Imagine TrustOps as your secret weapon in a world where customer confidence is king. It's not just about ticking boxes with certifications; it's about setting your business apart. Building an effective and efficient TrustOps program is your secret weapon. And there’s no better time to get started than now.
This guide aims to provide you with a practical roadmap to build or enhance your TrustOps program. Doing so will position your organization at the forefront of data protection and privacy, solidifying your relationships with customers, partners, and stakeholders and ultimately boosting your bottom line.
Understanding TrustOps
TrustOps is a comprehensive approach to building trust that intertwines various elements crucial for maintaining organizational integrity and customer confidence. At its core are principles like risk management, security incident response, IT security, privacy practices, and operational trust initiatives.
Each of these components plays a vital role in building and sustaining trust within and outside the organization. By delving into each aspect, we can appreciate how they collectively form the backbone of a successful TrustOps strategy, transforming security and trust from mere objectives into an integrated, dynamic framework.
Let's explore these key principles in detail:
- Risk management is the identification, assessment, prioritization, and control of an organization’s risk — including legal, financial, security, economic, and strategic risk — in order to reduce the probability of incidents occurring. TrustOps teams measure and mitigate risks with a view toward building trust.
- A security incident response plan is used to responsibly handle data breaches if they do occur. Being transparent about the impact of an incident or breach in a clear and honest way can reduce reputational harm.
- IT security is the collection of activities undertaken to meet IT regulations and industry expectations. In TrustOps, security compliance is viewed as a trust — and thus revenue — builder rather than an unavoidable cost.
- Privacy practices ensure customer data is handled securely and ethically throughout the organization and give customers confidence that their information is safe.
- Operational trust initiatives are actions that are taken to incorporate trust into all activities and decisions of all departments. TrustOps teams are typically responsible for developing metrics to measure the effectiveness of these activities.
Essentially, TrustOps combines trust and security into a cohesive strategy by integrating security measures with transparency, compliance, risk management, and user-centric practices. By adopting this comprehensive, collaborative, and adaptive approach, security and trust become not separate objectives, but two parts of one whole.
And, the payoffs for your business are big. Here are some of the key benefits of a successful TrustOps program:
- Comprehensive security and risk management: TrustOps ensures a holistic approach to security, compliance, and privacy, addressing these elements cohesively.
- Incident response preparedness: TrustOps prepares businesses for security incidents, enabling them to minimize damage, recover swiftly, and maintain customer trust after an attack.
- Enhanced customer trust and reputation: A strong TrustOps program demonstrates a commitment to data security and user privacy, enhancing a business's reputation, building trust, and fostering long-term relationships with customers, partners, and stakeholders.
- Transparent communication: TrustOps promotes clear communication about security measures and practices, showing businesses to be accountable and trustworthy.
- Mitigated third-party vendor risk: TrustOps principles are vital for evaluating and ensuring that external third parties meet robust security standards, thereby mitigating supply-chain risks.
- Competitive advantages: A robust TrustOps framework can provide a competitive edge by showcasing a business's commitment to security and trust.
- Innovative and agile responses to changing technology: TrustOps encourages adaptability and innovation in responding to evolving technology landscapes, maintaining continuous compliance and readiness.
Building your own TrustOps program
Now that you've got a handle on what TrustOps is all about and why it's crucial for today's businesses, it's time to take a look at the practical side of things. Below, you’ll find insights and actionable steps to support you as you build and implement a TrustOps program tailored for your organization.
