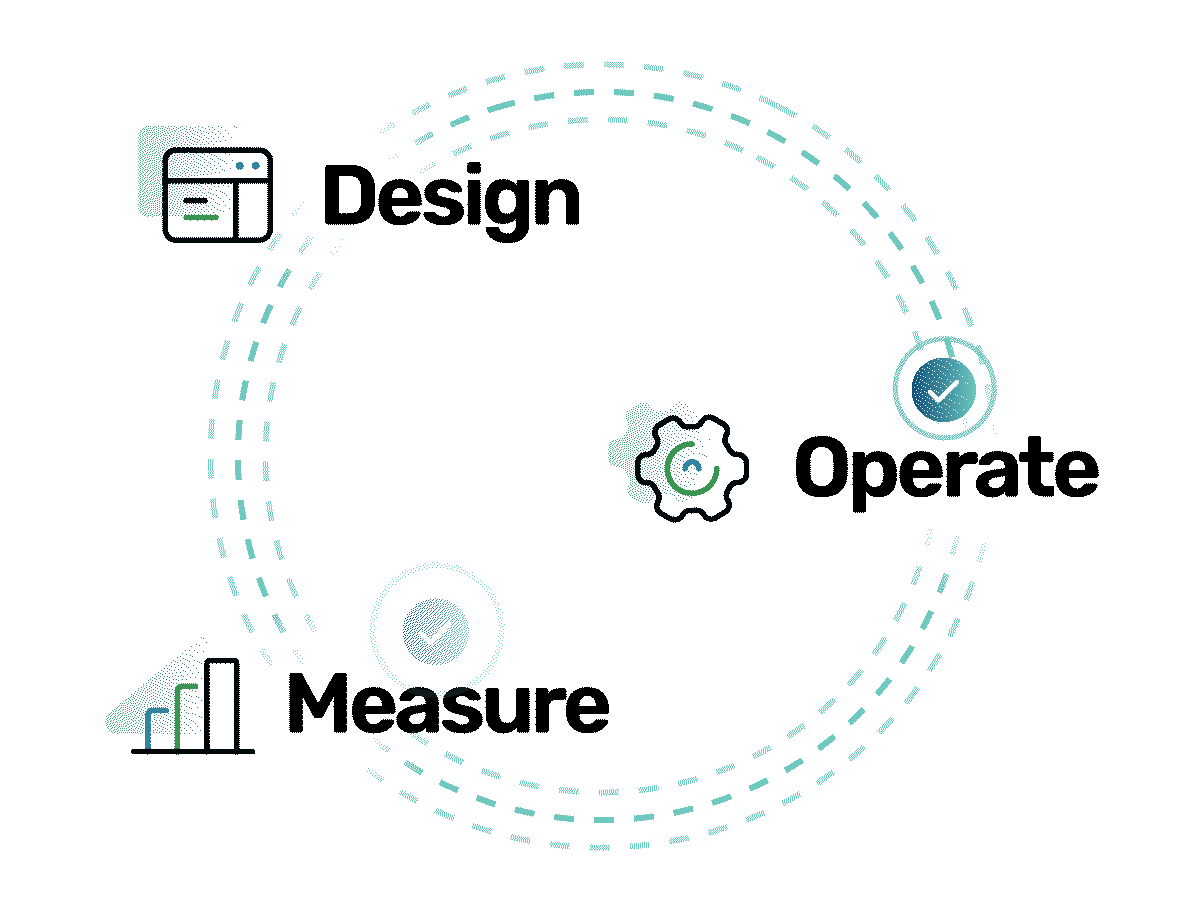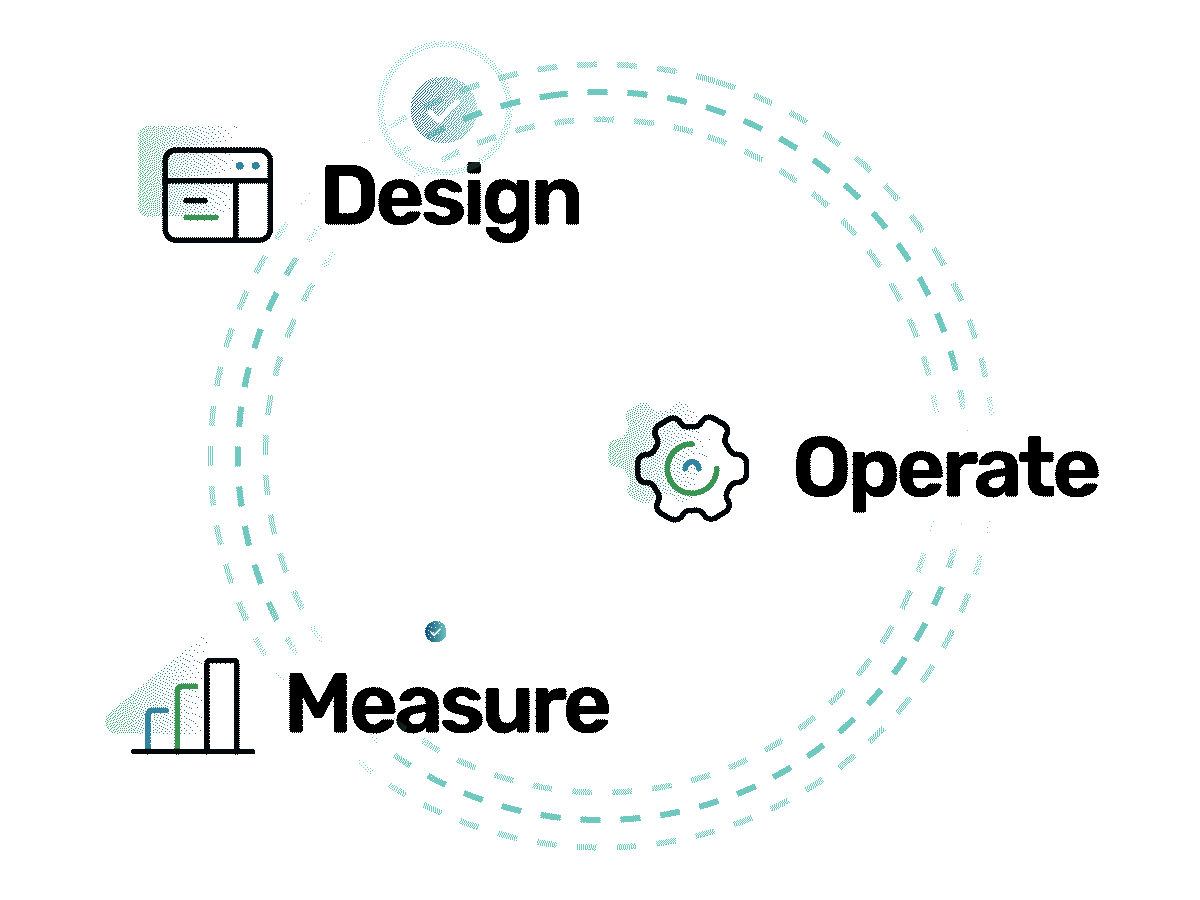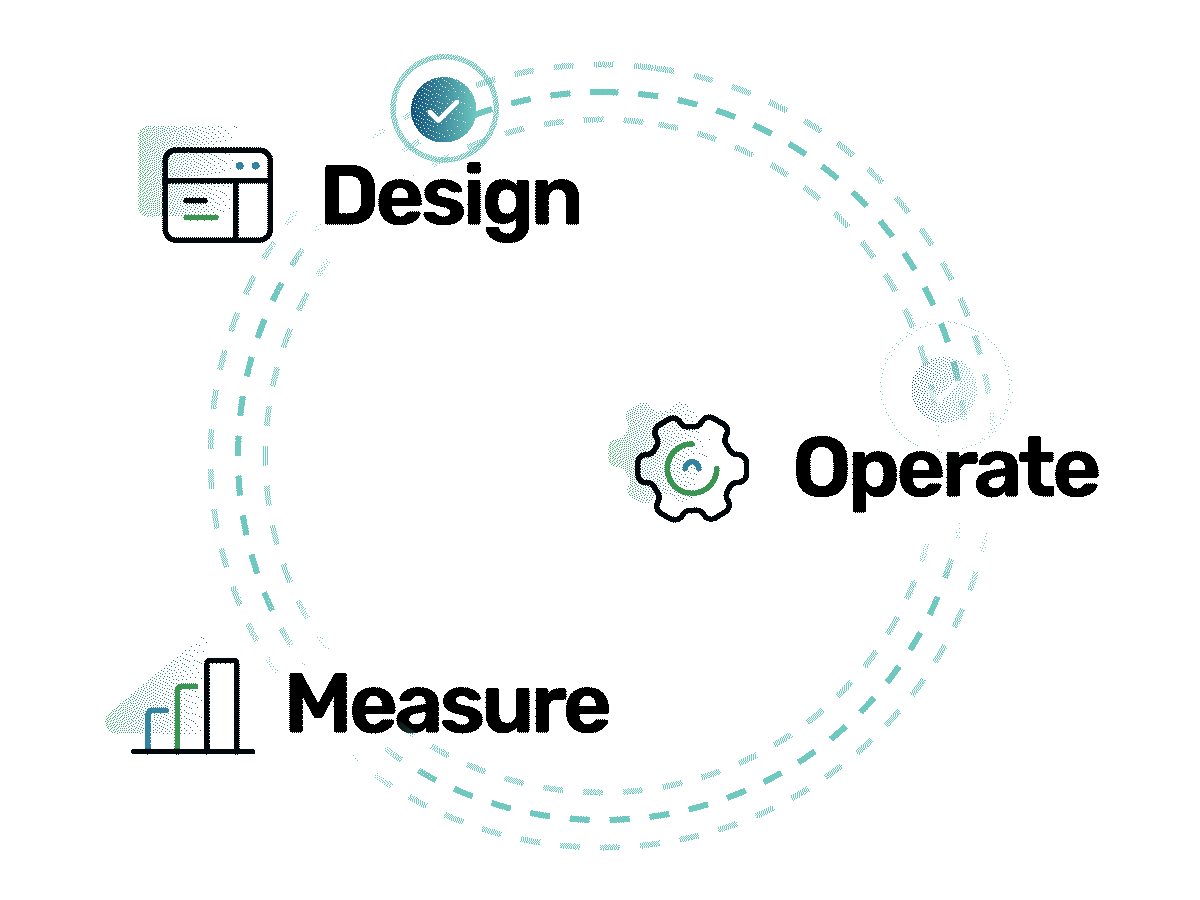
To give you an idea of how these phases work in tandem, consider this example. Let’s say a company has already reached SOC 2 compliance, but it’s interested in expanding to a new market that has other security requirements. The TrustOps team could be simultaneously deciding which security frameworks they need to add and making a strategic plan to start working toward them (design), continuing to collect evidence to prove the efficacy of their existing SOC 2 controls (operate), and evaluating how their SOC 2 compliance report impacted the previous year’s revenue (measure).
The best way to really understand the concept is to dig into the practical aspects of each phase. Let’s get started.
The TrustOps design phase

As we mentioned above, the design phase is when you’ll build your TrustOps strategy. There are three main questions you’ll want to ask yourself to guide your process:
What are my risks?
When considering the risks associated with your business, the first step is to identify the specific threats that exist for your type of business or the data you handle.
Industry-specific threats
