Understand how CMMC and FedRAMP fundamentally differ despite surface similarities. Experts debunk misconceptions and clarify who needs which framework. Download a free control map for each framework to sharpen your compliance efforts.
What are CMMC and FedRAMP?
CMMC and FedRAMP are government compliance frameworks that set cybersecurity requirements to protect sensitive federal data. At first glance, they may seem similar, but in practice, they apply to very different organizations with distinct compliance scopes. CMMC governs defense contractors, while FedRAMP covers cloud service providers working with federal agencies.
Both frameworks draw on standards developed by the National Institute of Standards and Technology (NIST). CMMC is based on NIST 800-171 and NIST 800-172, while FedRAMP builds on NIST 800-53. Each establishes requirements for safeguarding Federal Contract Information (FCI) and Controlled Unclassified Information (CUI), though they approach the task in different ways.
CMMC, or Cybersecurity Maturity Model Certification, is required for any defense contractor bidding on contracts where they will store, process, or transmit FCI or CUI. As Ashley Lex, Client Success Manager for Security & Compliance Services at Aprio, explains, “CMMC is a corporate-level certification that demonstrates an organization’s ability to protect Controlled Unclassified Information (CUI). CMMC requirements apply anywhere CUI exists inside the environment of an organization seeking assessment (OSA) — cloud, non-cloud, or on-premises — and to the people who have access to it. It ensures processes and procedures are in place to protect the CUI.”
Lex is part of Aprio’s Federal Certification Team, which helps DIB organizations of all sizes navigate both CMMC and FedRAMP compliance.

By contrast, FedRAMP, the Federal Risk and Authorization Management Program, is a government-wide program run by the General Services Administration (GSA). It applies specifically to cloud service providers (CSPs) and ensures their systems meet federal security requirements for cloud environments.
“In the simplest terms,” Lex says, “the purpose of FedRAMP is to protect federal data stored or processed in cloud environments. If you want to provide cloud services to federal agencies, you need to get FedRAMP.”
Authorized providers are listed on the FedRAMP Marketplace, which agencies use to find approved vendors. For organizations that serve both civilian and defense programs — or CSPs considering federal contracts — understanding the differences between CMMC and FedRAMP is essential.
How do CMMC and FedRAMP compare?
CMMC and FedRAMP share a similar purpose of keeping government data safe. However, CMMC is specific to the Department of Defense, and FedRAMP is for all federal agencies, including the DoD. FedRAMP has many more security controls, so the assessment is usually longer and the process might be more expensive.
 “CMMC and FedRAMP target very different types of organizations,” explains Elliott Harnagel, Product and Compliance Strategist at Strike Graph. “CMMC applies to anyone in the Defense Industrial Base — it could be a software company, but also a bolt manufacturer in Kansas supplying a defense mission. The DoD wants to protect its information, but it also recognizes that many of these companies aren’t highly technical. FedRAMP, by contrast, is for cloud service providers. These are high-tech companies, and the rules are much more stringent to reflect that.”
“CMMC and FedRAMP target very different types of organizations,” explains Elliott Harnagel, Product and Compliance Strategist at Strike Graph. “CMMC applies to anyone in the Defense Industrial Base — it could be a software company, but also a bolt manufacturer in Kansas supplying a defense mission. The DoD wants to protect its information, but it also recognizes that many of these companies aren’t highly technical. FedRAMP, by contrast, is for cloud service providers. These are high-tech companies, and the rules are much more stringent to reflect that.”
He continues, offering a high-level comparison: “CMMC is a challenging process, but it has far fewer controls and less ongoing monitoring than FedRAMP. For example, CMMC Level 2 has 110 controls, while FedRAMP Moderate has about 330. As a result, FedRAMP is usually harder to implement, more expensive, and requires a longer assessment.”

Is there reciprocity between FedRAMP and CMMC?
No, there isn’t reciprocity between FedRAMP and CMMC. Both have similar cybersecurity guidelines, but they serve different types of contractors. Even though some of the security rules overlap, having certification in one does not automatically count for the other.
The reciprocity question remains a source of confusion for some.
“FedRAMP’s security controls come directly from NIST 800-53, a government standard that defines cybersecurity practices, while CMMC comes from another NIST document (800-171), which is essentially a pared-down version of FedRAMP’s requirements,” explains Harnagel. “Still, the idea that efforts in one directly translate to the other is a misconception. Even though CMMC builds on FedRAMP, achieving compliance with both frameworks is a separate effort — there is no one-to-one reciprocity.”
