Software as a Medical Device
Master cybersecurity for medical devices
Elevate SaMD cybersecurity regulatory compliance management to the next level with Strike Graph. Centralized evidence management, streamlined workflows, and continuous monitoring, ensures your security posture remains strong from premarket to postmarket. With our expert support, you'll confidently meet and exceed FDA and EU regulatory standards, keeping your medical devices secure at every stage of their lifecycle.

The Landscape
US Pre/Post Medical Device Cybersecurity
Adherence to FDA Cybersecurity Guidance for premarket and postmarket phases, ensuring device security throughout lifecycle.
EU Medical Device Cybersecurity
Compliance with EU regulations, such as MDCG 2019-16 Rev.1 Guidance on Cybersecurity for medical devices, to protect patient data and device integrity.
SBOM
Essential for managing software supply chain risks and vulnerabilities.
HITRUST CSF
Addressing the unique needs of healthcare, HITRUST CSF provides a robust framework for safeguarding patient data.
ISO 27001
The gold standard for information security management systems, providing a comprehensive approach to data protection.
SOC 2
Focusing on security, availability, processing integrity, confidentiality, and privacy, SOC 2 is essential for cloud service providers.
ISO 42001
Provides a framework for the use of Artificial Intelligence with your SaMD platform

NIST CSF
A flexible framework for managing and reducing cybersecurity risk.
Challenges faced by the medical device industry
Balancing innovation and cybersecurity compliance
Aligning rapid product development with rigorous regulatory requirements like FDA Cybersecurity Guidance and EU MDR presents significant challenges. Integrating robust security measures while meeting strict timelines and ensuring patient safety necessitates a strategic approach.