Threats can vary greatly depending on your industry, the sensitivity of the data you process, and the digital landscape in which you operate.
For example, a financial services company may face risks related to financial fraud or data breaches, while a healthcare provider might be more concerned with protecting patient privacy and securing health records. Understanding these threats is crucial as they form the foundation of your risk management strategy. It's not just about recognizing the potential dangers, but also about understanding the implications of these threats on your business continuity, reputation, and legal obligations.
Operations and data needs
It's also vital to assess what operations or data capacity is required for the effective delivery of your solution. This involves a deep understanding of what you deliver, its criticality to your customers' success, and how to respond if a breach or disruption occurs. For instance, if your service is integral to your customers' daily operations, any downtime or data loss could have severe consequences. Evaluating the operational requirements and data capacity helps in determining the level of security and resilience needed to protect these assets.
Remember, risks are not just potential threats; they are also opportunities to precisely scope your security measures, enhance resilience, and optimize operational capacity. By clearly understanding your risks, you can tailor your security posture not only to protect against threats but also to ensure that your business can continue to deliver its critical services effectively, even in the face of adverse events.
What are my goals?
Setting clear goals is a fundamental part of establishing a robust TrustOps framework.
Satisfying legal requirements
A primary objective should be understanding and complying with the legal requirements for your target markets. These legal mandates can vary significantly across different regions and industries, encompassing data protection laws like GDPR in Europe or CPRA in California, industry-specific regulations such as HIPAA for healthcare in the United States, or financial regulations like SOX.
Complying with these laws is not just about avoiding penalties; it's about demonstrating to your customers that you are a responsible and trustworthy entity that respects and protects their interests. Your goals should, therefore, include a thorough legal compliance strategy that aligns with the specific demands of the markets you serve, ensuring that all aspects of your operations adhere to these regulatory frameworks.
