Measure
Leverage the power of proven compliance
You’ve made sure your data is secure — now how do you get the return on that investment?
Strike Graph streamlines certification and real-time reporting so you have the proof you need to build customer confidence and close new deals.
Rigorous measurement means real results
Design
Operate
Measure
EVALUATE
AI-powered
certification
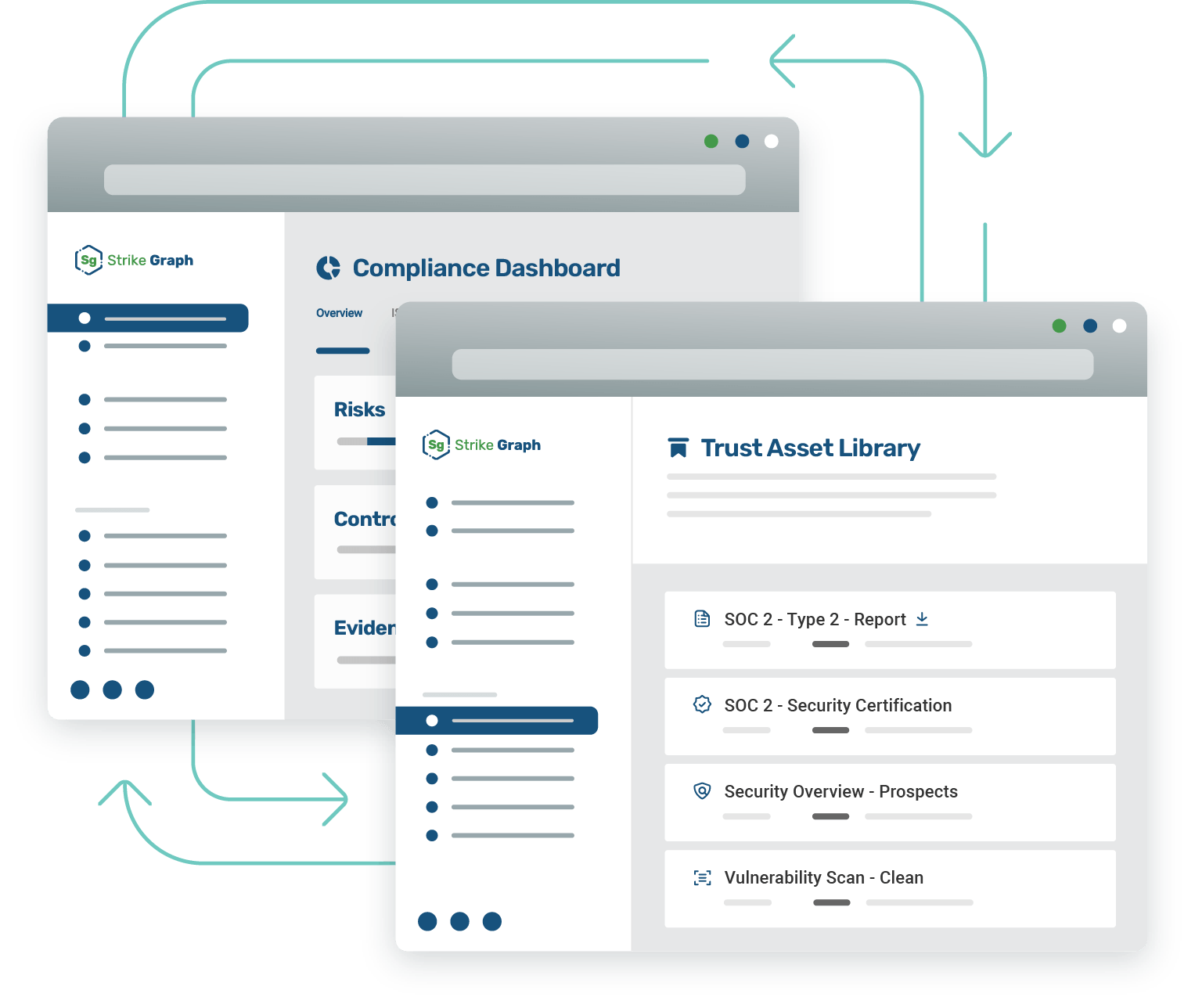
Simplify certification with Strike Graph’s AI-enabled audit process and quickly achieve trust assets critical for building trust and closing deals.
IMPROVE
Intelligent data
Interactive dashboards, real-time reporting, and a personalized AI security assistant ensure you have the data at your fingertips to keep your company secure.
