Work smarter not harder
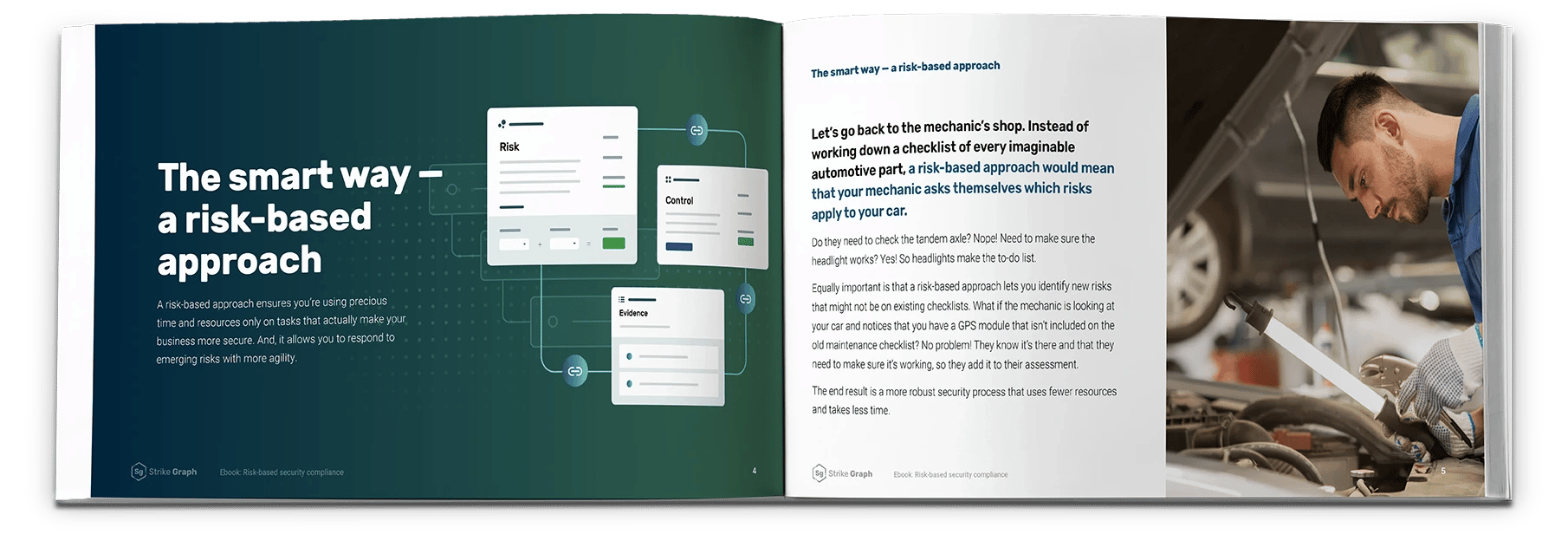
Outdated checklist approaches to security compliance waste time on tasks that aren't pertinent to your business. A risk-based approach focuses your resources where they actually make a difference.

Learn how risk-based compliance saves you time and money
Take a targeted approach to security compliance
In this free downloadable ebook, you'll learn why the AICPA recommends a risk-based approach, how ditching the checklists can save you time and money, and which software will help you get the job done.
No more checklists
Learn why checklists waste your resources without providing you the returns you want.
Why risk-based is better
Discover the power of looking at security compliance through a risk-centric lens.
Get started
Identify the risk-focused features you should look for in your compliance platform.
Boost the ROI of your security program
A risk-based approach builds more trust with your customers and stakeholders while spending fewer resources on your security program.

Strike Graph gets you certified fast.
Forget traditional auditing firms. Strike Graph takes you all the way to certification faster and more affordably than traditional solutions.
STEP 1
Design
Assess risk and design a strong security program that fits your business with Strike Graph’s extensive repository of policy templates, audit-tested controls, and educational articles.
STEP 2
Operate
Use the compliance dashboard to distribute ownership of risks, security controls, and evidence automation across the whole team, ensuring your organization meets its security contributions efficiently and effectively.
STEP 3
Measure
Easily measure and monitor the status of your controls so you’re always in compliance and ready for audit.
STEP 4
Certify
Give your partners and customers confidence you’re operating in compliance with all relevant regulations and industry-standard security frameworks with a Strike Graph compliance report.
The future is TrustOps
Revenue isn’t built on a single certification. It’s the product of a centralized, transparent approach to security and privacy that shows your stakeholders and customers they can trust you. Strike Graph is the platform that makes it possible.

Design
Assess risk and design a strong security program that fits your business with Strike Graph’s extensive repository of policy templates, audit-tested controls, and educational articles.

Operate
Use the compliance dashboard to distribute ownership of risks, security controls, and evidence automation across the whole team, ensuring your organization meets its security contributions efficiently and effectively.

Measure
Easily measure and monitor the status of your controls so you’re always in compliance and ready for audit.
Security compliance without the headache
Audit-tested control library
Over 450 audit-tested controls to pull from make compliance fast and easy.
Risk assessment
The risk assessment guides you through 40 common risk profiles to assess vulnerability.
System description builder
Develop a certification-compliant security narrative with templated language ready at your fingertips.
Evidence repository
Powerful evidence-collection automation gives your technology team the freedom to configure toward innovation. Workflow tools allow distributed responsibility for security ownership across your organization.
Compliance dashboard
Give leadership a bird’s eye view of your compliance program and day-to-day users a ground-level overview of risks, controls, and evidence.
AI-powered security questionnaire tool
Our AI-powered response engine uses your existing controls to fill out security questionnaires automatically.
Penetration testing
Certified penetration testing, in line with your compliance roadmap, is another critical sales asset required by buyers. Strike Graph certified penetration testing ensures customers trust your company to protect their important data.
Trusted by hundreds of fast-growing companies
Get the latest TrustOps news
Enter your email and we’ll send you useful resources to help you on your compliance journey.