Meeting industry expectations
In addition to legal compliance, another crucial goal is identifying and acquiring the trust assets that are expected in your target market. Trust assets can include certifications like ISO 27001 for information security management or SOC 2 reports, which attest to the effectiveness of your data security practices. These trust assets serve as tangible proof of your commitment to security and privacy, enhancing your reputation and giving your customers and partners the confidence to do business with you.
The goal here is not just to obtain these trust assets but to understand their relevance and importance in your specific market. By aligning your security and privacy strategies with these expected standards, you can effectively communicate your dedication to trust and security, thereby not only meeting but exceeding the expectations of your target audience.
This strategic approach ensures that your TrustOps goals are aligned with market demands, enhancing your competitive advantage and fostering long-term business relationships.
What are my capabilities?
Understanding your existing capabilities is a critical step in the TrustOps process, as it helps in determining the baseline from which you can build and improve.
Existing policies and procedures
Assessing any documentation that has already been developed to specify your operational expectations is key. This includes a review of existing policies and controls. Existing policies might outline how data is handled and protected, while controls are the specific measures put in place to enforce these policies. Reviewing these can provide insight into the effectiveness of your current security posture and identify areas for enhancement.
Current trust assets
Additionally, looking at prior trust assets achieved, such as certifications or compliance achievements, can give a sense of what has worked well and where improvements can be made. These assets can also serve as a benchmark for future security and compliance efforts.
By thoroughly evaluating these existing elements, you can gain a comprehensive understanding of your current capabilities, which is essential for identifying gaps, planning improvements, and setting realistic and achievable goals for your TrustOps strategy.
How Strike Graph supports the TrustOps design phase
Strike Graph provides a broad range of tools to support the design phase of your TrustOps program. The most powerful is our in-platform risk assessment that makes it simple and fast to identify and rank risks specific to your business context. (Read more about how a risk-based approach to compliance saves time and resources in our ebook.)
Additionally, multi-framework mapping ensures that any existing controls you have in place are automatically mapped to all security frameworks activated in the platform. This gives you an immediate view of where you stand in relation to various industry-specific security frameworks, and how many resources it will take to achieve compliance.
The TrustOps operate phase

Once you’ve identified your risks, understand your business requirements, and have built your TrustOps strategy, you’ll need to start putting actions in place to mitigate your risks and meet your goals. As with the design phase, it’s helpful to understand the operate phase in terms of some key questions your team should be asking itself:
What are my controls?
Controls in TrustOps are pivotal for mitigating the risks identified during the design phase of your TrustOps process. These controls are essentially your frontline defense mechanisms, tailored to address specific vulnerabilities and threats that your business faces. By effectively implementing these controls, you can significantly reduce the likelihood and impact of security incidents, ensuring the continuous integrity, availability, and confidentiality of your data and operations.
Characteristics of controls
Controls should be succinctly stated, combining a thing (asset, process, or resource) and an activity (action or procedure) to form a clear directive.
Example 1: Laptops will have anti-malware software installed.
This control targets a specific asset (laptops) and prescribes a clear action (installation of anti-malware software).
Example 2: Production cloud environments will require encrypted communications of TLS 1.3 or greater.
Here, the focus is on securing a particular environment (production cloud) with a specified security measure (encrypted communications using TLS 1.3 or higher).
Example 3: The IT department will maintain a disaster recovery plan.
This control assigns responsibility to a specific department (IT) to undertake an essential activity (maintaining a disaster recovery plan).
Defining an effective control
An effective control in TrustOps must exhibit several key characteristics. It must be
Assignable: It is crucial to clearly identify who is responsible for each control. This assignment ensures accountability and makes it possible to track compliance and effectiveness. For instance, specifying that the IT department is responsible for implementing and monitoring anti-malware software on all laptops.
Testable: A control should be verifiable. This means defining what data or evidence is required to prove that the control is being effectively operated. For example, logs or reports that show the status of anti-malware software on all company laptops.
Mappable: Each control should be related to common measuring tools or standards, ensuring that it aligns with broader security frameworks and compliance requirements. This aspect involves evaluating whether the control is well-written, appropriately mapped to compliance standards, and whether evidence is provided as per established schedules.
Who is accountable?
