Design > risk management
Conquer risk with Strike Graph
Our comprehensive platform gives you the tools to identify your company’s unique risks and mitigate them, building customer trust along the way.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!

Risk-based security compliance is the new standard
Traditional security checklists are slow, expensive, and fail to shield you from emerging threats. Strike Graph’s risk-based solution is more robust — and it saves you time and resources.
Tailored security
Tailor security measures to your unique risks, not generic standards.
Efficient resource allocation
Identify, prioritize, and allocate resources effectively for maximum protection.
Continuous improvement
Adapt and enhance your security posture continually.
Take a targeted approach to security compliance.
Companies manage risk at the most basic level to avoid breaking trust with customers, stakeholders, and employees. Learn how risk-based compliance saves you time and money.

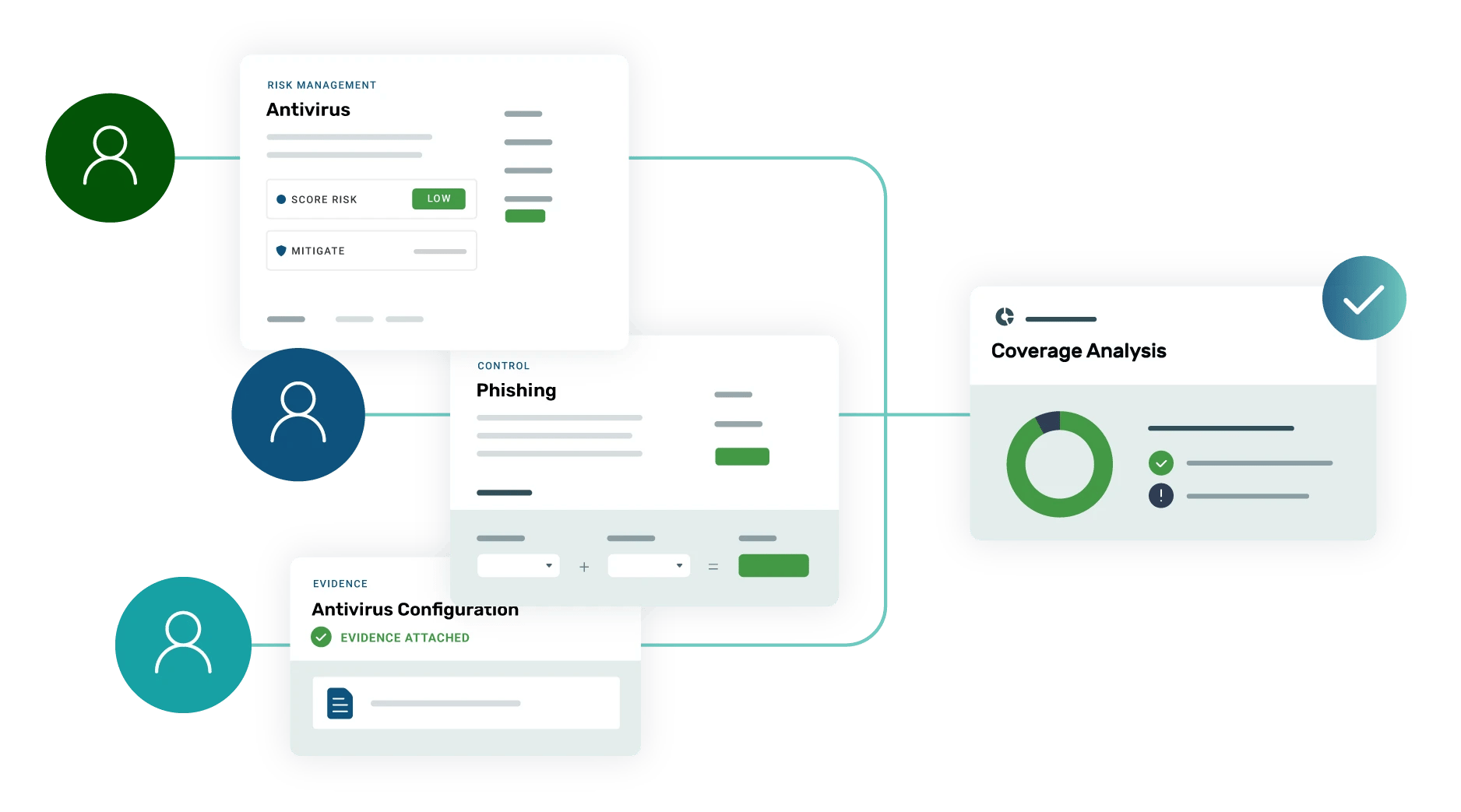
Your comprehensive risk management solution
Our all-in-one platform empowers you to assess and mitigate risk, then confirm your security program's efficacy.
