Don't guess on HIPAA. Get certified!
Strike Graph empowers you to meet HIPAA requirements then prove you're in compliance with our revenue-boosting certification.
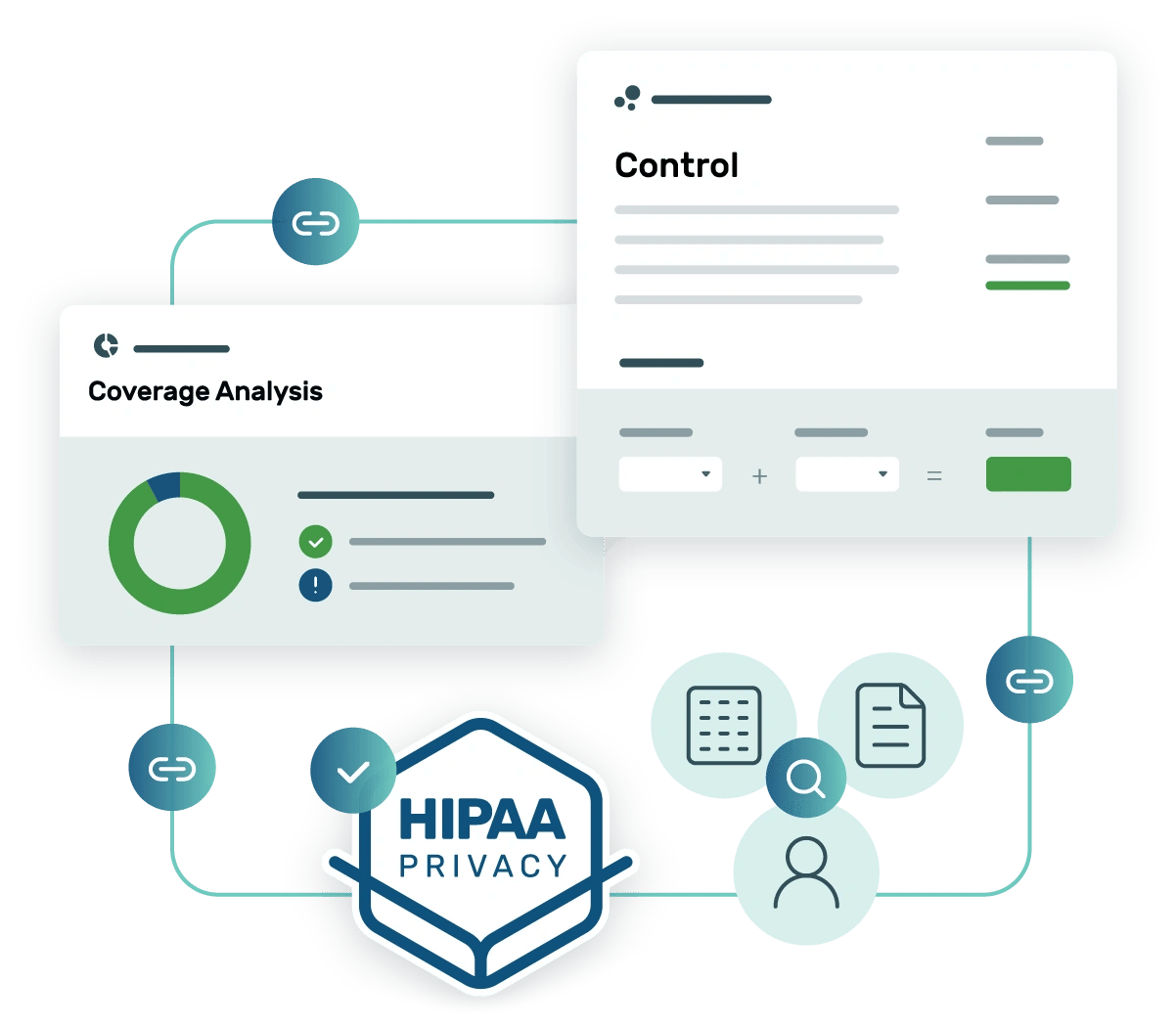
In health care, reputations are hard to build and easy to lose.