FedRAMP vs. CMMC
| |
FedRAMP
|
CMMC
|
|
Purpose
|
Sets standardized cybersecurity standards for all cloud services that federal agencies use to store their data.
|
Ensures that contractors in the Defense Industrial Base (DIB) implement cybersecurity practices that protect CUI and FCI wherever it appears in their system.
|
|
Who must comply
|
Cloud service providers that provide a CSO (cloud service offering) to federal agencies.
|
Defense Industrial Base (DIB) contractors and subcontractors that handle, process, or transmit any CUI or FCI as part of a DoD contract
|
|
Scope (system boundary)
|
The specific CSO (cloud service offering) that stores federal information
|
Any person, system, or component within the contractor’s environment that stores, processes, or transmits CUI or FCI.
|
|
Levels
|
Three impact baselines defined by the impact of a data breach to the government mission
|
Three maturity levels defined by the type of DoD data the organization will handle
- Level 1: FCI
- Level 2: CUI
- Level 3: CUI for critical missions
|
|
NIST requirement
|
NIST SP 800-53 controls
- Low: ~125 controls
- Moderate: ~325 controls
- High: ~421 controls
|
NIST SP 800-171
- Level 1: 15 practices (based on FAR 52.204-21)
- Level 2: 110 practices (NIST SP 800-171)
- Level 3: 130+ controls (NIST 800-171 and NIST 800-172)
|
|
Assessment type
|
Third-party assessment by a 3PAO
|
Depends on the level
- Level 1: self-assessment
- Level 2: Third-party certification by C3PAO
- Level 3: DIBCAC assessment
|
|
Assessment frequency
|
Initial authorization against all baseline controls
Annual assessment of a subset of the controls penetration test by external assessor,
Continuous monitoring and reporting
|
Level 1: annual self-assessment
Level 2 and 3: External assessment every three years (and annual company affirmation of compliance)
|
Do I need FedRAMP, CMMC, or both?
Whether you need FedRAMP, CMMC, or both depends on your services and the agencies you support. Defense contractors that don’t provide cloud services need CMMC. Cloud providers need FedRAMP to store federal data. A cloud provider handling defense data inside and outside their cloud may need both, but that’s rare.
Here's a breakdown of which types of organizations need CMMC, FedRAMP, or, in rare cases, both.
- CMMC: CMMC applies to any contractor that wants to bid on DoD contracts where they will handle, process, or transmit DoD Federal Contract Information (FCI) or Controlled Unclassified Information (CUI), and will need CMMC certification. The DoD makes CMMC requirements clear by adding them in the DFARS clause of any contract.
- FedRAMP: FedRAMP applies to cloud service providers that offer cloud software to a federal agency. Any CSP that wants to sell their services to a federal agency needs FedRAMP authorization at the appropriate level.
- CMMC and FedRAMP: If a CSP will handle CUI or FCI for a DoD project, you may need to meet both FedRAMP and CMMC standards — but that doesn’t always mean going through both certification processes.
For example, a DoD contractor needs CMMC Level 2 to handle CUI. If that contractor wants to use a cloud service to store the data, the CSP must be FedRAMP Moderate (or equivalent). The contractor pursues CMMC, while the CSP pursues FedRAMP. The CSP does not need its own CMMC certification. It’s rare for a single company to need both certifications, simply because most cloud service providers don’t host defense data outside their platforms, and most defense contractors contract out their cloud services rather than operating their own.
Still, the situation can happen.
“The type of data FedRAMP is protecting and how it is protecting is ultimately different than the type of data CMMC is protecting,” says Lex. “The only situation where an entity needs both is the situation where a defense contractor is also the cloud service provider. For example, an organization might have a CMMC clause in a defense contract and have to handle CUI outside of the cloud, but also have a cloud services branch that needs FedRAMP for other reasons.”
She continues, saying, “It’s extremely difficult to put a hard line on it. The black and white of it is, if you have a CMMC DFARs clause in your contract, , you will be expected to become CMMC compliant by law, regardless of what type of business you do.”
Lex offers some clarity on the situation for organizations that aren’t sure whether to pursue both: “If I were a CSP and I was struggling to determine whether I needed CMMC, I would first determine if any of my contracts contain DFARS 7012, which triggers CMMC. Next, I would determine if ALL the CUI I process is in fact contained within my cloud solution. If both are the case, then pursue FedRAMP authorization or equivalency, as well as perform a self-assessment to attest to CMMC Level 1 compliance for my corporate infrastructure that processes FCI. I would also consider having a C3PAO validate my self-assessment and my CUI and FCI data flows.
Similarities between CMMC and FedRAMP
CMMC and FedRAMP have much in common despite their core differences. Both set cybersecurity standards between the U.S. government and contractors. Both use a three-level certification system. They are also based on similar NIST standards.
Here's a breakdown of the key areas where CMMC and FedRAMP overlap:
- Foundational NIST standards
CMMC draws on NIST 800-171, which is itself a subset of NIST 800-53 — the same standard FedRAMP is based on. Because of this common foundation, there is significant overlap between the two frameworks, even though they apply in different contexts.
- Certification model
CMMC and FedRAMP both have a three-tier certification system. Higher levels require stricter security controls, while lower levels apply to less sensitive information and have fewer requirements to meet.