Monitor
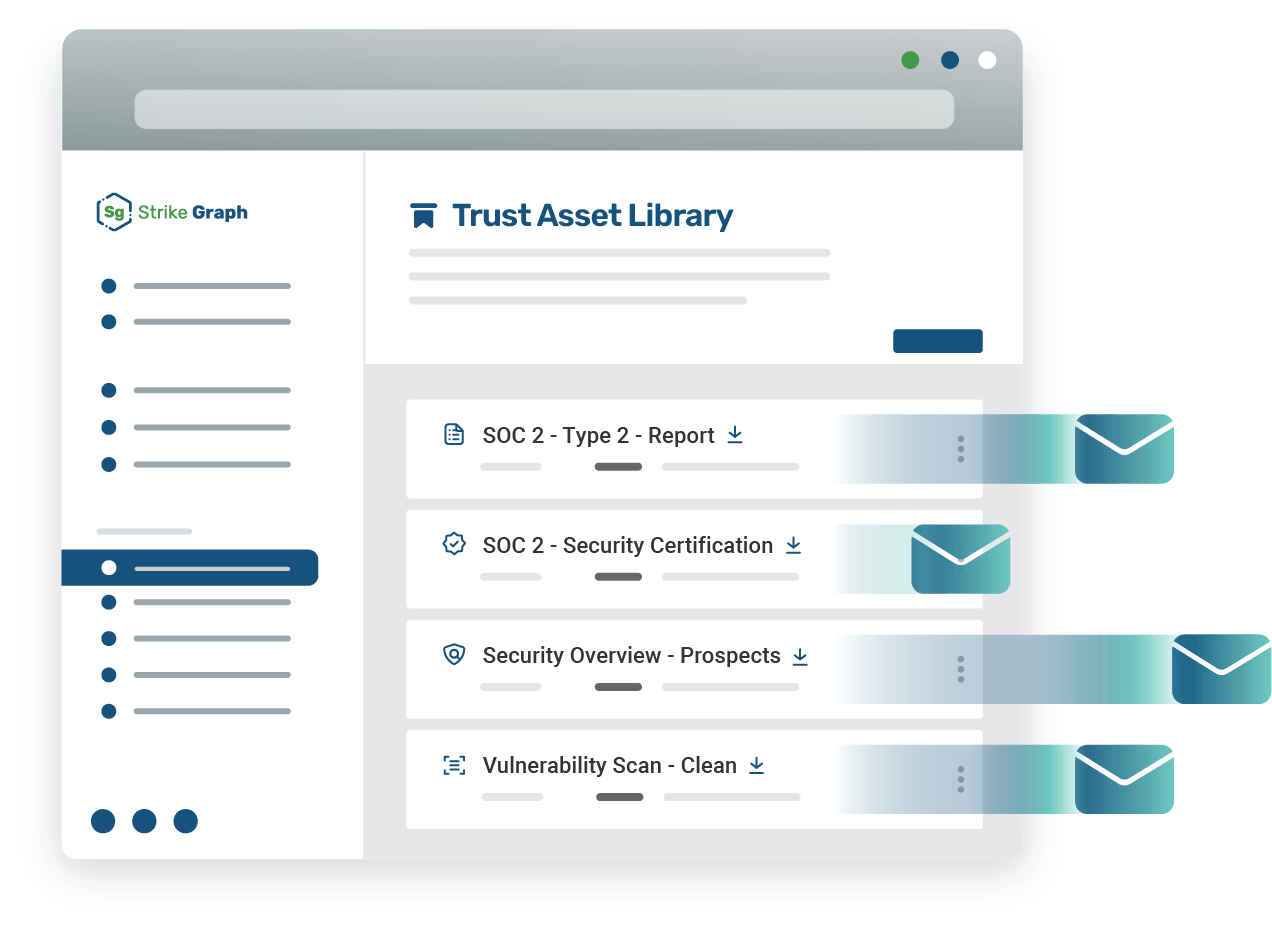
Trust asset library
Keep your valuable trust assets up-to-date, organized, and ready to easily share with potential customers and investors using our trust asset library.
VULNERABILITY SCANNING
Find your gaps before the hackers do
Hackers are always on the lookout for weaknesses in your digital defenses. Strike Graph’s integrated vulnerability scans and expert pen tests ensure you’re protected.
