Data Center Solutions
Future-proof every data center deployment stage
Centralized evidence management, automated workflows, and continuous evidence monitoring ensures a seamless security posture across diverse data center environments. Leveraging expert support, Strike Graph enables organizations to achieve and maintain security compliance with rigorous standards from colocation to hyperscale.

Suggested frameworks
ISO 27001
While remaining a core standard, it's increasingly integrated with other frameworks for a more holistic approach.
SOC 1
Focus is shifting beyond financial reporting to encompass broader security controls relevant to data centers.
SOC 2 & 3
Importance is rising as data center services become more critical for businesses, requiring transparency in security posture.
PCI-DSS
Continuously updated to address new vulnerabilities and payment methods impacting data security.
GDPR
Global impact is significant, pushing data centers to strengthen data privacy controls even if not directly located in the EU.
Challenges faced by data centers
Compliance Overload
Data centers, particularly those operating at scale, grapple with a complex web of overlapping compliance standards. From colocation facilities managing a handful of clients to hyperscale providers handling vast amounts of data, the burden of adhering to multiple frameworks is immense. This redundancy leads to inefficiencies, increased costs, and a potential diversion of resources from core operational functions.
Keeping track of evolving regulations, updates to frameworks, and upcoming audits creates a constant need for monitoring and adaptation.
Integrating controls and procedures from multiple frameworks into a single, cohesive security strategy can be a major undertaking.
Resource Constraints
Meeting the demands of various audits, the need to check all items of evidence within your controls can strain internal teams, diverting focus from core data center operations.
Compliance audits require dedicated security professionals to manage documentation, evidence collection, and internal control reviews. This diverts valuable resources from core data center operations, such as infrastructure maintenance and security incident response.