When your business involves personal health information, trust is your greatest asset. Certifying your HIPAA compliance is the best way to safeguard your reputation — and avoid costly fines due to HIPAA violations.
DIY is dangerous.
HIPAA is complicated. And, without an audit, you can think you’re in compliance until you suddenly receive notification you have HIPAA violations.
Strike Graph is a sure thing.
Our certification audit ensures you're in full HIPAA compliance so you can rest easy and build trust with customers.
Why HIPAA matters.
The Health Insurance Portability and Accountability Act (HIPAA) is a US federal law that sets standards for protecting sensitive patient health information. It mandates the confidentiality and security of healthcare records and transactions, ensuring patient privacy. HIPAA compliance is crucial for healthcare providers, insurance companies, and their business associates, as it governs how personal health information is used and disclosed. Non-compliance can lead to legal penalties and damage to reputation and compliance opens the way to business opportunities with HIPAA-obligated companies.

-min.png?width=2000&height=900&name=Rectangle_20451_20(1)-min.png)
Strike Graph takes the guesswork out of HIPAA compliance.
100% certainty about compliance
Strike Graph lets you assess your organization’s unique risks, easily implement HIPAA-mapped controls, and then our tech-enabled audit team verifies you're meeting requirements.
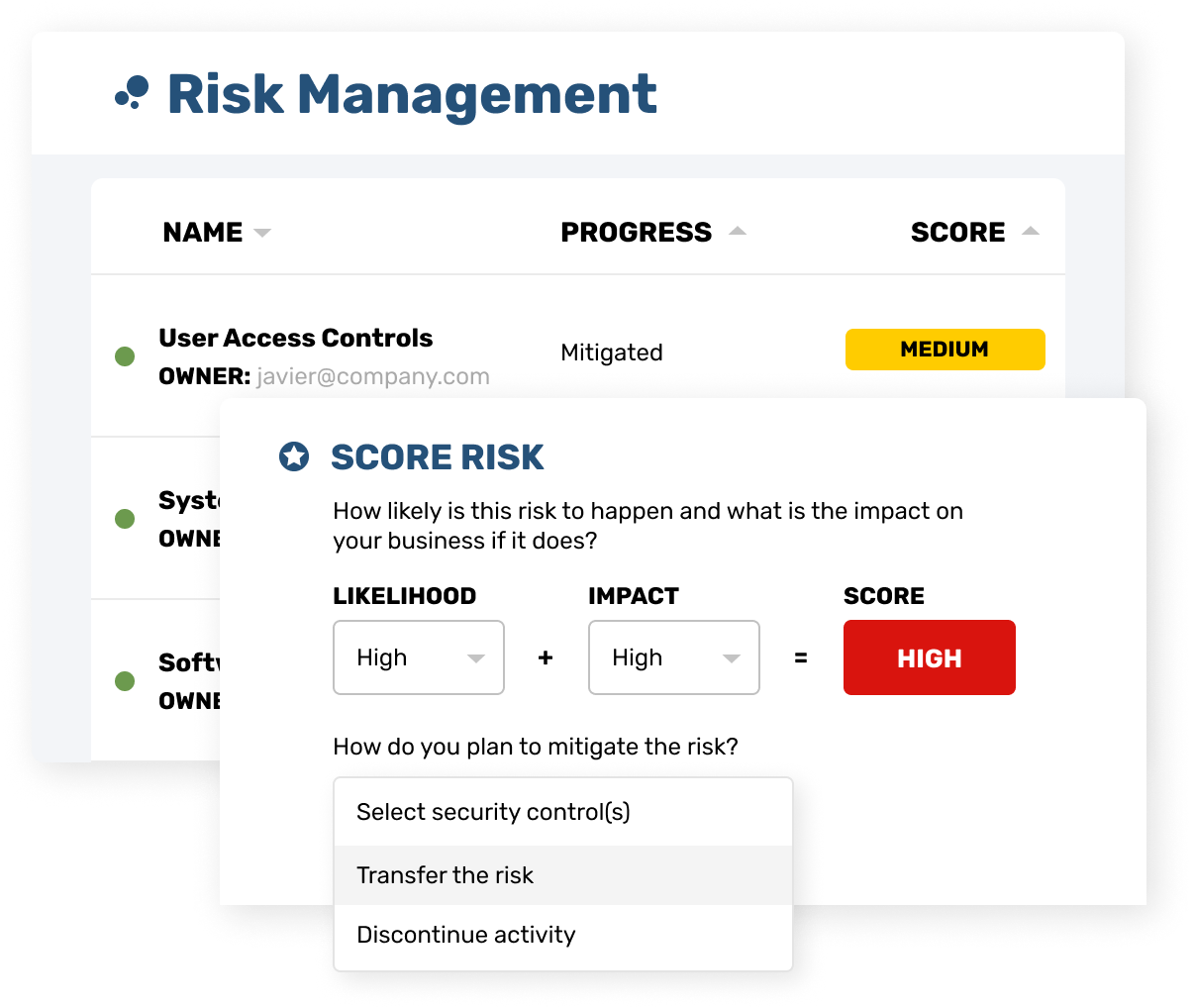
HIPAA-ready templates for quick documentation
Strike Graph’s extensive library of templates for HIPAA privacy and security templates means you don’t have to start your documentation from scratch. Use the templates as-is, or customize them to fit your unique needs.