Take your security program from resource drain to revenue driver
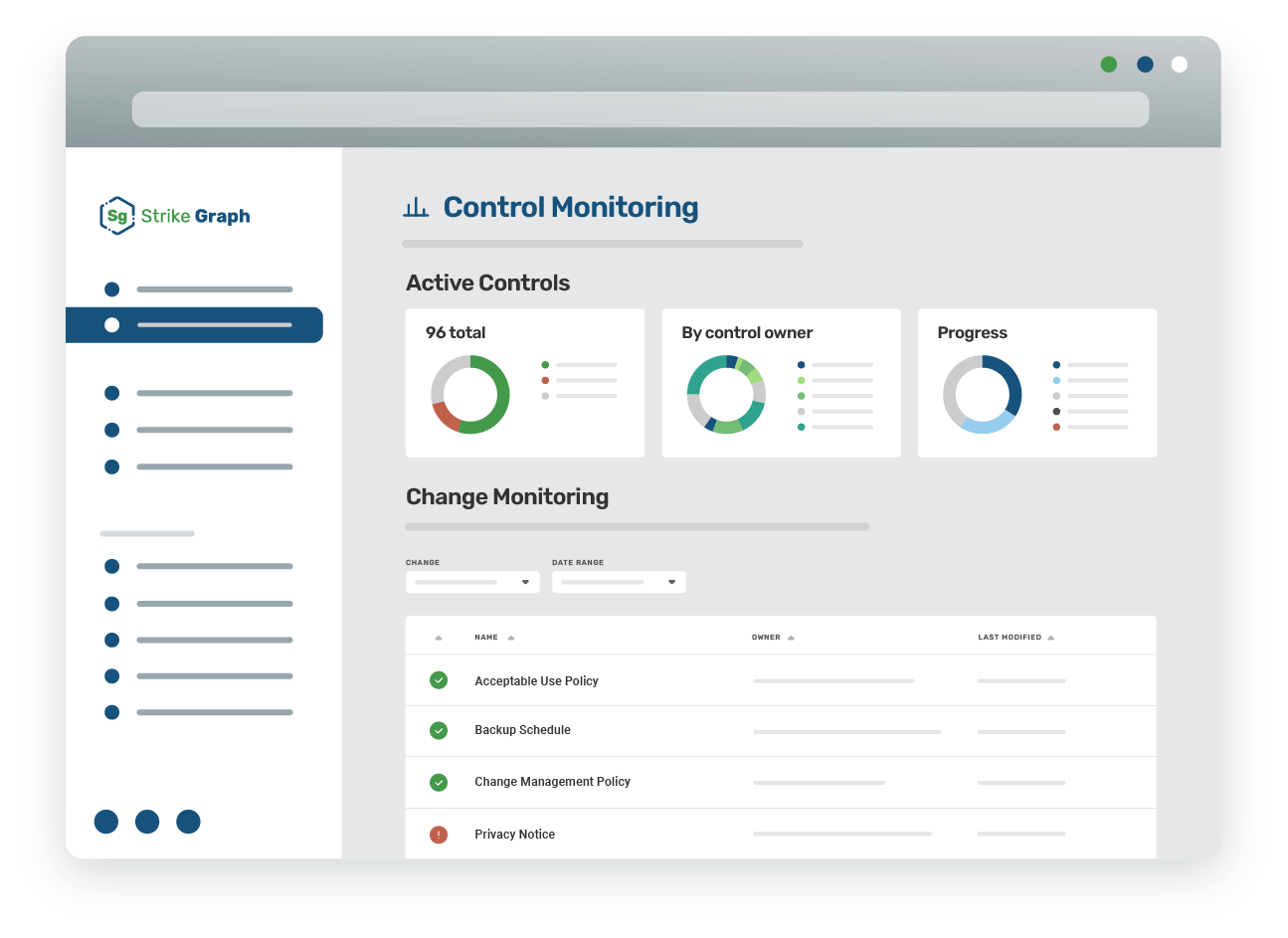
Comprehensive dashboards
Get a comprehensive overview of your security efforts, making it easy to identify areas for improvement and celebrate successes.
Trust asset libary
Easily organize, access, and share all of your trust assets — the keys to transforming your security efforts into revenue.
Audit prep management
Delegate and manage audit tasks across teams, embedding a compliance-first mindset throughout your organization.
Gap analysis
Leverage a rich set of tools to identify and close security gaps, ensuring your defenses are robust and comprehensive.
Control monitoring
Measure the effectiveness of your security controls, then add from our extensive control library as needed to fit your unique requirements.
High-impact reporting
Generate real-time reports that give you the proof you need to turn your security efforts into high-value trust assets.
