Welcome back! This is the third and final installment in our three-part blog series about the best way to create your TrustOps or security program.
We thought writing this series was important because we’re seeing many companies miss opportunities for growth because they’re approaching data security and privacy in old fashioned ways. For business and tech leaders to truly get out in front of the competition, they must reject these out-dated approaches and embrace a more holistic, trust-based perspective.
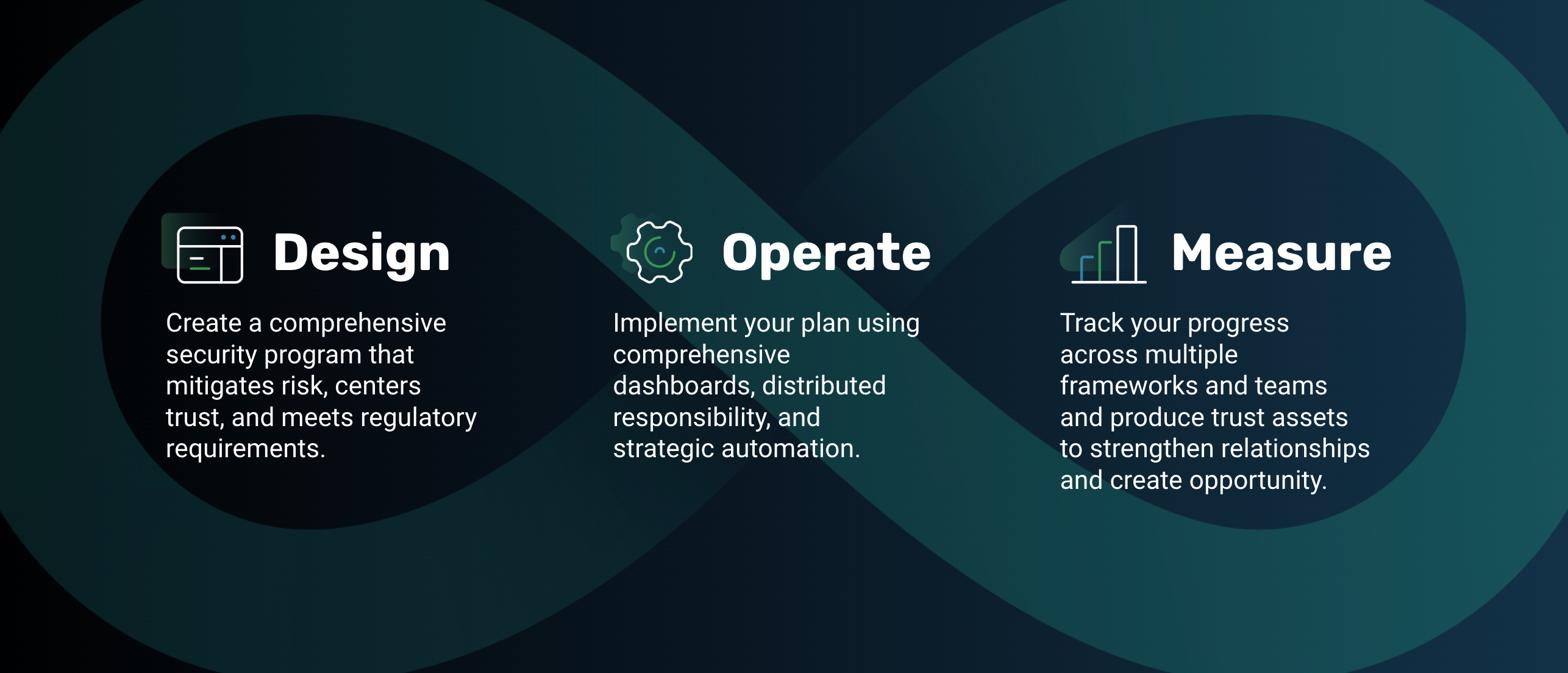
The best way to do this is to start viewing your security program as being made up of three interlocking phases: design, operate, and measure — the three installments of this series.