A fundamental aspect of TrustOps is establishing clear accountability for each control. This step is crucial for ensuring that the security and compliance measures you implement are not just theoretical but are actively managed and enforced.
Assigning responsibility
The first step in assigning responsibility is to identify who, specifically, is accountable for each control. This could be an individual, a team, or a department, depending on the nature of the control. For instance, the IT department may be responsible for ensuring that all laptops have up-to-date anti-malware software, while the HR department might be accountable for ensuring that employees are aware of and comply with data privacy policies.
Once responsibilities are assigned, it’s vital to have a transparent system in place for sharing this information. This can involve internal documentation, regular meetings, or digital dashboards that track control implementation and compliance. Transparency ensures that everyone in the organization understands their roles and responsibilities, and it also fosters a culture of accountability, which is integral to the success of your TrustOps strategy.
Validating control operation
The adage “trust but verify” is a cornerstone in the realm of accountability in TrustOps. While it's important to trust your team to implement and manage controls, it's equally important to have mechanisms in place to verify that these controls are operating as intended.
Identifying what data or evidence can validate control operation is essential. This could include system logs, audit trails, compliance reports, or performance metrics. For example, to validate the operation of anti-malware controls on laptops, you might use software that reports on the installation and update status of anti-malware programs across all company devices.
What do I monitor?
Controls can’t just be created and then forgotten, they need to be monitored to verify the supply of evidence, assess the quality of the control statements, and ensure that controls are appropriately mapped to your organization's needs and compliance standards.
Evidence supply and scheduling
A critical part of monitoring involves checking if evidence supporting the operation of controls has been supplied according to the established schedule. This could involve routine checks of logs, reports, and other documentation that serve as proof of control effectiveness. For example, ensuring that reports showing the successful implementation of security patches across your network are delivered and reviewed at predetermined intervals. Regular monitoring of evidence helps in timely identification of lapses or inefficiencies in control operation.
Control quality assessment
Another vital aspect to monitor is the quality of the control statements themselves. Is the control well written? A well-written control is specific, clear, and actionable. It should leave no room for ambiguity regarding what is required, by whom, and within what timeframe. For instance, a control stating “Regular security training for all employees” is less effective than one that specifies “Quarterly cybersecurity training sessions for all employees, with attendance and completion tracked and reported.” Regularly reviewing and refining the wording of your controls can significantly enhance their effectiveness and enforceability.
Control mapping
Lastly, monitoring must include verification that each control is appropriately mapped. This means ensuring that the controls are correctly aligned with the broader security frameworks and compliance standards relevant to your organization. Proper control mapping not only facilitates compliance but also ensures that controls are comprehensive and address all pertinent areas of risk and regulation. For example, if your organization needs to comply with GDPR, your controls related to data privacy and protection should be clearly mapped to the relevant GDPR articles and requirements.
How Strike Graph supports the TrustOps operate phase
The operate phase is where TrustOps can start to get more complicated — from juggling multiple security frameworks, to gathering mountains of evidence, to managing the journey toward certification, there’s a lot to keep in the air. Strike Graph is designed to tame this chaos, leveraging AI and automation to handle repetitive tasks and giving you insight into your progress with our intuitive dashboards.
 AI security assistant: Strike Graph's AI security assistant provides quick, accurate information on your company’s security policies and procedures, sourced directly from your documentation within the platform. And, your data remains completely secure because the AI security assistant doesn’t use open AI models like ChatGPT.
AI security assistant: Strike Graph's AI security assistant provides quick, accurate information on your company’s security policies and procedures, sourced directly from your documentation within the platform. And, your data remains completely secure because the AI security assistant doesn’t use open AI models like ChatGPT.
 Audit-proven controls: Strike Graph pre-populates the platform with tried and true controls for the frameworks you’ve selected. Use them out of the box, or customize them to reflect your company’s unique risk profile.
Audit-proven controls: Strike Graph pre-populates the platform with tried and true controls for the frameworks you’ve selected. Use them out of the box, or customize them to reflect your company’s unique risk profile.
 Multi-framework control mapping: Strike Graph's platform streamlines compliance by automatically mapping controls to security frameworks activated in the platform, significantly reducing manual effort. This feature enables you to effortlessly align controls with multiple frameworks like ISO 27701, SOC 2, and PCI DSS so you only have to do the work once.
Multi-framework control mapping: Strike Graph's platform streamlines compliance by automatically mapping controls to security frameworks activated in the platform, significantly reducing manual effort. This feature enables you to effortlessly align controls with multiple frameworks like ISO 27701, SOC 2, and PCI DSS so you only have to do the work once.