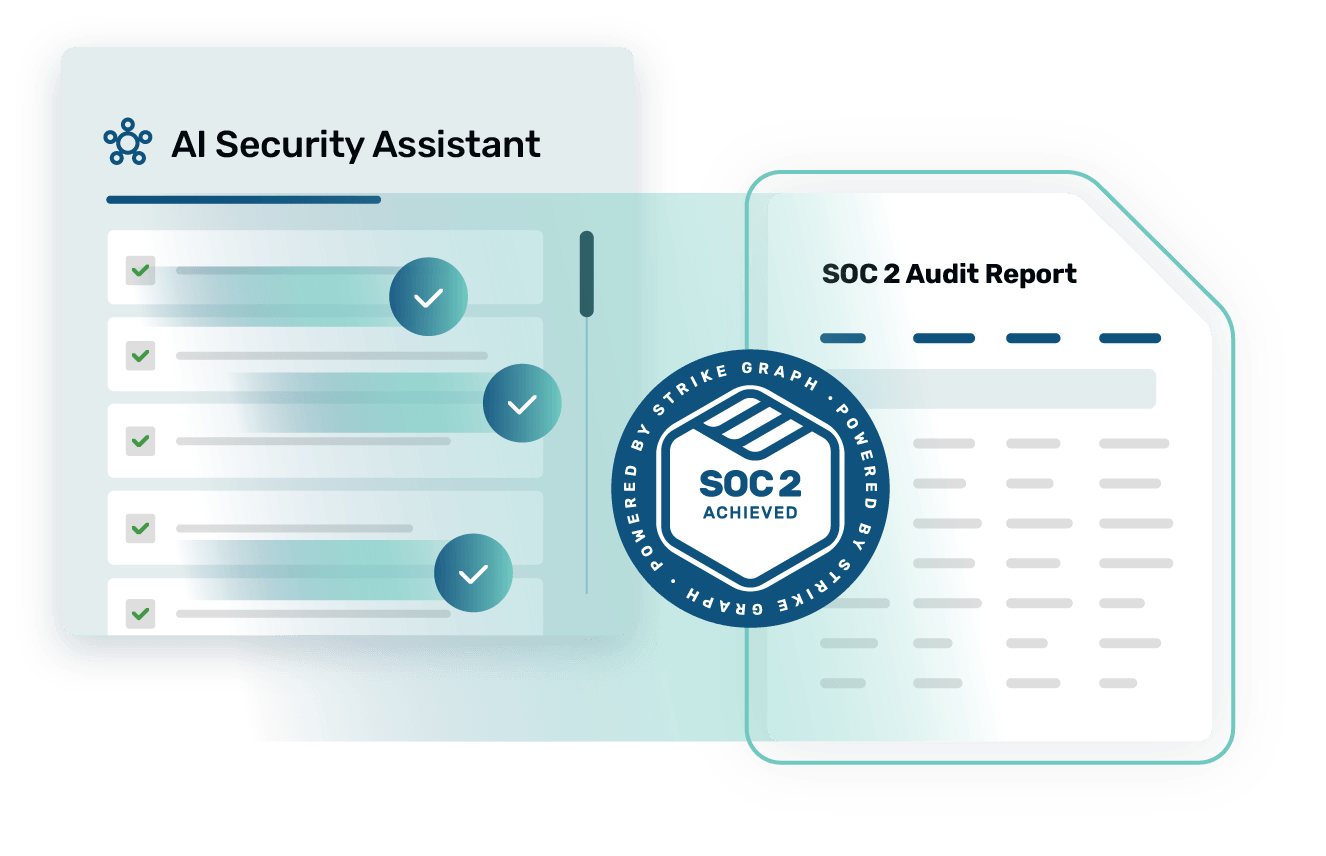
Get instant answers about your security program from your AI security assistant
Instead of wasting team hours tracking down information from your various policies, reports, controls, and evidence, just ask your personalized AI security assistant!
This is how it feels when compliance is easy.
Strike Graph is a guiding light through security land.
Saves us a lot of manual work. And that makes life easier.
I can't say enough about the ease of the interface.
Amazing concierge experience and highly-experienced professionals.
Learn more about security compliance
Our extensive library of resources will answer all your questions from SOC 2 to GDPR.
Keep up to date with Strike Graph
The security landscape is ever changing. Sign up for our newsletter to make sure you stay abreast of the latest regulations and requirements.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)