Quality management system integration
Integrating cybersecurity frameworks is complex due to overlapping requirements, resource constraints, and the challenge of demonstrating compliance through effective documentation and evidence collection.
Premarket submission hurdles
Developing comprehensive premarket submissions is a time-consuming and resource-intensive process. Manufacturers face challenges in gathering substantial evidence to address cybersecurity risks and controls while adhering to rigorous regulatory expectations outlined in guidelines like FDA Cybersecurity Guidance.
Postmarket management burden
Postmarket management demands ongoing vigilance to address emerging vulnerabilities, deploy critical patches promptly, and effectively manage cybersecurity incidents to mitigate risks and ensure patient safety.
Crosswalk FDA and EU compliance
your work on these frameworks is cross walked to other industry standards (ISO 27001, HiTrust, SOC and many more)
Strike Graph's solution for the medical device industry
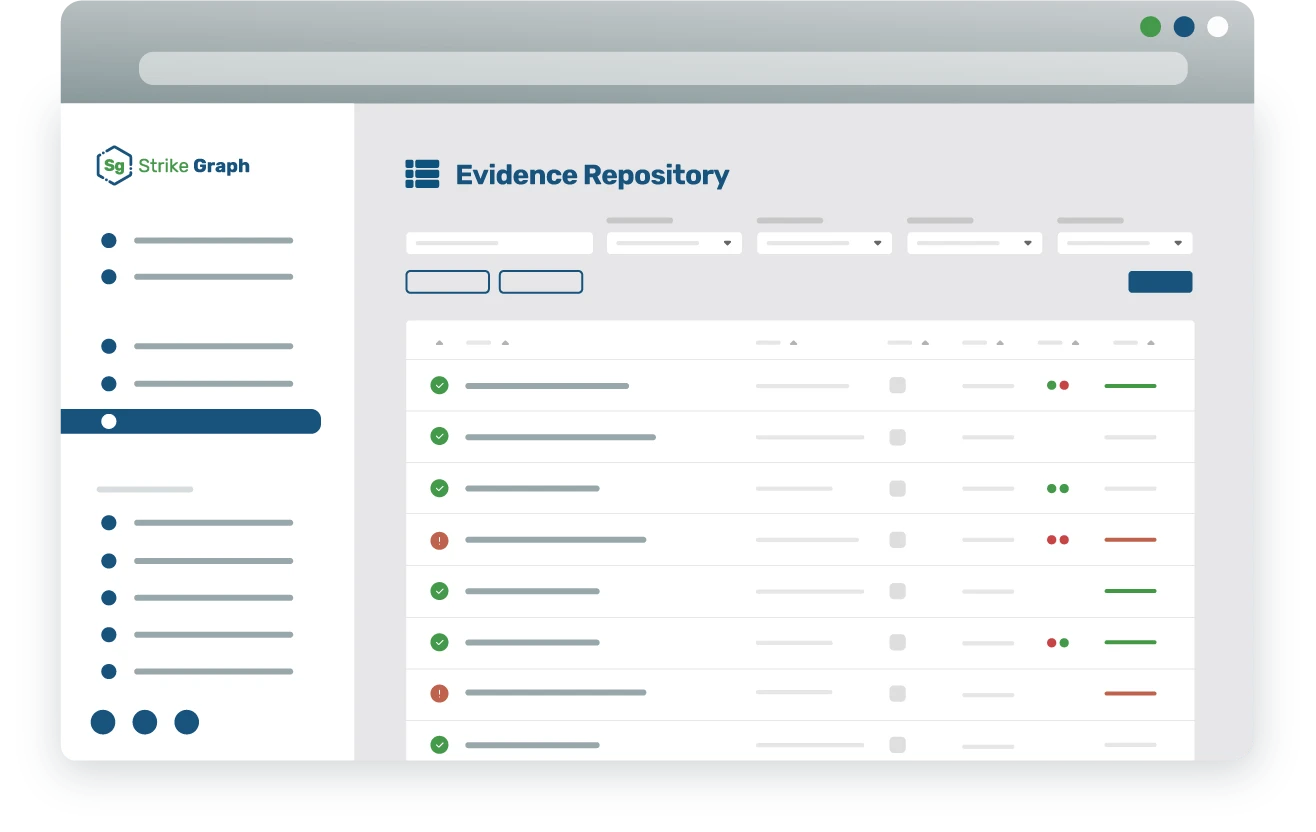
Streamlined premarket and postmarket management
Automate critical compliance and regulatory tasks across the entire medical device lifecycle. From premarket activities such as risk assessments, secure coding, and penetration testing integrated with the QMS, to postmarket functions like automated vulnerability monitoring, patch management, and incident response workflows, our platform ensures comprehensive cybersecurity coverage.
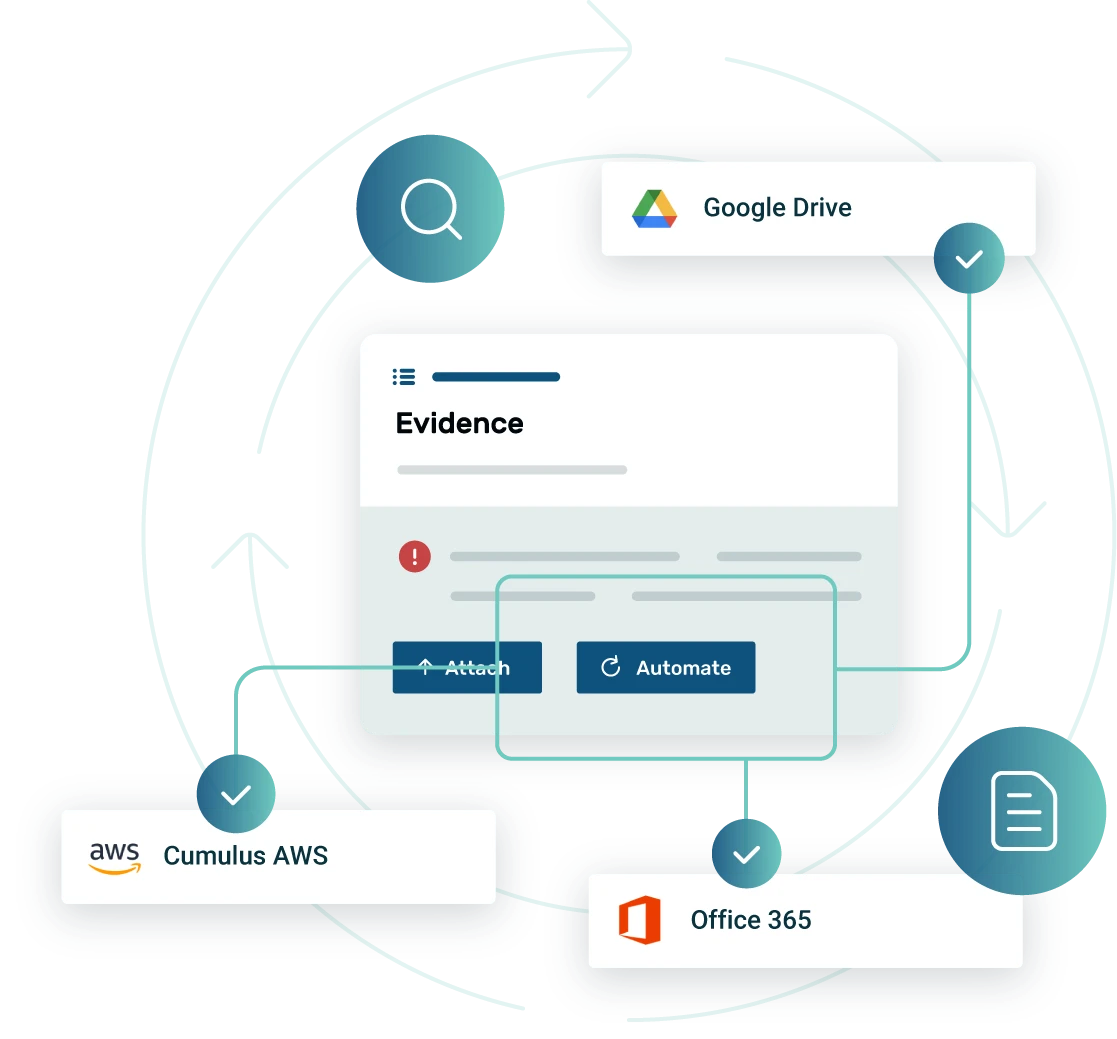
Automated evidence collection