 Evidence notifications: Helpful notifications let you know when the evidence is about to expire so you can keep your brain power (and calendar) free for more important tasks and also ensure your evidence is always up to date.
Evidence notifications: Helpful notifications let you know when the evidence is about to expire so you can keep your brain power (and calendar) free for more important tasks and also ensure your evidence is always up to date.
 Control monitoring feature: Strike Graph’s control monitoring feature allows you to check when controls were last modified and by whom so you know at a glance your risks are covered.
Control monitoring feature: Strike Graph’s control monitoring feature allows you to check when controls were last modified and by whom so you know at a glance your risks are covered.
 Policy templates: Our library of policy templates ranging from privacy to InfoSec saves the time you would otherwise spend writing documentation from scratch.
Policy templates: Our library of policy templates ranging from privacy to InfoSec saves the time you would otherwise spend writing documentation from scratch.
 Resource library: Strike Graph’s extensive education resource library and in-platform educational tips give you practical guidance \and in-depth knowledge when you need it. And, our team of TrustOps experts is available if you need a little extra support along the way.
Resource library: Strike Graph’s extensive education resource library and in-platform educational tips give you practical guidance \and in-depth knowledge when you need it. And, our team of TrustOps experts is available if you need a little extra support along the way.
Measure
The measure phase provides proof that your company is effectively protecting customer data and privacy, thus building trust. This phase may have an aura of finality to it, but in actuality, companies should be constantly measuring their TrustOps programs. Let’s first look at the most obvious form of measurement — external security compliance audits and certifications — then we’ll move on to more broader types of measurement that should be ongoing.
External security compliance audits and certifications
External security compliance audits are a critical aspect of establishing and maintaining trust in your business. These audits provide your company with valuable trust assets, such as security compliance reports and certifications, that provide proof of your company's commitment to security, growing customer trust, and opening the way to new business opportunities — which in turn, boost your company’s revenue.
Internal evaluation
Internal evaluations play a pivotal role in ensuring the effectiveness and adaptability of your TrustOps program. Conducting these processes allows an organization to critically analyze its current TrustOps posture, identify areas for improvement, and align its operations with the evolving data security and privacy demands. This continuous scrutiny and adjustment are what make TrustOps a proactive and effective approach to building and maintaining trust within an organization.
Identifying remaining gaps
A primary objective of internal evaluations is to uncover any remaining (or new) unmitigated risks or unmet standards that could compromise the effectiveness of the TrustOps program. By regularly assessing these areas, organizations can ensure that their TrustOps strategy remains robust and responsive to evolving threats and regulatory requirements.
Evaluating progress toward goals
Another critical aspect of the measure phase is evaluating whether the organization is on track to meet the objectives outlined in its TrustOps plan. This involves assessing the implementation and efficacy of controls and evidence collection against the established timeline and goals. Regular evaluations help in maintaining alignment with the TrustOps strategy, ensuring that the organization not only meets its current security and trust obligations but also positions itself for future success and resilience.
Assessing revenue impact
What sets TrustOps apart is that it explicitly ties security efforts to revenue (via trust building). Assessing your TrustOps program’s revenue impact is assessing the success of your TrustOps program. You’ll want to look at concrete numbers, and you’ll also want to evaluate how effectively you’re leveraging trust assets to set yourself up for even greater future TrustOps success.
Tracking revenue increases
Tracking the revenue impact of your TrustOps program involves closely monitoring key performance indicators (KPIs) that link your security and trust initiatives to business growth. This tracking should focus on metrics such as new customer acquisition, customer retention rates, and market share expansion post-implementation of TrustOps.
By correlating these financial metrics with the timing and nature of your TrustOps activities, you can gain insights into how effectively TrustOps initiatives are translating into tangible business benefits. Regular analysis of these KPIs helps in fine-tuning your TrustOps strategy to maximize its contribution to your organization's revenue growth.
Trust assets
Tracking the current impact of your TrustOps program is crucial, and so is maximizing the potential ROI of your TrustOps program by evaluating whether you’re leveraging your trust assets as effectively as possible.
First, you’ll want to assess if you’ve attained the expected third-party assessments or certifications in your target market. These assessments validate your security and compliance measures, serving as a benchmark for trust and reliability in the eyes of potential customers.