.webp)
HIPAA privacy support
The stringent requirements of the HIPAA privacy rule are a challenge for covered entities. Strike Graph simplifies the process and proves you're meeting all privacy rule standards.
Packed with useful features
penetration testing
Strike Graph’s initial assessment identifies areas of risk.
Implement controls to close your gaps.
Get certified.
See what our customers think of Strike Graph.





Streamlining the compliance process
The pre-existing libraries to choose from are beneficial, as well as the ability to add our unique controls is highly efficient and user-friendly. … Strike Graph is an intuitive easy to use tool for efficiently working through the compliance process. Read more on G2.com
User in computer software
Strike Graph is your partner in compliance…
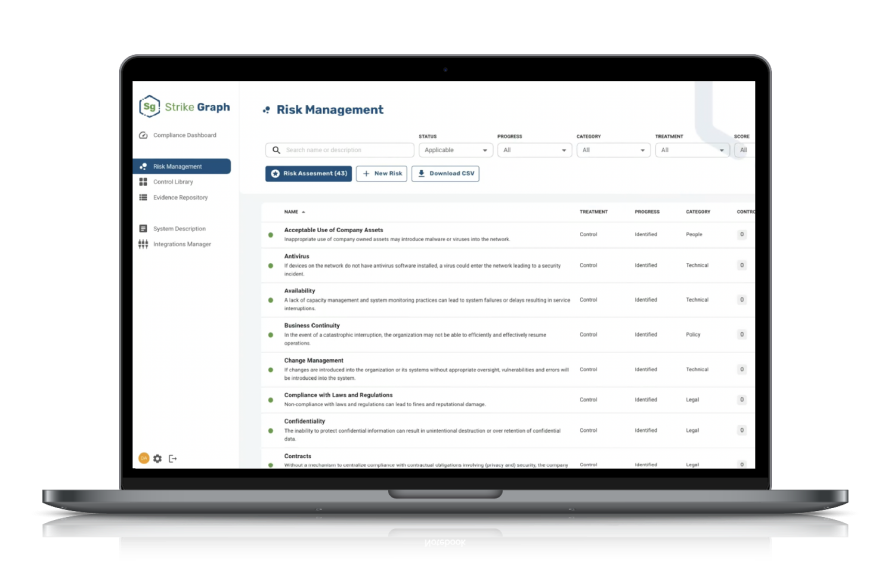
Strike Graph is your one-stop shop to get your security audits going and completed in half the time. There are file repositories for security audits, automated security questionnaires. evidence repository, and great support from the customer success team. Whether you need evidence of HIPAA, SOC2, or ISO, you're in the right place. Read more on G2.com
Administrator, information technology and services
Compliance powers confidence
I am pleased with the Strike Graph team helping us navigate our compliance ocean. I have been surprised how quickly we can make sense of the good policies and procedures we already have functioning internally with the frameworks we need to provide an attestation around. Read more on G2.com
Executive Sponsor in Computer Software
Strike Graph is trusted by hundreds of companies for HIPAA certification.