Lex notes that each framework defines its tiers using different criteria, but both rely on some measure of data sensitivity and criticality.
“CMMC has three levels that are based on whether you handle FCI or CUI, and what type of CUI,” Lex says. “Whereas the FedRAMP level depends on your data type and what the relative impact (“low,” “medium,” or “high”) would be if your security failed and the data was compromised.”
- Similar assessment structure
Both programs require third-party assessments, except CMMC Level 1 (and select Level 2 contracts), where contractors complete a self-assessment. Each program has its own assessor:
-
- For CMMC: Certified Third-Party Assessment Organizations (C3PAOs) conduct CMMC Level 2 assessments, the most common CMMC level. The Cyber AB approves C3PAOs. A government assessor from the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) performs assessments for CMMC Level 3, which applies to only a few major contractors.
- The FedRAMP Project Management Office (PMO) approves 3PAOs (Third-Party Assessment Organizations) to assess cloud service providers for FedRAMP compliance.
Differences between CMMC and FedRAMP
CMMC and FedRAMP fundamentally differ in scope, requirements, and certification approach. CMMC applies to any part of an organization that handles DoD data. FedRAMP applies to a cloud service offering (CSO) that stores federal data. FedRAMP includes more security controls than CMMC and is usually more costly and time-intensive.
Here's a breakdown of the key differences between CMMC and FedRAMP:
- Purpose & Scope:
- FedRAMP creates a standardized security framework for any cloud service the federal government uses. It applies to all cloud service providers (CSPs) that want to sell to federal agencies.
- CMMC is a DoD-specific certification that requires defense contractors in the Defense Industrial Base to protect Controlled Unclassified Information (CUI). It applies to any system or individual handling DoD data, not just cloud services.
- Standards and control set:
- FedRAMP’s cybersecurity requirements come from NIST SP 800-53. They require hundreds of technical and cloud-specific security controls. While FedRAMP overlaps with some CMMC practices, it requires significantly more controls and is more technically rigorous.
- CMMC’s requirements come from NIST SP 800-171 (some from 800-172 for CMMC Level 3). CMMC requires far fewer controls.
- Compliance Process:
- FedRAMP:
FedRAMP’s assessment structure and monitoring requirements are more rigorous than CMMC’s, and unlike CMMC, the assessment structure does not vary by certification level.
- Sponsorship:
To pursue FedRAMP authorization, there are two paths: Agency sponsorship or a Joint Authorization Board (JAB). An agency sponsorship means a federal agency that wants to use a cloud service “sponsors” an organization. They work with the organization through the FedRAMP process, review your security package, and, if the organization becomes FedRAMP authorized, eventually grant an Authorization to Operate (ATO) within their agency. On the other hand, a Joint Authorization Board is made up of the CIOs of the Department of Homeland Security (DHS), DoD, and the General Services Administration (GSA). They review and authorize a limited number of high-impact popular cloud services each year. JAB authorization is harder to get but carries more weight because it allows any federal agency to use the cloud service, not just a single sponsoring agency.
-
-
- Initial assessment: FedRAMP compliance starts with an initial assessment, or a full security assessment against all baseline controls by an accredited Third-Party Assessment Organization (3PAO).
-
-
- Annual assessment: Each year, a 3PAO assesses a subset of the FedRAMP controls for the organization’s given impact level.
-
-
- Continuous monitoring: After authorization, the CSP performs monthly vulnerability scans and does other monitoring activities that they must submit to the FedRAMP Program Management Office (PMO) and the authorizing agency. They submit documentation, such as scan results, Plan of Action & Milestones (POA&Ms), and other relevant documents. Agency officials (AOs) track compliance and can suspend or revoke authorization.
-
- CMMC:
The CMMC audit process varies by level, but it’s generally less demanding than FedRAMP’s process.
- CMMC Level 1: Contractors complete an annual self-assessment and submit their results to the Supplier Performance Risk System (SPRS).
-
-
- CMMC Level 2: Almost all Level 2 Contractors must receive an assessment from a Certified Third-Party Assessor Organization (C3PAO) every three years, against all 110 security controls. Each year, the contractor submits an annual self-affirmation of compliance that they submit to SPRS. For some Level 2 contracts, the DoD only requires an annual self-assessment against the 110 security controls, along with the annual self-affirmation.
-
-
- CMMC Level 3: Level 3 contractors must undergo a government-led assessment from the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) every three years. They must also submit an annual self-affirmation of compliance to SPRS.
How do CMMC levels relate to FedRAMP impact baselines?
CMMC and FedRAMP each have three tiers, with stricter requirements at higher levels. But the requirements for each level don’t directly align across frameworks. CMMC bases its levels on the type of data a contractor handles, while FedRAMP has “impact baselines” that reflect the potential mission impact if there were a data breach.