Assuming you’ve achieved the appropriate trust assets, you’ll also want to evaluate if you’re effectively communicating and marketing these accomplishments. A strong TrustOps marketing plan involves crafting messages that highlight your TrustOps achievements and integrate them into your marketing and sales strategies to attract and retain customers.
Finally, in order for a TrustOps program to maximize its ROI, your whole team needs to understand and utilize the trust assets you've achieved. Assessing whether all team members have adequate knowledge of and access to your trust assets sets you up to create a culture of security within your organization and also ensure that every team member can effectively communicate these achievements to customers and stakeholders.
How Strike Graph supports the TrustOps measurement phase
If there’s an area where emerging technology is poised to totally change the landscape — security and TrustOps measurement is it. Traditionally, auditing and evaluating your risk-mitigation activities required expensive, slow auditing firms and other third-party security consultants. Strike Graph has changed that.
Our suite of AI-powered tools and strategic automation drastically cut the time and cost of evaluating your TrustOps activities and obtaining valuable trust assets while giving you real-time reporting that just wasn’t possible before.
 AI-powered audits: Strike Graph’s tech-enabled audits are faster and more efficient than traditional methods. Seamless integration provides transparent, verifiable testing results that are understandable for the entire team.
AI-powered audits: Strike Graph’s tech-enabled audits are faster and more efficient than traditional methods. Seamless integration provides transparent, verifiable testing results that are understandable for the entire team.
 Intuitive dashboard: Our dashboard provides leadership with a bird’s eye view of your TrustOps program for easy continuous evaluation and monitoring.
Intuitive dashboard: Our dashboard provides leadership with a bird’s eye view of your TrustOps program for easy continuous evaluation and monitoring.
 Vulnerability scanning and penetration testing: Feel confident your security safeguards are working with our pen tests that simulate real-world attacks that hackers use to gain access to your organization’s network and vulnerability scans to test your network for common vulnerabilities.
Vulnerability scanning and penetration testing: Feel confident your security safeguards are working with our pen tests that simulate real-world attacks that hackers use to gain access to your organization’s network and vulnerability scans to test your network for common vulnerabilities.
 Security questionnaire: Our AI-powered security questionnaire uses your existing controls to answer each security question. No need to spend countless hours completing security questionnaires for each prospect.
Security questionnaire: Our AI-powered security questionnaire uses your existing controls to answer each security question. No need to spend countless hours completing security questionnaires for each prospect.
 Trust asset library: Strike Graph’s trust asset library consolidates all of your company’s trust assets in one central location, allowing you to more easily organize and share them with customers, partners, team, and stakeholders.
Trust asset library: Strike Graph’s trust asset library consolidates all of your company’s trust assets in one central location, allowing you to more easily organize and share them with customers, partners, team, and stakeholders.
Security overview: Strike Graph’s security overview is a real-time snapshot of your security posture. Use it to build trust with customers between certifications and to maintain transparency with partners and stakeholders.
Coming soon | Audit prediction: Watch your audit prediction score rise as you implement controls and attach evidence. When it’s at 100%, you can enter your audit knowing you’ll pass. Guaranteed success with zero stress.
Design-operate-measure for enterprise companies with multiple products
The design-operate-measure TrustOps model is a versatile approach that works for companies of all sizes, including large enterprise companies with multiple products. That said, when adapting this model for enterprise-scale operations, there are additional considerations you should take to ensure its effectiveness across diverse product lines.
In the following section, we’ll explore the dos and don'ts for enterprise companies when implementing a TrustOps program, providing insights into how to tailor this model to meet the unique challenges and complexities of managing security and trust in a multi-product environment.
What not to do: top-down security management
Traditionally, enterprises have often adopted a top-down approach to security, but this method has its challenges, especially in complex organizational structures. The reality is that this approach doesn’t work well when your goal is to build trust holistically across the organization. Here’s why (and a better way to tackle enterprise TrustOps).
Top-down security management in complex enterprises
Traditionally, top-down security management involves centralized security teams dictating practices across diverse business units. This model, while seemingly efficient, often fails to address the unique security needs of each division within a complex enterprise structure. It also tends to overlook the nuanced understanding of risks and operations at the divisional level, leading to a one-size-fits-all approach that isn’t always effective.
Emergence of shadow non-security practices
The rigidity and generalization of the top-down approach often leads business leaders and divisions to develop their own shadow practices to circumvent overly restrictive security measures. These unofficial practices are usually aimed at speeding up processes but lack the comprehensive security oversight necessary to protect the organization adequately.
