The common wisdom about data and privacy compliance just isn't keeping up with the current business landscape.
So what can business and tech leaders do about it? If you want to outpace the competition while creating a security program that will stand the test of time, we recommend thinking about compliance in a holistic, tech-enabled way.
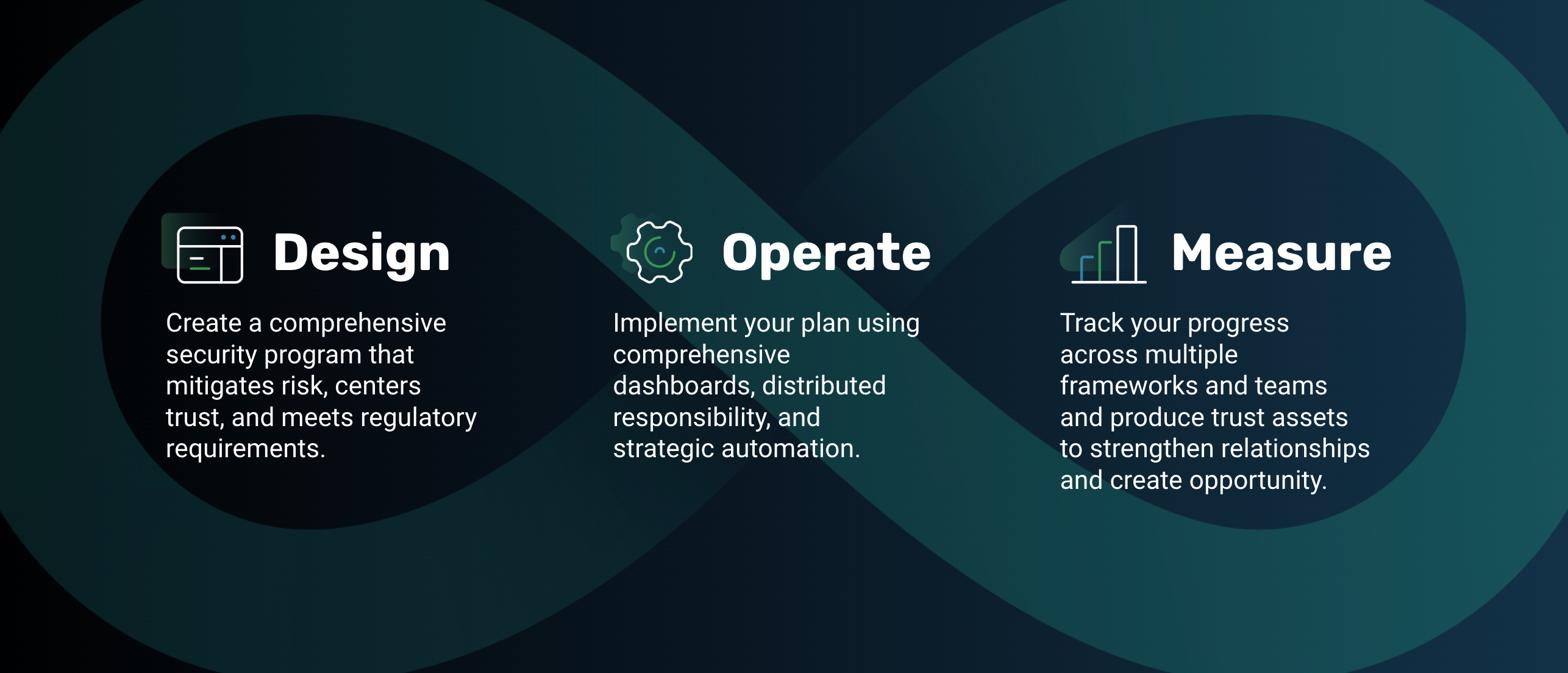
This up-to-date method of designing your security program uses three interlocking phases: design, operate, and measure.
In this blog post, we’ll dig into the design part of the process. Then, in the following two installments of this series, we’ll dive into the operation and measurement stages. So stay tuned.
Let’s do it!
The old-school way of thinking about security program design
What used to happen a lot in the past — and, sadly, sometimes still happens today — was that IT security was considered a distraction and only implemented when it was demanded by customers, often haphazardly.
When companies did finally decide to implement security, they usually took one of two paths: 1. Hiring a consultant or 2. Opting for a certification-in-a-box approach. The problem with these paths is that not only are both inefficient and expensive, they’re also typically unsuccessful. Let’s take a closer look at each to understand why.
Hiring a consultant
Hiring a security consultant can be expensive. Why? Because their expertise and time come at a premium, and their fees can add up, particularly if your organization requires ongoing consultation or assistance. Consultants also may not have an in-depth understanding of your company's culture, operations, and specific needs. This means they might lack the context required to design a security program that aligns perfectly with your organization's goals, values, and workflows.
Furthermore, given that they typically work on a contractual basis, once their engagement is complete, consultants may not have a continued presence within your organization. This can potentially lead to challenges in maintaining and evolving your security program over time, as the responsibility falls back on internal resources who may not have the same level of expertise.

Opting for certification in a box
Checklist-based certification software claims to provide a comprehensive security program for organizations, but is often generic and one size fits all. This means these pre-packaged frameworks or templates will fail to take into account the unique needs, risk profile, and/or specific requirements of your organization. This can result in a security program that is either too rigid and impractical or fails to address critical vulnerabilities specific to your industry or operations.
These solutions also may not easily adapt to changes in your organization, technology, or evolving security threats. This lack of flexibility to accommodate emerging risks and regulatory changes can leave your company exposed, and/or require significant effort on your part to modify the program accordingly.
Choose a holistic approach to designing your security program
Taking a proactive approach to designing a program that builds trust can not only be more efficient, but more effective too. Building said trust — which, as you know, is essential to revenue generation — can be accomplished via a TrustOps program, which produces security assets like certifications. These trust assets build the confidence of customers and stakeholders, enabling faster growth and more revenue.
So what does this all mean for your company? It means that now is the time to ditch the checklist approach and switch to TrustOps thinking. Not only will you be able to leverage technology — like compliance software — to make your TrustOps program accessible to people with no prior expertise, you’ll also save time and money while ensuring a good fit with your business model.
Strike Graph is here to help
Understanding how to design a security program — including where to start, what technology to employ, and who to trust — can make anyone’s head spin. That’s why we designed our all-in-one platform to take you through all three interlocking phases of the security/Trust Ops process — design, operate, and measure — painlessly and efficiently.
There’s also no need to hire an outside audit firm because we do your certifications in house. And, as you grow, the Strike Graph platform grows with you, allowing you to add certifications as your company expands and matures.
Ready to get started designing now? Click the banner below. And, keep an eye out for upcoming two more posts on operating and measuring your TrustOps program.
Want to read more? Click through to the next article in this series.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)