At a high level, CMMC defines its levels based on the type of data an organization will handle as part of a defense contract, Federal Contract Information (FCI) or Controlled Unclassified Information (CUI), and the degree of cybersecurity maturity the DoD requires to protect this data. The DoD specifies the CMMC maturity level in the Defense Federal Acquisition Regulation Supplement (DFARS) of a defense contract.
In contrast, FedRAMP defines its impact baselines by the potential impact of a security breach on three “axes” of concern: confidentiality, integrity, and availability of the data. FedRAMP derives these levels from the Federal Information Processing Standards Publication (FIPS) 199, Standards for Security Categorization of Federal Information and Information Systems.
To determine the appropriate FedRAMP level, a cloud service provider must evaluate each type of data it stores and assess the impact a breach would have on confidentiality, integrity, and availability. FedRAMP then considers the combined impact across these axes when assigning a particular level.
Comparing CMMC Level 1 vs. FedRAMP Low
CMMC Level 1 and FedRAMP Low both represent baseline requirements, but they differ significantly. CMMC Level 1 requires 15 controls with a self-assessment. FedRAMP Low requires 125 controls and an independent third-party assessment.
Here's a direct comparison of CMMC Level 1 vs. FedRAMP Low:
- Definition and scope
- CMMC Level 1: For DoD contractors that only handle, process, or transmit Federal Contract Information (FCI).
- FedRAMP Low: Appropriate for where a breach would only have very limited effects on the confidentiality, integrity, or availability of the data. “FedRAMP Low is usually just about protecting basic information like emails and passwords,” says Harnagel.
- Control set and requirements
- CMMC Level 1: 15 “basic safeguarding requirements” from FAR 52.204-21
- FedRAMP Low: 125 security controls from NIST SP 800-53
- Assessment
- CMMC Level 1: Annual self-assessment from the organization seeking compliance
- FedRAMP Low: Applies to cloud service offerings (CSOs) where the impact of a breach would cause “low” impacts to the mission.
Comparing CMMC Level 2 vs. FedRAMP Moderate
CMMC Level 2 and FedRAMP Moderate are “mid-tier” in their frameworks, but they’re not equivalent. Level 2 requires 110 controls and a third-party assessment. FedRAMP Moderate requires 325 controls, a third-party assessment, and continuous monitoring.
Here’s a direct comparison of CMMC Level 2 with FedRAMP Moderate:
- Definition and scope
- CMMC Level 2: For DoD contractors that handle, process, or transmit Controlled Unclassified Information (CUI). This is the most common level for organizations in the Defense Industrial Base.
-
- FedRAMP Moderate: This level applies to cloud service offerings (CSOs) where a breach could have serious adverse effects on confidentiality, integrity, or availability of federal data.
- Control set and requirements
- CMMC Level 2: 110 practices from NIST SP 800-171.
- FedRAMP Moderate: 325 security controls from NIST SP 800-53.
-
- CMMC Level 2: Requires a C3PAO assessment every three years, with annual self-affirmations from the organization in between formal audits.
-
- FedRAMP Moderate: Requires an initial authorization from a 3PAO against all security controls. Then, annual assessments are conducted on a subset of controls, and the organization conducts continuous monitoring.
- Equivalency Note
Sometimes, DoD contractors want to store their data in a cloud that isn’t FedRAMP-authorized. In the FedRAMP Moderate Equivalency Memo, the DoD stated that they would allow defense contractors to use certain CSPs that don’t have full FedRAMP Moderate authorization, but can demonstrate an “equivalent” level of cybersecurity.
Comparing CMMC Level 3 vs. FedRAMP High
CMMC Level 3 and FedRAMP High are the most demanding levels in their frameworks. CMMC Level 3 requires 130 controls and applies to contractors handling critical CUI. FedRAMP High requires around 421 controls and applies to a cloud where breaches could severely impact federal services or missions.
Here’s a direct comparison of CMMC Level 3 with FedRAMP High:
- Definition and scope:
- CMMC Level 3:
CMMC Level 3 applies to contractors handling critical CUI related to very important DoD missions. It builds on Level 2 and adds enhanced practices to address advanced persistent threats (APTs).
- FedRAMP High: Applies to cloud service offerings (CSOs) where loss of confidentiality, integrity, or availability could have severe adverse effects on agency operations or assets.
- Control set and requirements:
- CMMC Level 3: Requires 110 practices from NIST SP 800-171, plus an additional 30 enhanced requirements from NIST SP 800-172 that are specific to countering APTs.
- FedRAMP High: Requires up to 421 controls from NIST SP 800-53.
- Assessment:
- CMMC Level 3: CMMC Level 3 requires a government-led assessment by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), part of the Defense Contract Management Agency (DCMA), every three years, along with annual self-affirmations from the organization.
- FedRAMP High: Requires an initial full 3PAO authorization against all 421 controls. Afterward, the service provider must perform an annual 3PAO assessment of a subset of controls and perform continuous monitoring (e.g., monthly vulnerability scans, POA&M updates, and incident reporting).