Our centralized library revolutionizes medical device cybersecurity compliance by consolidating critical documentation into a single, accessible platform. This eliminates the manual burden of managing disparate files and ensures all evidence related to premarket submissions, postmarket surveillance, and quality management systems (QMS) is readily available for audits and regulatory inspections. By streamlining access to essential information, Strike Graph significantly enhances efficiency and reduces compliance risks.
.webp?width=1492&height=1069&name=general%20journey%20(10).webp)
Pre-built medical device security frameworks
Accelerate compliance with pre-configured libraries to other key compliance frameworks, aligned with critical medical device security regulations and best practices, including FDA Cybersecurity Guidance, EU Medical Device Cybersecurity, HITRUST CSF, SOC 2, ISO 27001, HIPAA, and ISO 42001. Our frameworks incorporate SBOM management to address software supply chain risks. Seamlessly integrate cybersecurity controls into your existing Quality Management Systems (QMS) for efficient compliance.

Real-time visibility and security insights
Real-time dashboards that provide comprehensive insights into the security posture of medical devices across their entire lifecycle. By continuously monitoring for vulnerabilities and potential threats, users can proactively identify and address security gaps. Detailed reports offer actionable intelligence to support informed decision-making, risk mitigation, and compliance with evolving regulatory requirements.
Additional benefits
Establish device resilience
while maintaining robust security through streamlined premarket and postmarket processes.
Enhance patient data security
by exceeding regulatory requirements and building trust through automated compliance.