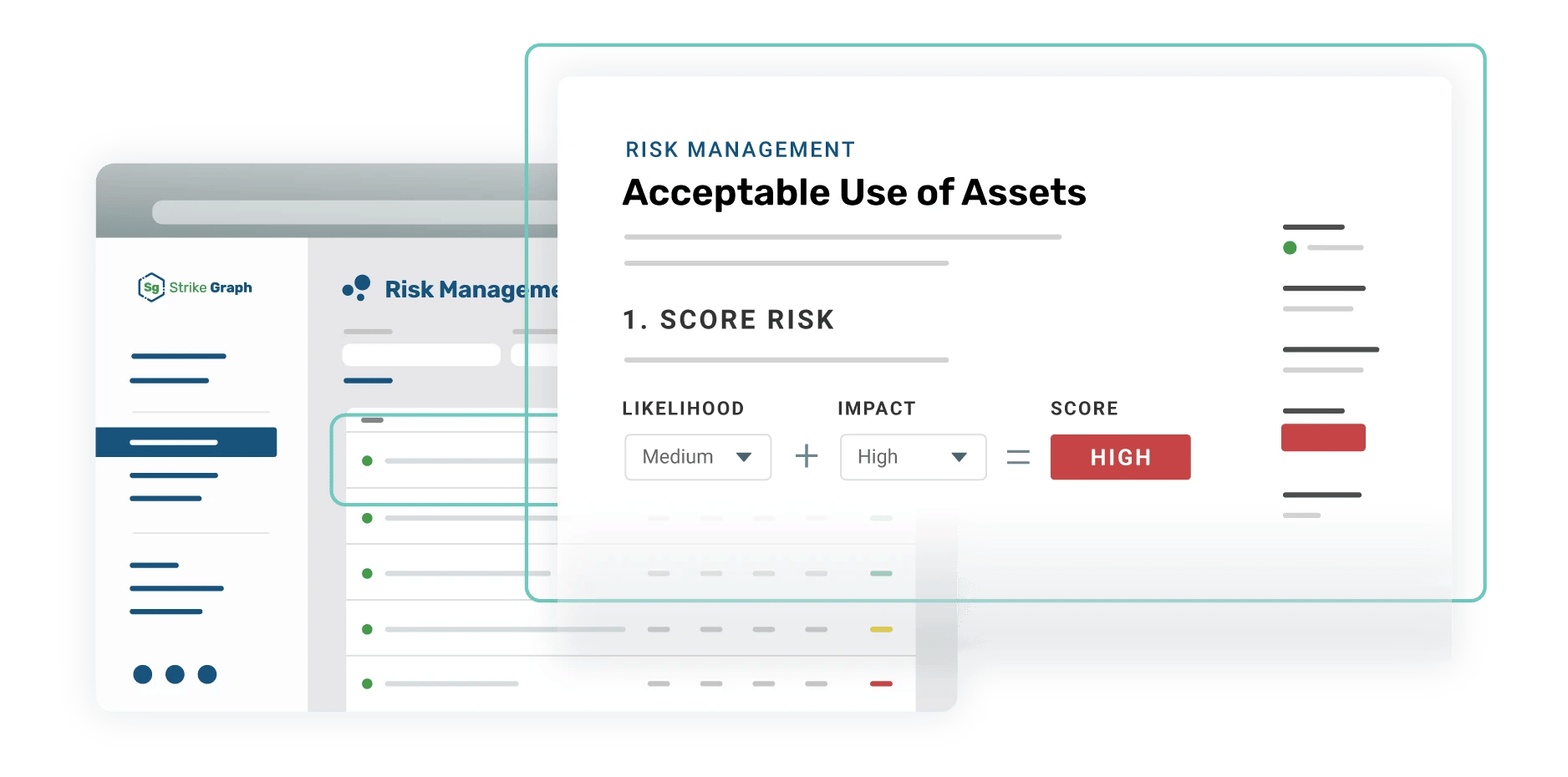
In-platform risk assessment
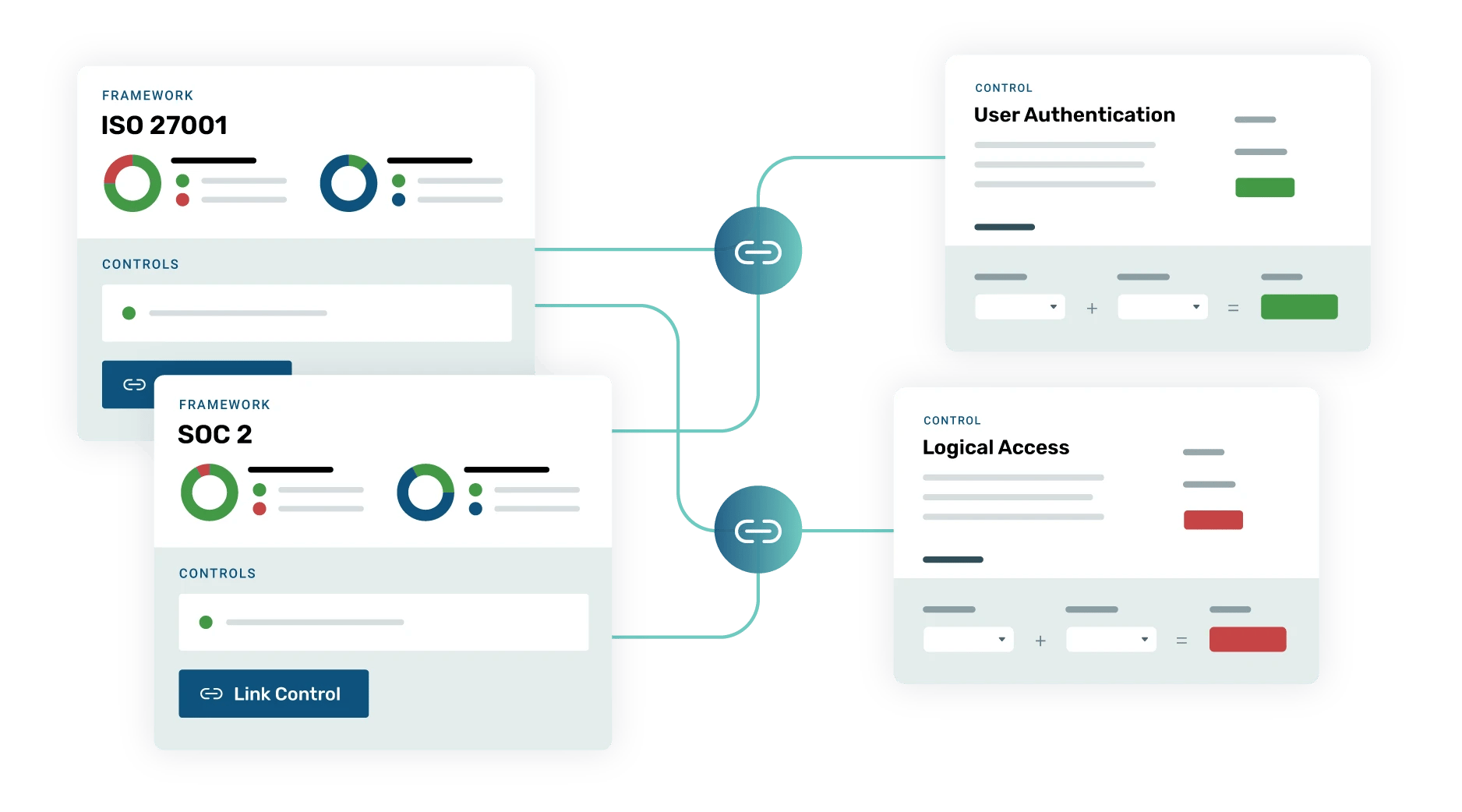
Multi-framework control mapping