FedRAMP Impact Baselines vs. CMMC Maturity Levels
|
Framework
|
Tier
|
Definition / Scope
|
Control Set
|
Assessment
|
Frequency
|
|
CMMC
|
Level 1
|
Contractors handling only Federal Contract Information (FCI)
|
15 basic safeguarding requirements (from FAR 52.204-21)
|
Annual self-assessment
|
Every year (self-attested)
|
| |
Level 2
|
Contractors handling Controlled Unclassified Information (CUI)
|
110 practices from NIST SP 800-171
|
C3PAO third-party assessment + annual affirmation
|
Full reassessment every 3 years; affirmation annually
|
| |
Level 3
|
Contractors with the most sensitive CUI tied to national security
|
130+ practices (NIST SP 800-171 + enhanced practices from SP 800-172)
|
Government-led assessment by DIBCAC + annual affirmation
|
Full reassessment every 3 years; affirmation annually
|
|
FedRAMP
|
Low
|
Cloud services where a breach would cause limited adverse effects
|
125 controls from NIST SP 800-53 (Low baseline)
|
C3PAO initial authorization + continuous monitoring
|
Initial full authorization; annual subset assessment; monthly continuous monitoring
|
| |
Moderate
|
Cloud services where a breach would cause serious adverse effects
|
325 controls from NIST SP 800-53 (Moderate baseline)
|
3PAO initial authorization + continuous monitoring
|
Same as Low (annual 3PAO subset assessment + monthly monitoring)
|
| |
High
|
Cloud services where a breach would cause severe/catastrophic adverse effects
|
421 controls from NIST SP 800-53 (High baseline)
|
3PAO initial authorization + continuous monitoring
|
Same as Low/Moderate (annual 3PAO subset assessment + monthly monitoring)
|
How to reuse FedRAMP controls for CMMC if you do need both
If your organization already complies with FedRAMP, you’re well-positioned to meet CMMC requirements in the rare case you’ll need it. For efficiency, align with the highest FedRAMP level you plan to achieve, then tailor down to CMMC for any areas of your system outside the FedRAMP boundary.
Most organizations will only need to comply with either FedRAMP or CMMC, not both. For the rare cases where both apply, you can design your security controls strategically to satisfy the requirements of each framework as efficiently as possible. This situation typically arises when a cloud service provider (CSP) is hosting federal data in the cloud (triggering FedRAMP) while also holding a DoD contract with a DFARS clause that requires CMMC compliance for systems outside the cloud environment.
“You can write a single set of policies that satisfy both FedRAMP and CMMC controls,” says Lex. “The procedures may differ slightly between the two, but you can note those differences within your policy. The key is to tailor the control to the highest FedRAMP level you want to meet, since those requirements are often stricter — for example, FedRAMP’s password rules go beyond CMMC’s. By aiming for the stricter FedRAMP standard, you’ll naturally cover CMMC as well.”
Lex cautions that, while mapping between FedRAMP and CMMC can look straightforward on paper, organizations often overlook the context each framework applies to.
“Some companies assume they’re CMMC compliant just because they’re FedRAMP Moderate — or even have the DoD’s FedRAMP Moderate equivalency,” she explains. “But CMMC’s scope is different from FedRAMP’s. WhereasedRAMP is focused on cloud systems, while CMMC applies to the entire organization wherever CUI is handled. If you’re processing CUI outside of your FedRAMP boundary, you’ll still need to meet CMMC. There are also control areas that differ, like personnel security and supply chain risk, particularly if you manage physical CUI.”
What’s different between FedRAMP evidence and CMMC evidence?
Both FedRAMP and CMMC require evidence that shows your security controls are in place. Because both draw from NIST standards, the types of evidence are similar. However, FedRAMP often requires more technical testing, while CMMC can involve on-site inspections.
According to Lex, CMMC and FedRAMP accept and require similar types of evidence. “Since both frameworks draw on NIST, which defines assessment methodology, the evidence that FedRAMP and CMMC organizations provide is similar. For example, organizations will offer documentation, make sure stakeholders are available for interviews with assessors, demonstrate systems, and perform technical tests as needed.”
She continues, noting that there are differences since FedRAMP focuses on a cloud environment, which is usually more technical and advanced. “FedRAMP usually involves technical testing, like a penetration test.” In contrast, CMMC often involves a physical inspection of the premises where the organization works with CUI.