Gathering evidence for audits often involves manual processes like compiling logs, reports, and security policies. This can be time-consuming, error-prone, and difficult to scale as data volumes grow.
The looming threat of audits forces a reactive approach. Data centers scramble to gather evidence just before deadlines, creating a constant strain on resources and leading to potential oversights.
Data Security Concerns
Operate in a landscape marked by heightened customer expectations, stringent regulations, and evolving cyber threats. Safeguarding sensitive data while meeting compliance requirements is a complex challenge. Hyperscale providers, in particular, face the added pressure of managing vast amounts of data across multiple jurisdictions, making data security a paramount concern.
Customers are more aware than ever of data breaches and privacy scandals. They demand robust data security from the data centers they trust with their sensitive information.
Regulatory landscapes are constantly evolving, with frameworks like GDPR imposing hefty fines for non-compliance. This puts pressure on data centers to demonstrate a strong commitment to data security.
The sophistication and frequency of cyberattacks are on the rise. Data centers need to stay ahead of these threats to ensure customer data remains protected.
Key Trends
Frameworks are becoming more interconnected, with overlapping requirements. This pushes the need for data centers to adopt a comprehensive compliance strategy.
As data centers migrate to cloud environments, security controls need to adapt to address new challenges.
Data privacy regulations like GDPR are raising the bar for data security and user control over their information.
Strike Graph's solution for data centers
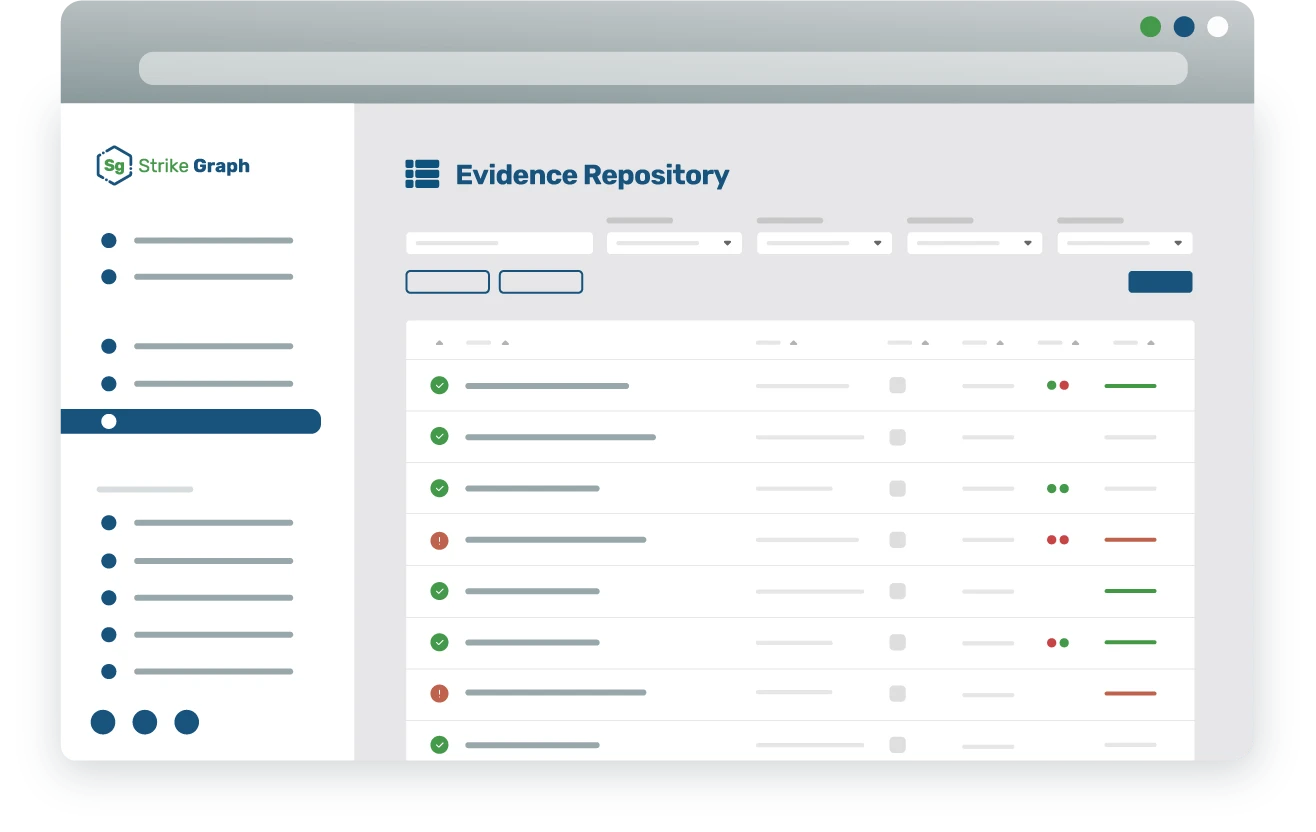
Centralized Evidence Management
Share ownership of security tasks across multiple teams and individuals, building a culture of compliance.

Automated Workflows
Data centers operate in a world of ever-increasing compliance demands, with each framework having its own set of requirements, leading to a mountain of repetitive tasks like risk assessments, control implementation, and policy management. Strike Graph tackles this challenge head-on with automated workflows, freeing up your valuable resources.

VerifyAI