Scale your security posture
to adapt to evolving regulatory landscapes and business growth.
Reduce compliance burden
with automated workflows and centralized evidence management.
Gain a competitive edge
by demonstrating a strong commitment to patient safety and data privacy.
Additional Considerations
Manufacturers
Include customer testimonials from medical device manufacturers who successfully achieved compliance with Strike Graph (FDA Cybersecurity Guidance, SOC2).
Showcase
Showcase logos of recognized medical device security regulations (FDA Cybersecurity, EU MDCG 2019-16 Rev.1 Guidance on Cybersecurity) throughout the webpage.
Free Quote Request
Integrate clear pricing options or a free quote request option.
Accelerate
Get certified faster
Develop a blog section with informative content related to medical device cybersecurity best practices, emerging threats, and regulatory updates.
See what our customers say
“The team at Strike Graph has a deep understanding of what we needed to do to achieve SOC2 compliance. Their expertise helped us identify the controls we needed for our business and their application made it easy to document and upload evidence.”
“The team at Strike Graph has a deep understanding of what we needed to do to achieve SOC2 compliance. Their expertise helped us identify the controls we needed for our business and their application made it easy to document and upload evidence.”
“The team at Strike Graph has a deep understanding of what we needed to do to achieve SOC2 compliance. Their expertise helped us identify the controls we needed for our business and their application made it easy to document and upload evidence.”
Join the growing list of companies who understand trust is paramount
.png?width=800&height=118&name=whylabs-logo-for-light-background%20(1).png)
hs.png?width=354&height=178&name=Wellinks%20logo)hs.png)
.png?width=353&height=177&name=Octagos%20Health%20(2).png)
Medical Device Cybersecurity
Best Practices
Receive immediate, precise answers to security questions, allowing your team to focus on what they do best. Gone are the days of wading through dense security manuals – welcome to an era of instant security insights and streamlined processes.
Emerging Threats
Receive immediate, precise answers to security questions, allowing your team to focus on what they do best. Gone are the days of wading through dense security manuals – welcome to an era of instant security insights and streamlined processes.
Regulatory Updates
Receive immediate, precise answers to security questions, allowing your team to focus on what they do best. Gone are the days of wading through dense security manuals – welcome to an era of instant security insights and streamlined processes.
Additional resources
Our extensive library of resources will answer all your questions.
Ready to start exploring?
Ready to revolutionize how you manage data center security compliance?
Simplify SaMD security compliance
The best way to understand how powerful the Strike Graph platform is is to jump right in and give it a spin.
Secure your medical devices and accelerate time to market
Connect with Strike Graph today to see how you can achieve your compliance goals.
Ready to see Strike Graph in action?
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Find out why Strike Graph is the right choice for your organization. What can you expect?
- Brief conversation to discuss your compliance goals and how your team currently tracks security operations
- Live demo of our platform, tailored to the way you work
- All your questions answered to make sure you have all the information you need
- No commitment whatsoever
We look forward to helping you with your compliance needs!
Ready to see Strike Graph in action?
Fill out a simple form and our team will be in touch.
Experience a live customized demo, get answers to your specific questions , and find out why Strike Graph is the right choice for your organization.
What to expect:
- Lorem Ipsum is simply dummy text of the printing and typesetting industry.
- Lorem Ipsum is simply dummy text of the printing.
- It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout.
- The standard chunk of Lorem Ipsum used since the 1500s
We look forward to helping you with your compliance needs!
Fill out a simple form and our team will be in touch.
Experience a live customized demo, get answers to your specific questions , and find out why Strike Graph is the right choice for your organization.
What to expect:
- Lorem Ipsum is simply dummy text of the printing and typesetting industry.
- Lorem Ipsum is simply dummy text of the printing.
- It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout.
- The standard chunk of Lorem Ipsum used since the 1500s
We look forward to helping you with your compliance needs!
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)