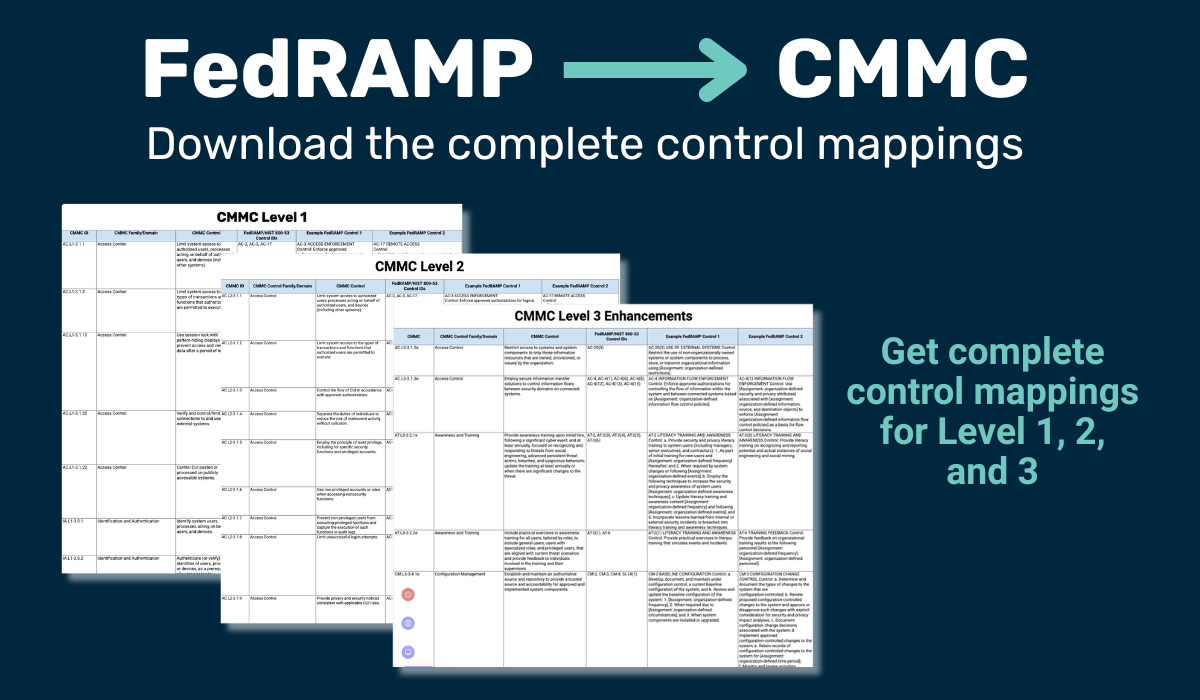
Download FedRAMP/CMMC control mapping
Get this spreadsheet showing controls for CMMC and FedRAMP in one convenient place. It details all three CMMC level controls and highlights the FedRAMP controls.

Download our free FedRAMP/CMMC mapping.
Time and cost to achieve FedRAMP and CMMC compliance
Achieving both FedRAMP and CMMC compliance can take months for mature organizations or years for less prepared ones. Costs often reach hundreds of thousands to millions of dollars, especially at advanced levels. FedRAMP is typically more costly and time-intensive, but completing it first streamlines CMMC since many requirements overlap.
Is CMMC easier if I already have FedRAMP?
Yes, if your organization already complies with FedRAMP, achieving CMMC is usually easier because many requirements overlap. However, if your CMMC environment differs significantly from your FedRAMP environment, it may not offer much assistance.
“How quickly an organization can adapt from FedRAMP to CMMC really depends on the degree of overlap,” says Lex. “If the environment and boundaries are the same, the process is much faster. Since CMMC requirements are derived from FedRAMP, much of the groundwork is already in place. In fact, if you’re operating within the same boundary, you’ve likely already met, or even exceeded, several technical controls.”
How long does it take to do FedRAMP or CMMC?
The timeline depends on the certification level you’re pursuing and how mature your security program is. Organizations with strong existing controls may be able to finish in several months. Less prepared companies may spend a year or more, sometimes multiple years, to reach compliance.
To become compliant with either framework, organizations must implement the required controls, create a System Security Plan (SSP), and gather policies and evidence. They must then undergo an assessment by a C3PAO for CMMC or a 3PAO for FedRAMP. Each of these steps can take very different amounts of time depending on the organization, but even the most mature teams should expect to spend months preparing, followed by several more months for the assessment and submission.
“The timeline to compliance in either framework varies greatly between organizations,” explains Lex. “It could take as quickly as a few months if you have an already mature system, and plenty of time and resources to dedicate to the effort.”
Here’s an estimate of how much time it might take a typical organization to pursue CMMC or FedRAMP compliance, depending on the level. These are very broad estimates, and the actual time might vary greatly depending on your company’s existing cybersecurity measures, your resources, and the scope of your system and environment.
- FedRAMP:
The FedRAMP process is the same across all impact levels: organizations implement the required security controls for their level, undergo a 3PAO assessment, and then maintain compliance through annual continuous monitoring. The average timeline to achieve an initial authorization is 12 to 18 months, though this can vary widely depending on how prepared the organization is at the outset. According to Lex, the 3PAO assessment itself typically takes 8 to 12 weeks.