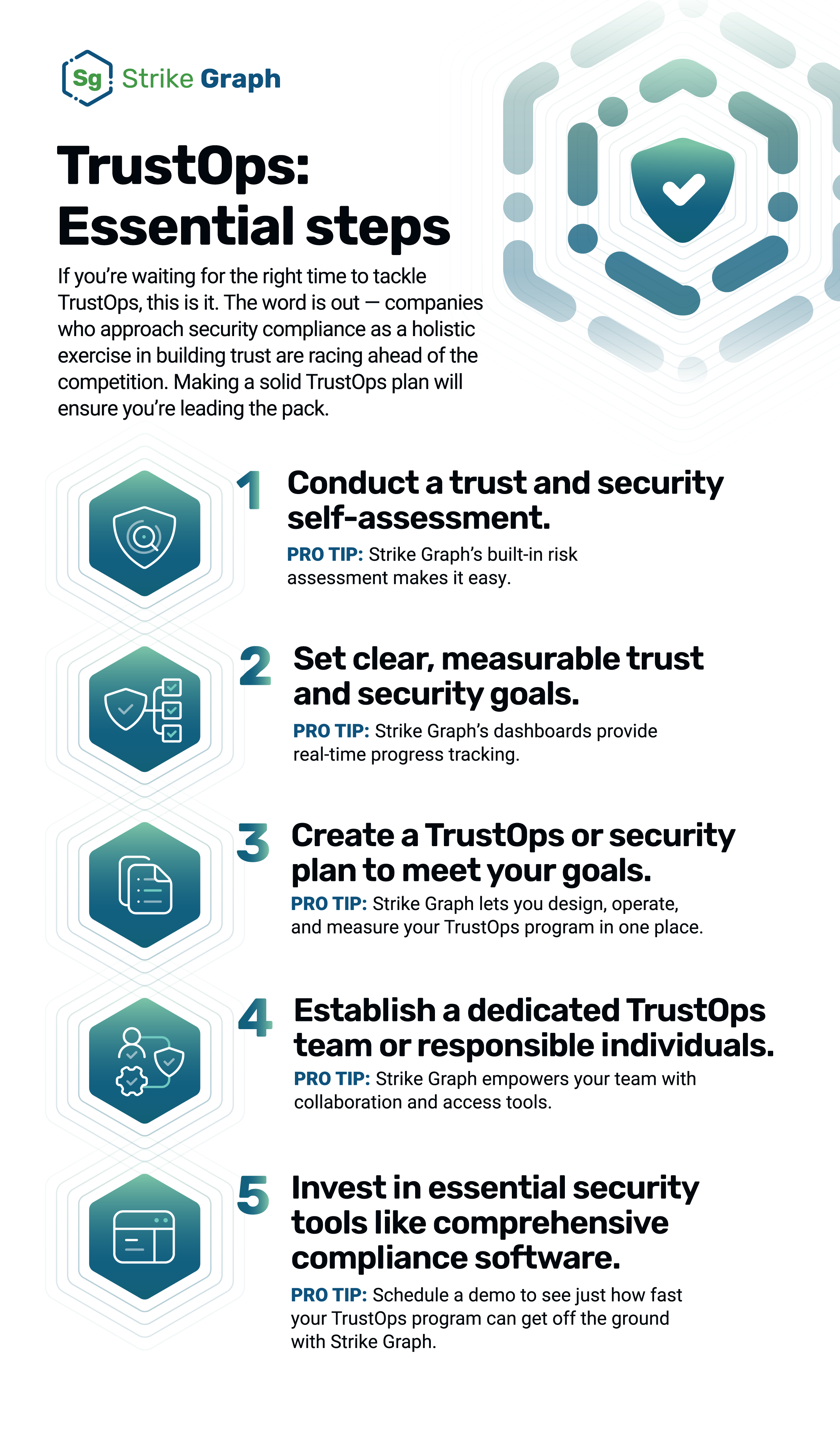
1. Assess your current trust and security posture
Starting with a self-assessment of your organization's current trust and security posture is like drawing a detailed map of where you stand in a vast landscape of information security and privacy threats.
The self-assessment’s goal is to thoroughly understand the current state of your security infrastructure. It involves looking into all facets of your security system — from the hardware and software you use to the networks you rely on and the strategies you employ to protect data. The idea is to get a clear picture of your organization's vulnerabilities and weaknesses.
Conducting a self-assessment serves another crucial purpose as well — it gives you valuable insights into which security frameworks are best suited for your business. Depending on the nature of your operations, certain frameworks may be more appropriate or even mandatory. For instance, if you handle a lot of customer data, frameworks focusing on data privacy and protection like GDPR or HIPAA might be relevant.
✔️ Strike Graph's built-in risk assessment tool and vulnerability scanning help you identify and rate the individual risks your company faces to ensure you close all your security gaps. And, because our platform supports multi-framework mapping, it’s simple to implement new frameworks with little or no extra work as your needs grow.
2. Recognize and leverage your existing TrustOps activities
In many organizations, TrustOps activities are already underway, even if they’re not formally recognized as such. Companies often engage in crucial TrustOps practices like conducting data security and privacy training, monitoring customer feedback, and tracking system uptime. Identifying these existing practices is a crucial first step in weaving them into a more structured TrustOps program.
But identification isn’t sufficient. Building on your foundation is key to strengthening your TrustOps position. This involves not just continuing with existing activities, but also enhancing them and integrating additional elements.
✔️ Strike Graph’s intuitive dashboards make it simple to see where you stand with TrustOps activities — from leadership-level overviews to granular tracking and collaboration tools for security operators.
3. Set annual trust and security goals
Setting annual trust and security goals is essential. Why? Because not only do they provide a clear direction for your organization, they build an internal culture of trust by indicating the importance your company places on building and maintaining trust with your customers.