Further strengthen your data center's control monitoring with our in-house advanced AI to continuously analyze your evidence whether you are using our automated workflows or manual uploads, VerifyAI will ensure your evidence is matching your control definition
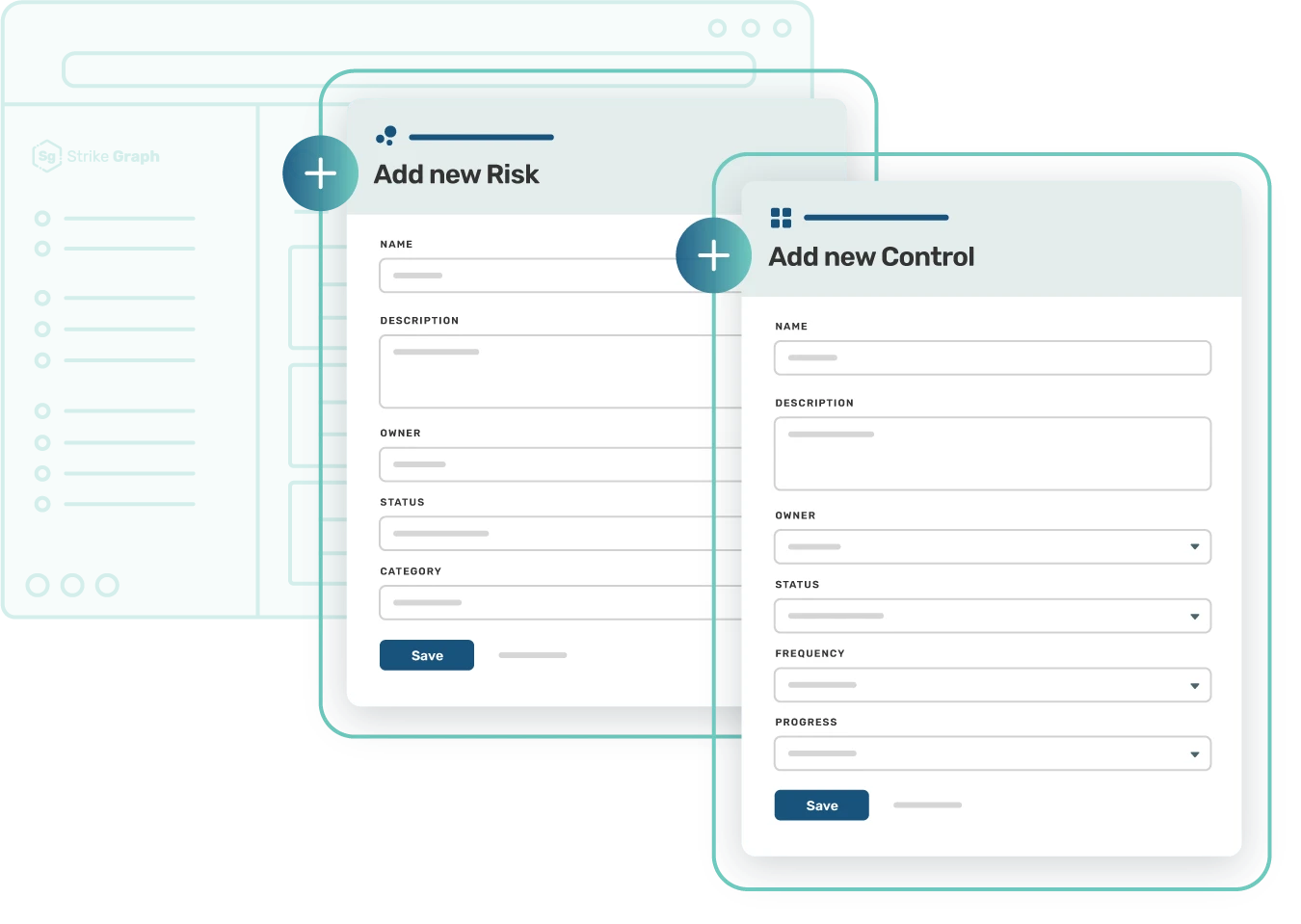
Custom Controls
Data centers face the constant challenge of maintaining a robust cybersecurity environment while navigating the complex web of compliance frameworks. Strike Graph tackles this challenge head-on with a powerful solution, modify pre-mapped control libraries to industry-specific data center compliance frameworks.
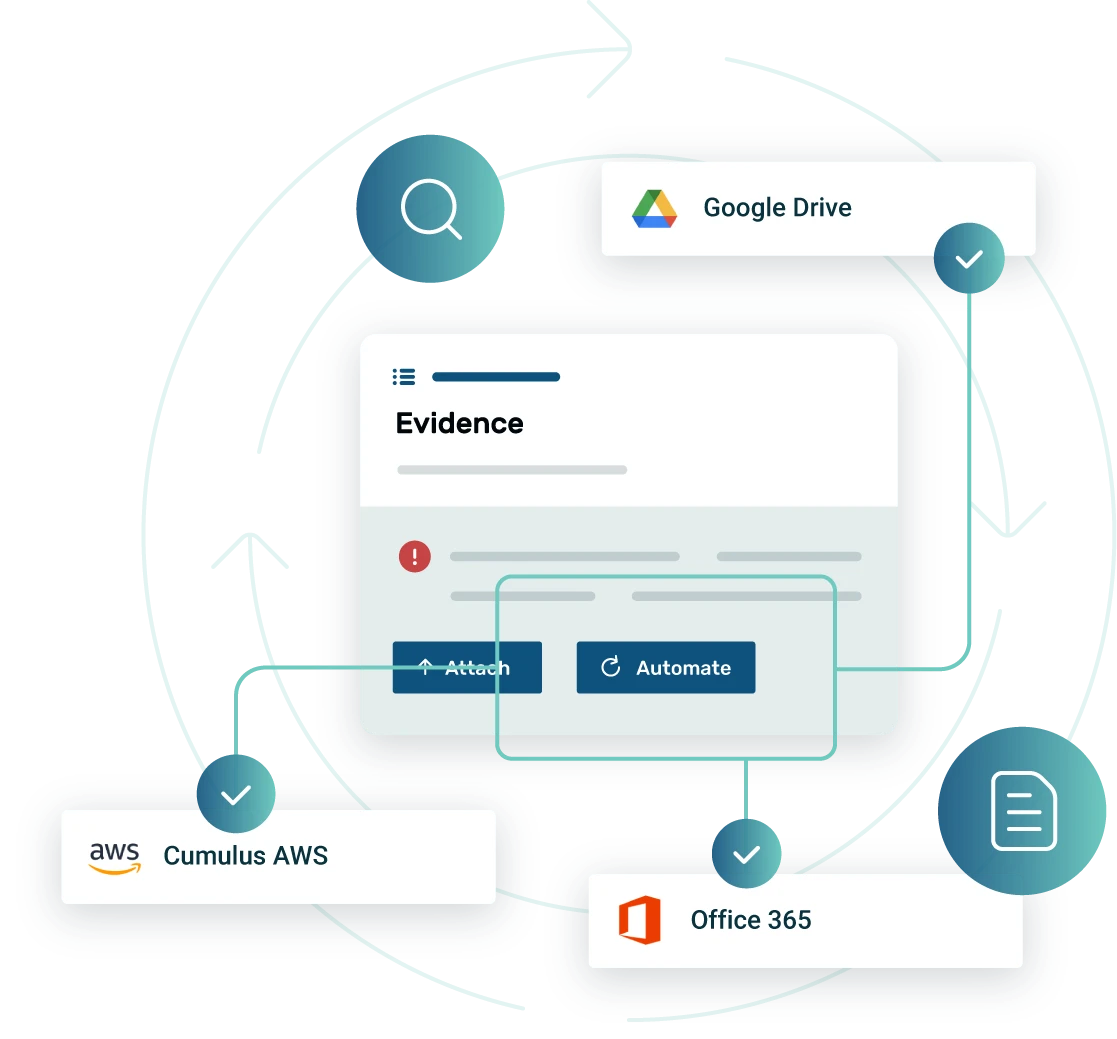
Continuous Monitoring & Reporting
Traditional methods often struggle with real-time visibility and actionable insights. Strike Graph offers a solution by providing real-time compliance status, comprehensive reporting, and continuous monitoring of evidence uploads. This enables data centers to proactively manage risk, ensuring that evidence remains up-to-date and aligned with compliance requirements.
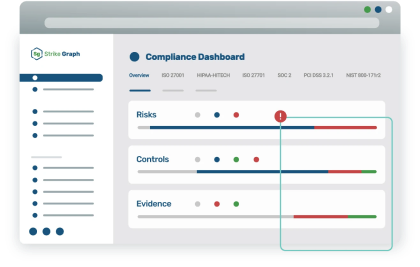
GAP Analysis
Identify discrepancies between your current security posture and desired compliance standards. By pinpointing areas of vulnerability, we equip organizations with the ability to prioritize remediation efforts and allocate resources effectively.
.webp?width=1260&height=963&name=illustration-library-report-questionnaire%204%20(1).webp)
Seamless Navigation
Strike Graph provides dedicated customer success managers to guide you through every step of your compliance journey. Our experts assist in connecting your organization to relevant frameworks, conducting in-depth risk assessments, and developing tailored compliance strategies. With ongoing support, training, and best practice guidance, we ensure seamless integration of our platform into your existing security infrastructure.
User-Centric Design
Strike Graph prioritizes a user friendly interface and experience to streamline the compliance process for data center professionals. The platform is intuitive and easy to adapt, reducing the learning curve and allowing teams to focus on strategic initiatives rather than a complex software platform.
Service Bundled Solutions