- CMMC:
Because the assessment process varies by level, the timeline largely depends on how compliant your organization already is.
- Level 1: The preparation and self-assessment may only take a few weeks to a couple of months to complete. The typical duration from start to finish is 2 to 4 months.
- Level 2: The full timeline will be eight months to 18 months, depending on the organization's size and maturity. The assessment may take anywhere from six weeks to three months.
- Level 3: Level 3 compliance will require 18 months or more of effort.
How much does it cost to do FedRAMP or CMMC?
Both frameworks require a major investment, but FedRAMP is usually more expensive because it requires more controls. FedRAMP typically costs from half a million to several million dollars. CMMC costs scale by level, from tens of thousands at Level 1 to millions at Level 3.
The cost of pursuing either framework comes from several areas: preparing for compliance (implementing controls, writing policies, gathering evidence), completing the assessment, addressing any gaps, and performing continuous monitoring. Then, the cost of each of these steps depends on your organization’s existing cybersecurity posture and the specific certification level you’re pursuing. It also depends on the scope of your IT environment.
Lex notes that preparation costs can look similar for mature organizations, but that a FedRAMP assessment will always cost more. “If your organization already has strong cybersecurity in place, you might not spend much more money complying with one or the other, though both are very costly to implement, But the audit will also affect the price. A FedRAMP audit covers considerably more controls, so it takes the assessor more time and costs more.”
Harnagel points out that, for CSPs, the added cost may be worthwhile. “The audits are more expensive and take longer. But FedRAMP authorization opens the door to more lucrative government contracts.”
Here’s a very broad overview of the costs an organization might face, level by level, for its first assessment and initial preparation.
- CMMC
As part of the CMMC level 2.0 final rule, which defines the CMMC 2.0 guidelines and assessment practices, the Department of Defense (DoD) estimates the cost to become compliant for each level:
-
- Level 1:
- Preparation and implementation: The DoD doesn’t estimate implementation costs, since Level 1 requirements are basic practices a company should already have in place.
-
-
- Assessment: The costs for the Level 1 annual self-assessment depend on the effort you need to collect evidence. DoD estimates about $5,000 for the initial assessment.
-
- Level 2:
- Preparation and implementation: The DoD doesn’t estimate implementation costs, since they treat Level 2 requirements as security practices that a company should already have in place.
-
-
- Assessment: Depending on the contract, a Level 2 company can either self-assess or undergo a third-party certification audit:
- Self-assessment: (triennial + annual affirmations): The DoD estimates around $30,000 to $50,0000 over three years.
- C3PAO assessment (triennial assessment + annual affirmations): The DoD estimates around $117,000 over three years.
-
- Level 3:
Note: Level 3 is a new addition to CMMC 2.0, and all cost figures are rough estimates.
- Preparation & implementation: Level 3 requires additional controls from NIST SP 800-172, so DoD includes significant “nonrecurring engineering” costs to implement them, between $2.7 million to $21.1 million.
-
-
- DIBCAC Assessment: DoD estimates $9K to $39K over three years, though external sources put real-world costs closer to $100,000 to $500,000.
- Note: Level 3 is still new, and all cost figures should be treated as rough estimates.
- FedRAMP
There are no official, government-issued cost estimates for pursuing FedRAMP.
Here’s a broad guideline based on industry consensus:
- FedRAMP Low: Hundreds of thousands in the first year, tens to hundreds of thousands annually.
- FedRAMP Moderate: Typically between half a million $1.5 million upfront, and a few hundred thousand per year.
- FedRAMP High: $1 million to several million up front, with substantial ongoing costs.
How to implement CMMC and FedRAMP efficiently
To implement both CMMC and FedRAMP, start with FedRAMP as the baseline since it is stricter. Work with an assessor accredited for both frameworks and make sure you understand the scope of each framework and where it applies in your system. Also, consider using software that supports both frameworks.
Since CMMC and FedRAMP have overlapping requirements, it’s possible to pursue both frameworks in a single, concentrated effort, instead of treating them as two totally separate projects. Still, both frameworks are part of a constantly changing federal security landscape, where cybersecurity standards evolve regularly, and it’s important to keep up with the latest requirements.
Here are some tips on how to “bundle” CMMC and FedRAMP if you happen to be one the few companies that needs both:
- Work backward to identify your timeline:
“Check your contracts to see whether you need CMMC certification or FedRAMP authorization by a specific date,” says Lex. “Then, work backward to build a timeline and plan milestones.”
- Map your scope
Both CMMC and FedRAMP cover Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). Since CMMC applies to the entire organization, not just the cloud, define and, if possible, limit your scope. This helps eliminate outlier data in unexpected places and reduces both cost and effort.