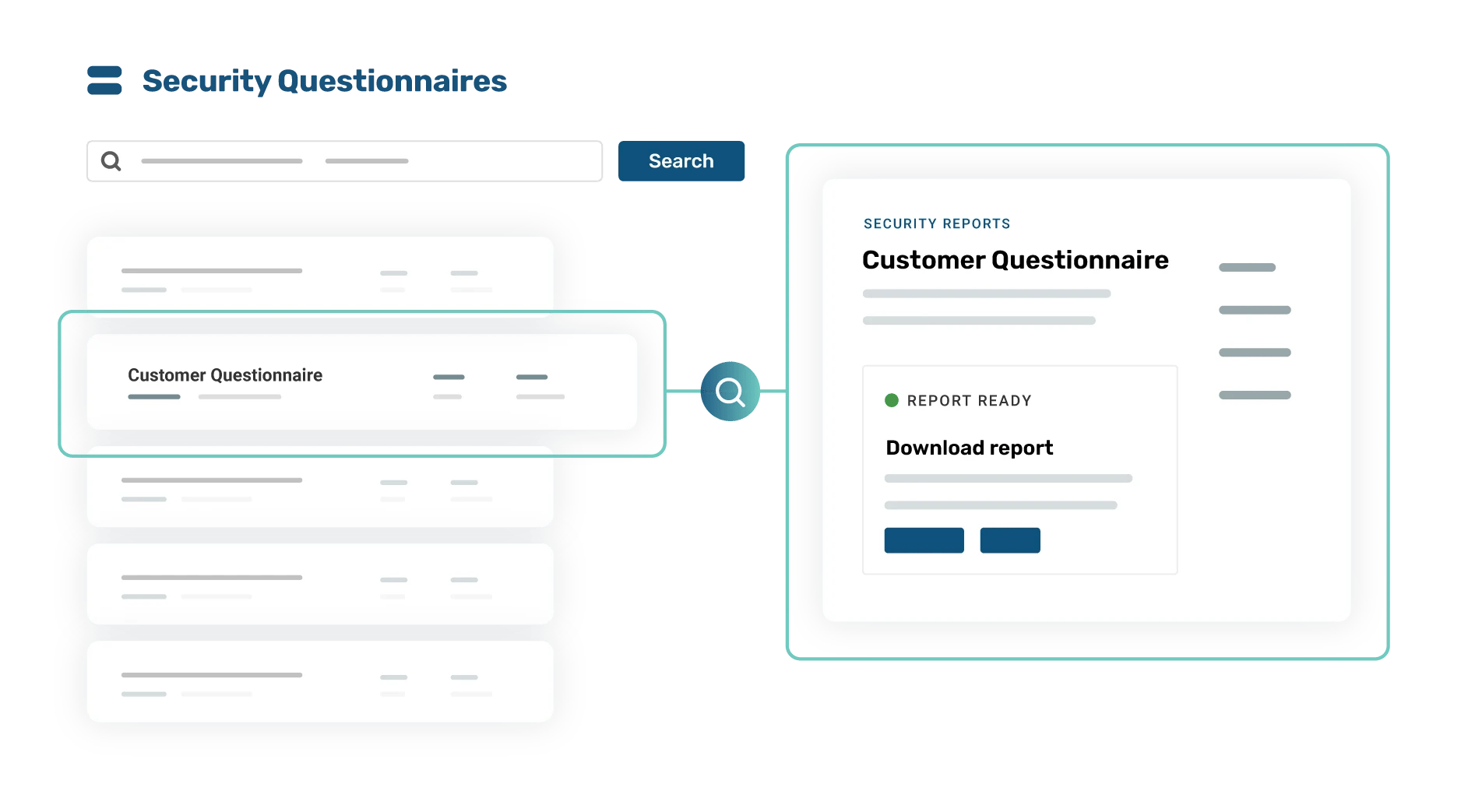
Streamlined security questionnaires
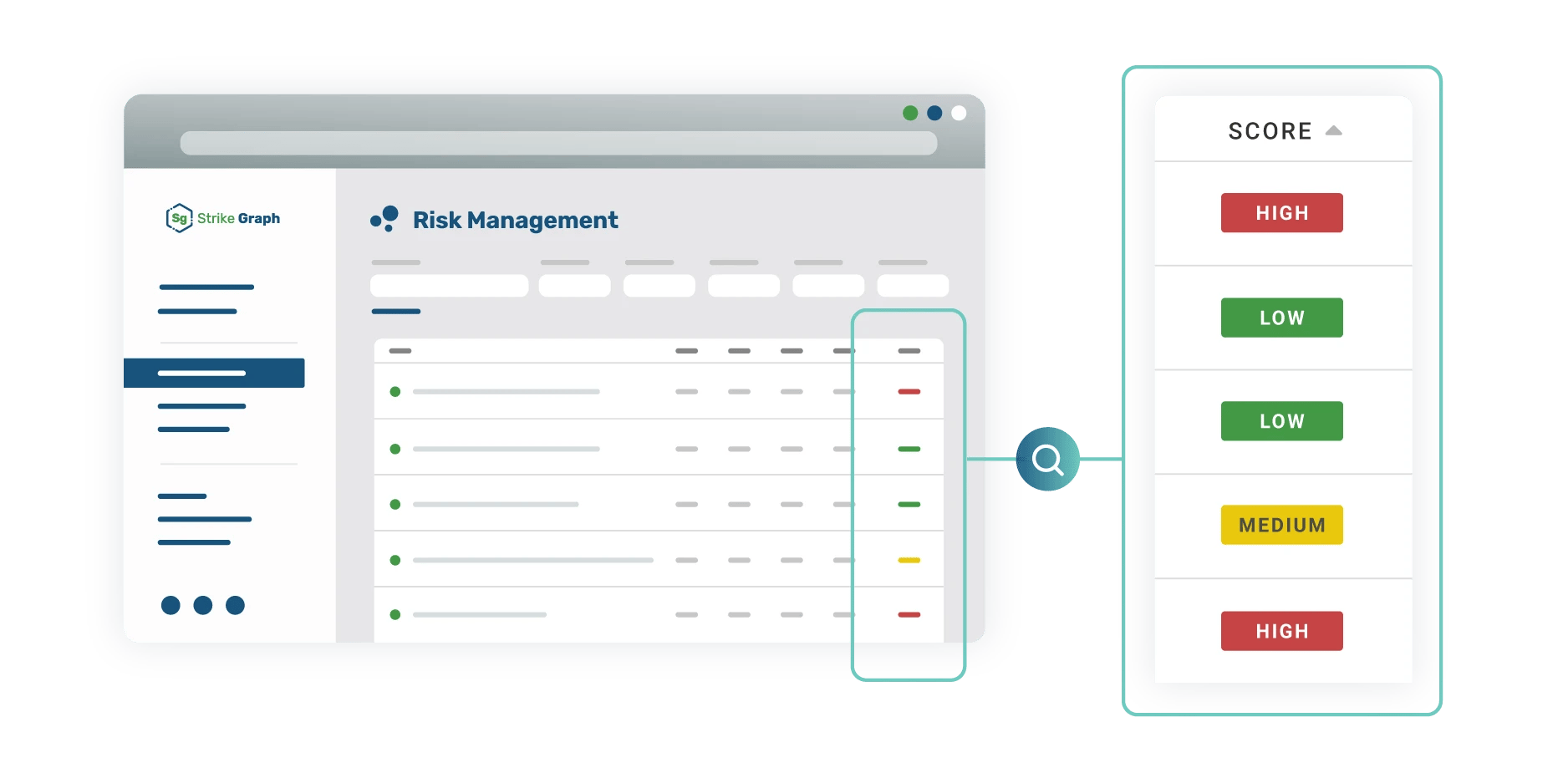
Assign risk ratings
Distribute responsibility
Join the hundreds of companies that rely on Strike Graph for risk management






Join the hundreds of companies that rely on Strike Graph for security compliance

Have more questions about risk management?