Thoughtful goals create a framework by which to address risks effectively, allocate resources efficiently, encourage a culture of continuous improvement, and track security progress. Below are two examples of clear, measurable trust and security goals for you to model your goals on:
Example goal: Achieve ISO 27001 certification
Achieving ISO certification — or any other security certification, for that matter — enhances credibility, provides a competitive advantage, ensures compliance, reduces risks, and prepares you for security incidents. It is a good annual security goal because it is specific and measurable — not only in terms of if the certification was achieved but also whether holding this certification increased the company’s ability to close deals and bring in revenue.
Example goal: Ensure security status is reported quarterly to employees, leadership, board members, and investors.
Having consistent internal reporting is fundamental to TrustOps success. It ensures that decision-making is data-driven, fosters accountability and transparency, supports compliance efforts, facilitates efficient resource allocation, enhances communication, aids in crisis management, and promotes a culture of continuous improvement. And, it is a specific and measurable goal.
✔️ Strike Graph’s TrustOps platform provides the tools you need to set strong goals and then measure their success thanks to our design-operate-measure approach to TrustOps.
4. Identify your TrustOps team
Identifying a dedicated TrustOps team — or having a group of individuals responsible for trust and security — helps to ensure that all aspects of TrustOps are considered in a holistic manner throughout the organization. It also signals to every member of your organization that trust is important, which increases adherence to security protocols and accuracy of reporting.
In small or medium-sized businesses, TrustOps teams typically have a centralized structure with a small team or a single TrustOps lead reporting directly to senior management, often the CEO. Team members in these smaller businesses may handle TrustOps responsibilities along with other roles, allowing for a flexible and agile approach to trust and security issues.
In contrast, enterprise-level companies usually have a more complex TrustOps structure. They often appoint a dedicated Chief Trust Officer (CTrO) who oversees specialized sub-teams focusing on various aspects such as data privacy, security, and compliance.
Cross-functional collaboration is crucial among the members of your TrustOps team, be it small or large. Clear, efficient communication is the first step toward implementing consistent security policies and ensuring that everyone understands their role in maintaining trust and security.
✔️ Strike Graph teams and other collaborative tools make working within and across teams a cinch.
5. Create your annual TrustOps plan
Once you've established your TrustOps goals for the year, formed your TrustOps team, the real work begins: laying out the action plan. This step is all about getting down to the nitty-gritty of what needs to be done to achieve your goals. It involves detailing the steps necessary to meet your objectives and assigning these tasks to the appropriate team members.
However, this process isn't just about task allocation; it's about building a sense of shared purpose and direction. Everyone involved needs to understand not only what they're doing but why they're doing it and how it contributes to the broader TrustOps objectives of building and maintaining trust.
Real world example: We’re working toward SOC 2 compliance because we want to land enterprise customers and they require security assurances.
But remember, the TrustOps landscape is dynamic, and your plan needs to be adaptable. Regularly reviewing and updating your strategy is crucial. This means keeping an eye on your key performance indicators, assessing your progress, and being ready to pivot when necessary.
The goal is to maintain a course that's both responsive to current needs and aligned with your long-term trust-building objectives. This adaptability is essential to ensure that your TrustOps plan stays relevant and effective throughout the year, allowing your organization to navigate the complex and ever-changing terrain of data privacy, security, and trust
✔️ Strike Graph makes it easy to assign responsibility for specific controls to individual team members, and our measurement tools let you track and adjust throughout the year.
6. Harness the power of AI and automation
Building a robust TrustOps or security program used to mean lots of expensive and slow vendors and processes. Not any more. Comprehensive TrustOps platforms, like Strike Graph, allow you to do everything in one place. And, AI and automation are new tools emerging in the TrustOps landscape to help improve efficiency.
It’s important to remember that while automation and AI offer significant benefits — they excel at optimizing processes, supporting tasks like automated evidence collection for security audits, and tracking compliance status — they cannot replace the strategic thinking and trust-building capabilities inherent to humans. The key is strategic implementation of AI and automation within your TrustOps program.
✔️ Strike Graph is dedicated to creating AI-driven tools that are innovative, effective, and secure — like our AI security assistant, automated evidence collection, automated testing and audit prediction.
Ready to start the year off right? Let’s get started!
Here’s a quick checklist to help you get the ball rolling.
At Strike Graph, we’re committed to ensuring you have all the tools, resources, and support your need to design, operate, and measure a robust TrustOps program that builds customer trust and boosts your revenue growth. Best of all? You can get started right away for free.
Or, if you'd rather connect with one of our TrustOps experts, schedule a demo and we'll show you how Strike Graph can help you build a cutting-edge TrustOps program.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)