- Use FedRAMP as your guide:
“One hundred percent of CMMC controls are a subset of FedRAMP controls that have been tailored to focus on confidentiality and apply to private entities,” says Lex. “Specifically, NIST 800-171, the guidelines behind CMMC, is a subset of NIST 800-53, which FedRAMP applies. Because of that, there’s a natural overlap between the two sets of requirements, particularly at the policy level. But the level of effort, or ‘lift,’ for FedRAMP is significantly higher in many areas. For example, both frameworks have password requirements, but FedRAMP requires many more characters.”
- Prepare a single set of policies and procedures
“You can write one set of policies to cover both frameworks,” says Lex. “Always tailor them to the stricter standard — FedRAMP.”
- Hire a dual-credential assessor
Lex recommends working with a dual credential assessor, meaning an individual or organization that is both a C3PAO and a 3PAO. They can help you prepare, streamline your efforts, and perform assessments on overlapping requirements at the same time instead of separately.”
- Leverage compliance software
Use compliance software that splits the NIST 800 171-11 and 800-53 frameworks so you can manage both FedRAMP and CMMC.
How to streamline CMMC and FedRAMP compliance with Strike Graph
Compliance rarely stops at one framework, and that certainly includes CMMC and FedRAMP. A defense contractor may need CMMC alongside ISO 27001 or SOC 2. A cloud service provider pursuing FedRAMP may also need to meet StateRAMP or commercial standards. Strike Graph brings them all together in one unified system, so you can manage multiple frameworks without duplicating effort.
The Strike Graph platform adapts to your scope, aligns overlapping requirements, and highlights where evidence can be reused. Its AI-powered engine maps shared controls, guides you step by step through each framework, and keeps your documentation organized.
With a customizable dashboard that supports SSPs, POA&Ms, self-assessments, and full authorizations, Strike Graph helps you stay continuously audit-ready. Whether you’re handling CMMC, FedRAMP, or pairing either with other standards, compliance becomes less of a burden and more of a streamlined strategy you can manage with confidence.
Ready to get started? Open a free launch account or schedule a demo with one of our privacy experts.
FAQs on CMMC 2.0 vs. FedRAMP
Get quick answers to the most common questions about CMMC and FedRAMP. Learn how they differ, where they overlap, and get practical strategies for pursuing both frameworks.
effectively.
Are FedRAMP and CMMC the same?
No, they are not the same. FedRAMP sets requirements for cloud service providers that contract with the federal government and protects federal data in the cloud. CMMC sets requirements for contractors in the Defense Industrial Base and covers every system or person that handles defense data.
Is FedRAMP required for CMMC compliance?
No, FedRAMP is not required for CMMC compliance. The frameworks overlap but have separate scopes and processes. You don’t need FedRAMP for CMMC, but if you use the cloud to store Department of Defense data, your provider must be FedRAMP authorized or equivalent.
How are CMMC 2.0 and FedRAMP related to NIST?
Both CMMC 2.0 and FedRAMP use NIST cybersecurity guidelines. CMMC 2.0 Level 2, the most common level, is based on NIST SP 800-171, while FedRAMP follows NIST SP 800-53. Because 800-171 is a subset of 800-53, FedRAMP’s requirements are more extensive and detailed.
What’s the difference between FedRAMP authorization and CMMC certification?
FedRAMP authorization means a cloud service provider has passed a FedRAMP assessment and can offer services to federal agencies. CMMC certification means an organization has implemented CMMC requirements, passed a C3PAO assessment, and is eligible to bid on defense contracts at its certified level.
Can FedRAMP compliance help with CMMC compliance?
Yes, FedRAMP authorization can help with CMMC compliance because its requirements are similar but more demanding. The benefit depends on the scope. If FedRAMP applies only to the cloud, the organization will likely need more work to extend controls across the full CMMC environment.
Is there a FedRAMP equivalent to CMMC Level 2?
There is no FedRAMP equivalent to CMMC Level 2. But, there is a FedRAMP equivalency program that lets CMMC Level 2 contractors use cloud providers with FedRAMP Moderate equivalency. This is not the same as full FedRAMP or CMMC authorization, but it gives defense contractors more options when choosing cloud providers.
Which should I do first — FedRAMP or CMMC?
It depends on your business needs, contractual requirements, and cybersecurity environment. Experts recommend starting with the certification that brings in the most business for your organization. If you want both, it makes sense to begin with FedRAMP’s guidelines, since they are the most demanding, but to be aware that the CMMC scope is usually much broader.
Do subcontractors need CMMC or FedRAMP?
CMMC subcontractors usually need their own certification if they handle DoD data. FedRAMP applies only to the cloud system, so subcontractors follow its security policies but don’t need separate FedRAMP authorization for their organization.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)


 “CMMC and FedRAMP target very different types of organizations,” explains
“CMMC and FedRAMP target very different types of organizations,” explains 







.png?width=600&height=600&name=Starter%20Kit%20for%20CMMC%20Plan%20of%20Action%20%26%20Milestones%20(2).png)