Dig into the details.
Check out our FAQs to learn what HIPAA is, if it applies to your organization, and how to avoid HIPAA violations.
What is HIPAA?
HIPAA stands for the Health Insurance Portability and Accountability Act of 1996. It’s a collection of medical privacy regulations for health-care organizations handling sensitive personal health information (PHI). HIPAA sets the standard for security, privacy, and integrity of patient data.
Who needs to be HIPAA compliant?
Any organization that collects, processes, stores, or shares protected health information is considered a covered entity under HIPAA. Covered entities include hospitals, academic medical centers, physicians, and other healthcare providers. Even if your business is not specifically a covered entity, you are subject to HIPAA rules if you enter into a business associate contract with a covered entity.
What is the HIPAA Privacy Rule?
The Privacy Rule sets national standards to protect patients' medical records and other personal health information. The HIPAA Privacy Rule applies to covered entities like healthcare clearinghouses, health plans, and other healthcare providers that conduct transactions electronically. The rule does not apply to business associates. The rule requires reliable measures to protect the privacy of personal health information (PHI). The rule establishes authorized actions and the required disclosures that apply to such data. In addition, the HIPAA Privacy Rule gives individuals rights over their health information, including rights to access and review a copy of their records and request modifications.
What is the HIPAA Security Rule?
The Security Standards for protecting electronic personal health information (ePHI) are a national set of standards establishing the protective protocols for health information that covered entities hold or transfer.The US Department of Health and Human Services (HHS) states that "the Security Rule operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards" that covered entities must implement to secure ePHI. Both covered entities and business associates are subject to the Security Rule. The Office for Civil Rights (OCR) mandates the enforcement of both the Privacy and Security Rules with voluntary compliance activities and civil money penalties.
Can my organization become HIPAA certified?
Strike Graph's experienced assessment team can provide a thorough HIPAA audit of your security program. Once the audit is complete, you will receive a HIPAA compliance certification report proving your company is meeting all applicable HIPAA requirements.
How can my organization become HIPAA compliant?
Organizations subject to HIPAA — covered entities — and their business associates are required to perform periodic technical and non-technical evaluations that establish the extent to which an entity's security policies and procedures meet HIPAA security requirements. These assessments can be performed internally or contracted through an external organization that provides certification services.
Organizations that determine they are covered entities must abide by the Privacy Rule, Breach Notification Rule, and Security Rule. Business associates are only required to meet the requirements of the Security Rule.
These basic steps are necessary to reach HIPAA compliance:
- Develop privacy and security policies.
- Develop an in-house team of HIPAA experts with a designated Privacy Compliance Office as required by the HIPAA Security Rule.
- Implement necessary security controls, including administrative, physical, and technical safeguards as recommended by the HIPAA Security Rule.
- Conduct regular risk assessment and self-audits to identify HIPAA compliance gaps.
- Obtain satisfactory assurances that business associates meet HIPAA requirements and can safeguard shared PHI.
- Develop a breach notification protocol.
- Document the process for future HIPAA audits and incident investigations.
How can my organization stay HIPAA compliant long term?
Organizations can follow these steps to maintain HIPAA compliance and avoid HIPAA violations or penalties:
- Partner with an expert who understands HIPAA requirements.
- Conduct an annual risk assessment.
- Perform frequent vulnerability assessments and penetration testing.
- Enhance security posture by implementing assessment recommendations.
- Maintain continuous employee awareness of HIPAA compliance requirements.
- Review business-associate contracts regularly for HIPAA compliance.
Can’t find the answer you’re looking for? Contact our team!
Additional HIPAA resources
Check out more helpful guides from our compliance experts!



Additional HIPAA resources
Check out more helpful guides from our compliance experts!
Want to know more?
Schedule a demo and one of our HIPAA experts will reach out to walk you step by step through our HIPAA compliance process.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)