As a quick refresher, in the first post, we covered the design of your security program, and how instead of hiring a consultant or opting for a certification-in-a-box, it’s better to take a proactive approach and leverage technology — like compliance software — to build trust by designing a TrustOps program.
In the second post, we talked about the operation of your security program. Rather than throwing together a hodge-podge team that doesn’t have the necessary expertise, or using compliance tools that don’t adapt to your existing systems, we recommend choosing comprehensive compliance software that supports you now and into the future.
This all brings us to our third blog — this post — in which we’ll discuss the outdated ways most organizations are still measuring their security programs, as well as the best practices you should be implementing to efficiently and accurately measure and certify your own.
Let’s get to it!
The outdated way of measuring a security program
Unfortunately, most businesses are still using outdated methods to measure their security programs, including hiring auditors, relying on tools that don’t serve them, and using multiple measuring sticks to ensure compliance. Let’s take a closer look at all three of these missteps now.

Hiring an auditor
In order to measure their security programs, most companies hire auditors. You might be wondering, “What’s wrong with that? That’s what everyone does, right?”
You’re right in thinking that far too many companies still take this route, but it’s not the best decision.
- Cost: Hiring an auditor is expensive, especially if you need to engage a big firm. And it’s not a one time expense typically — auditors are motivated to continue billing you hourly. These costs can be a significant burden, especially for smaller businesses or organizations with limited budgets.
- Disruption: The auditing process can be disruptive to daily operations. That’s because auditors may need to access various systems and interview employees, which can take time away from your team’s ability to perform their regular tasks and responsibilities.
- Lack of Context: External auditors may lack an in-depth understanding of your organization's unique security needs, business processes, and risks. Therefore, their recommendations may not be tailored to your specific business situation, needs, or objectives.
Lack of proper tools
If you’re not aware of, or don’t choose to use, the latest tools for measuring the success of your security program, you won’t be able to make strong strategic decisions or understand what the impact of past decisions is. You’re left not knowing how to function efficiently and unable to determine if your program is even keeping your data safe.
All of this means you can get stuck continuing the same security program year after year, without much knowledge as to why they’re doing things the way they’re doing them.
Multiple measuring sticks
Currently, there are multiple measuring sticks in the form of different frameworks, standards, and regulations (think HIPAA, ISO 27001, SOC 2, etc.). For most mid-size and larger companies, complying with multiple frameworks is a necessity. The problem arises when organizations go after these different certifications piecemeal without a standardized approach to measuring their overall process. The result is security chaos.
The more efficient and effective approach to program measurement
A holistic, tech-enabled approach to measuring your security program (TrustOps) isn’t only more efficient, it’s more effective too.
When companies have the tools they need to effectively self-assess their own security programs with less human involvement, it’s no longer necessary to hire a big, fancy auditing firm. That’s because an auditor only needs to come in to verify that the testing was thorough enough to result in reasonable assurance. And individual CPAs — who are more affordable — instead of big firms can easily perform the necessary verification.
Furthermore, the right compliance tools ensure that testing is easy, can compare multiple standards at any time, and is able to provide results upon request. This means that business managers tasked with compliance can demonstrate their success against the goal of compliance and report on the effectiveness of the program that they’ve established.
Where Strike Graph comes in
Strike Graph’s all-in-one compliance and certification platform automates testing to prove compliance and helps your organization achieve certification faster and with much less of a headache.
You’ll find useful measurements and reports on our dashboard, which keeps business leaders abreast of all ongoing efforts in real time, empowering them to make strategic, informed, long-term decisions when they need to.
Additionally, our platform produces trust assets — like certifications, reports,and attestations — that drive revenue. The Strike Graph trust asset library makes it easy to share these trust assets among team members, partners, and other stakeholders so there’s nothing standing in the way of your company’s success.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)