We have answers!
What are the 6 stages of risk management?
Risk management involves six basic stages:
- Identify: Conduct a risk assessment to understand weaknesses and identify threats.
- Analyze: Establish the probability and potential outcomes of each risk.
- Prioritize: Evaluate risks and rank them based on probability and consequence.
- Own: Determine who is responsible for managing each risk.
- Respond: Formulate a response plan for each risk.
- Monitor: Continuously monitor risks as part of an ongoing process.
Strike Graph’s in-platform risk assessment empowers you to identify, analyze, and prioritize your company’s unqiue risks then assign controls to mitigate them. Our collaborative tools allow you to assign responsibility for individual controls and our intiuitive dashboards show you exactly where you stand.
What are the seven types of risk in business?
Most business risks fall into these seven categories:
- Economic risk: risk due to macroeconomic forces such as inflation or policy changes
- Legal/compliance risk: risks from violating laws or regulations
- Security and fraud risk: risks from internal or external deception, including data breaches
- Financial risk: loss of money or assets, including market and currency risks
- Reputation risk: loss of confidence in a brand or product
- Operational risk: risks that halt business operations, like natural disasters
- Competitive risk: Loss of customers due to competition
Strike Graph’s in-platform risk assessment empowers you to identify, analyze, and prioritize your company’s unqiue risks then assign controls to mitigate them. Our collaborative tools allow you to assign responsibility for individual controls and our intiuitive dashboards show you exactly where you stand.
What is compliance risk management?
Compliance risk management involves processes to identify, assess, address, and monitor compliance risks. It aims to mitigate losses from noncompliance with laws, standards, regulations, and internal/external policies. It's important to continuously monitor and update compliance policies and procedures due to regularly changing regulations
Why are governance, risk, and compliance (GRC) and TrustOps important?
TrustOps and GRC are crucial for managing security risks and complying with regulatory requirements.
TrustOps, or trust operations, involves a wide range of methods and practices (including GRC) aimed at establishing and preserving trust with clients and partners. It also tracks the impact of a company’s trust-building activities on business outcomes like revenue.
GRC has a narrower scope. It consists of governance (overseeing information security), risk (managing information security risks), and compliance (establishing and maintaining compliance with regulations). GRC programs help in staying abreast of regulatory changes, preparing for new risks, managing third-party relationships, and adhering to data privacy trends.
Can’t find the answer you’re looking for? Contact our team!
Additional risk management resources
Our extensive library of resources will answer all your questions.
Additional risk management resources
Our extensive library of resources will answer all your questions.
Ready to start exploring?
Ready to revolutionize how you manage risk?
Why wait?
Get started for free.
The best way to understand how powerful the Strike Graph platform is is to jump right in and give it a spin.
Still have questions? Let us show you around.
Connect with Strike Graph today and step into the future of risk management.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)