Consequences of ignored security measures
The downside of these shadow practices becomes starkly evident in high-profile security breaches, such as the Solar Winds and the Colonial Pipeline company incidents. These incidents serve as a cautionary tale about the pitfalls of a top-down security approach in complex enterprises, where the need for speed can sometimes overshadow the importance of robust security protocols.
The right way to do enterprise TrustOps — federated security
Adopting a federated approach to TrustOps in enterprise environments aligns security practices more effectively with the diverse needs of various divisions. This approach decentralizes the responsibility for security, tailoring it to the specific requirements of each business unit.
Division-specific analysis
Each division is evaluated for its unique business outcomes, risks, and security opportunities. This tailored analysis ensures that security measures are directly relevant to the specific operational context of each division.
Corporate leadership role
In a federated security model, divisions collaborate with corporate security leaders to identify and take ownership of crucial security compliance achievements.
Corporate security leaders play a crucial role in harmonizing security practices across divisions. They should set clear goals and objectives for each division's security practice. This typically involves utilizing frameworks like SOC 2 or a subset of the NIST framework to establish broad security expectations.
Some of these security measures will need to be managed broadly across all divisions and should be overseen by corporate leadership. For example, corporate HR might manage acceptable use policies for all divisions, providing a consistent baseline.
Division leadership role
On the other hand, division leaders ensure that security measures are appropriate and effective for each division's needs. This includes obtaining relevant certifications that are critical to their target market and other more granular security measures, like software change management, that require specialized attention to the unique technological needs of a division.
Division leaders should work closely with corporate leadership to create a TrustOps methodology tailored to the division’s needs that also adheres to the umbrella organizational security expectations.
Evaluation and monitoring
It’s crucial to monitor each division’s progress and foster a culture of accountability and security awareness across the organization. Corporate leadership should keep divisions informed about the evolving risk landscape and then collaborate with division leaders to adjust divisional security practices as needed.

That’s a lot of work. What’s the ROI?
Investing in TrustOps, particularly for enterprise companies, yields a significant return on investment primarily through increased revenue. The equation is this. TrustOps → trust → revenue.
How TrustOps creates customer trust
By integrating activities like IT security, risk management, and data privacy practices, TrustOps demonstrates a company's competence in handling sensitive data and maintaining robust security practices. This operational excellence, reflected through acquired trust assets like certifications, showcases a company's integrity and commitment to ethical data stewardship. These elements are foundational in earning customer and stakeholder trust, particularly in an age of growing customer awareness of data and privacy vulnerability.
How trust leads to revenue increases
The trust established by effective TrustOps practices directly translates into enhanced market position and revenue growth for a company by expanding business opportunities and strengthening customer relationships.
Customers who trust a company are more likely to make repeat purchases and remain loyal, even in challenging situations like data breaches. Trust also attracts new customers, as it is a crucial factor in purchasing decisions, especially in industries where data security is paramount.
Additionally, trust makes a company more appealing to investors and partners, opening up new business opportunities. Enterprises known for robust TrustOps practices are preferred for their reliability, leading to more lucrative deals and collaborations.
Maximize ROI with the right TrustOps tools
The key to maximizing the return on investment in TrustOps lies in achieving efficiency while maintaining robustness. The key to reaching this balance between robustness and resource use is choosing a comprehensive TrustOps platform like Strike Graph.
Strike Graph leverages strategic AI and automation alongside risk-based planning to streamline the TrustOps process, enhancing efficiency. And, Strike Graph is tailored to convert security measures into revenue through trust assets via features like our trust asset library and tech-enabled audits.
Start your TrustOps journey
Embarking on the TrustOps journey transforms how a business approaches security and trust. TrustOps, with its comprehensive strategy that spans all organizational facets, elevates both security posture and customer trust. The process of designing, operating, and measuring in TrustOps is a pathway to not just safeguarding data but also enhancing customer relationships and market presence.
To say it simply: TrustOps turns security measures into a lever for revenue growth and ongoing business success.
And Strike Graph’s design, operate, measure approach is the way to do TrustOps most efficiently and effectively.
Our team of TrustOps experts are eager to show you how Strike Graph’s comprehensive TrustOps platform can support your company’s journey. Schedule a demo to get started. Or, take a spin around Strike Graph yourself by registering for your free account.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)