From pen tests, vulnerability scans and audits - achieve guaranteed cyber resilience with our specialty designed data center packages and expert guidance.
Scalability and flexibility
As compliance requirements expand and diversify, our platform adapts to incorporate new frameworks and regulations.
Efficiently manage your compliance obligations without compromising on security or operational efficiency.
Scale with evolving customer needs signifies a long-term commitment to providing solutions and support.
Attract new customers in industries with stricter compliance requirements.
Open doors to new markets with specific data security regulations.
Additional resources
Our extensive library of resources will answer all your questions.
Ready to start exploring?
Ready to revolutionize how you manage data center security compliance?
Simplify compliance
The best way to understand how powerful the Strike Graph platform is is to jump right in and give it a spin.
Still have questions? Let us show you around.
Connect with Strike Graph today to see how you can achieve your compliance goals.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Ready to see Strike Graph in action?
Fill out a simple form and our team will be in touch.
Experience a live customized demo, get answers to your specific questions , and find out why Strike Graph is the right choice for your organization.
What to expect:
- Lorem Ipsum is simply dummy text of the printing and typesetting industry.
- Lorem Ipsum is simply dummy text of the printing.
- It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout.
- The standard chunk of Lorem Ipsum used since the 1500s
We look forward to helping you with your compliance needs!
Fill out a simple form and our team will be in touch.
Experience a live customized demo, get answers to your specific questions , and find out why Strike Graph is the right choice for your organization.
What to expect:
- Lorem Ipsum is simply dummy text of the printing and typesetting industry.
- Lorem Ipsum is simply dummy text of the printing.
- It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout.
- The standard chunk of Lorem Ipsum used since the 1500s
We look forward to helping you with your compliance needs!
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)


