We simplify SOC 2 compliance.
You focus on growing your company.
Strike Graph’s stress-free, tailored approach means you’ll reach SOC 2 compliance in no time.
Don’t let SOC 2 compliance slow your momentum.
Cybersecurity requirements, like SOC 2 compliance, often catch companies off guard just as they’re reaching a critical stage of expansion.
Traditional compliance
Traditional approaches require hundreds of hours of work and don’t support cross-certification, leaving you back at square one when you’re ready to level up again.
Strike Graph
That’s where Strike Graph comes in. We take a holistic approach that prioritizes both speed and long-term benefits, so you achieve SOC 2 86% faster and are set up for future success.
Why SOC 2 matters.
Service Organization Control 2 (SOC 2) is a framework by the American Institute of CPAs (AICPA) for managing data security in service organizations, especially those handling customer data in the cloud. Focusing on security, availability, processing integrity, confidentiality, and privacy, SOC 2 is vital for tech and cloud computing firms. SOC 2 compliance assures clients that their data is managed securely and responsibly, which makes it essential for business relationships with larger corporations. This certification is increasingly important in the tech industry because it signifies a commitment to stringent data security and privacy standards.

-min.png?width=2000&height=900&name=Rectangle_20451_20(1)-min.png)
Strike Graph’s platform makes SOC 2 compliance simple and fast.
Everything you need — nothing you don’t
Forget one-size-fits-all compliance checklists. Strike Graph tailors the compliance process so you’re only investing time and energy into SOC 2 controls that are necessary for your business. The result? Faster, easier SOC 2 compliance.
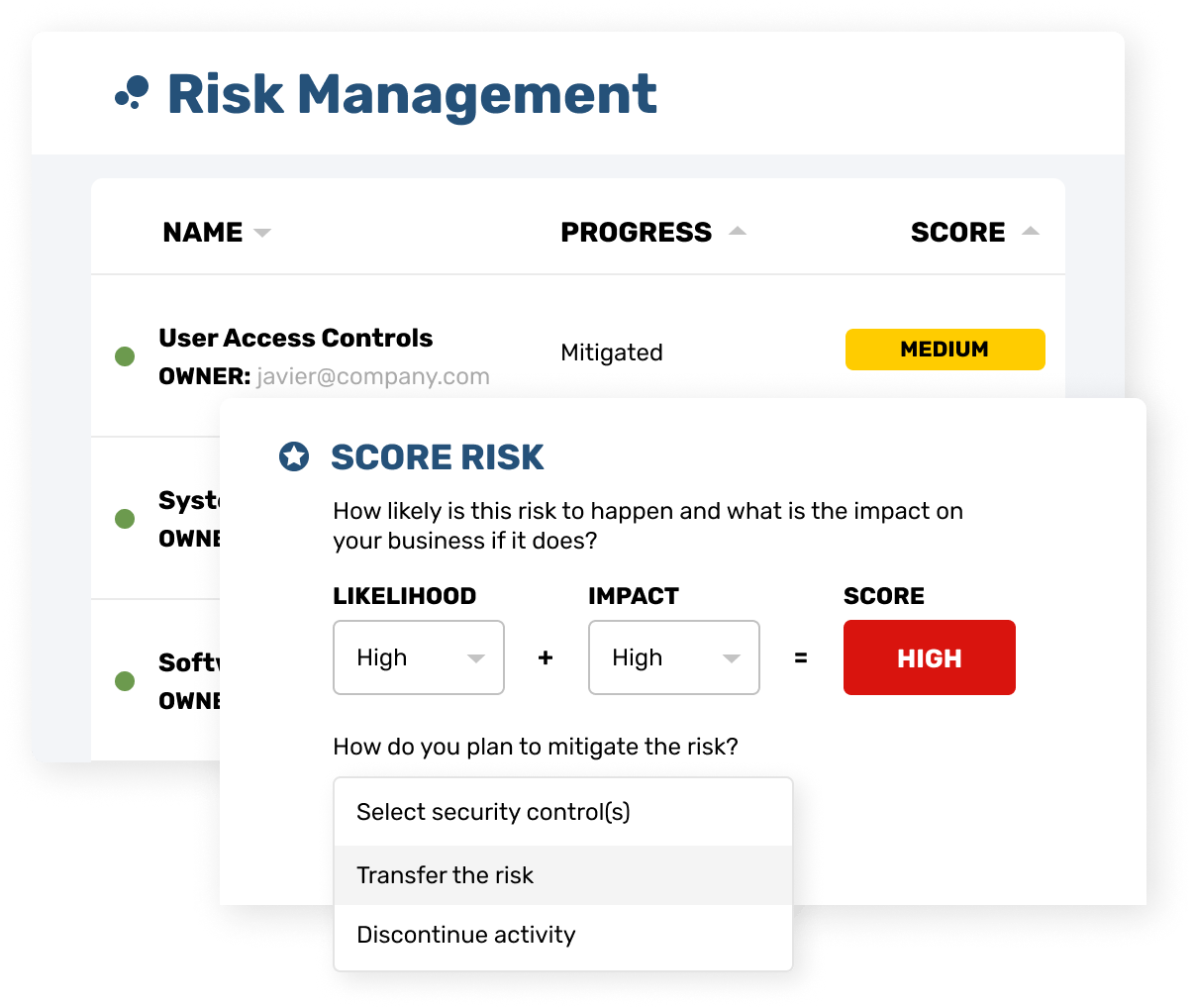
Automation to lessen the load
No one wants to waste time hounding colleagues for documentation. Strike Graph does that legwork for you. Our platform lets you automate SOC 2 evidence collection and maintenance reminders and assign responsibility to appropriate team members within your company.
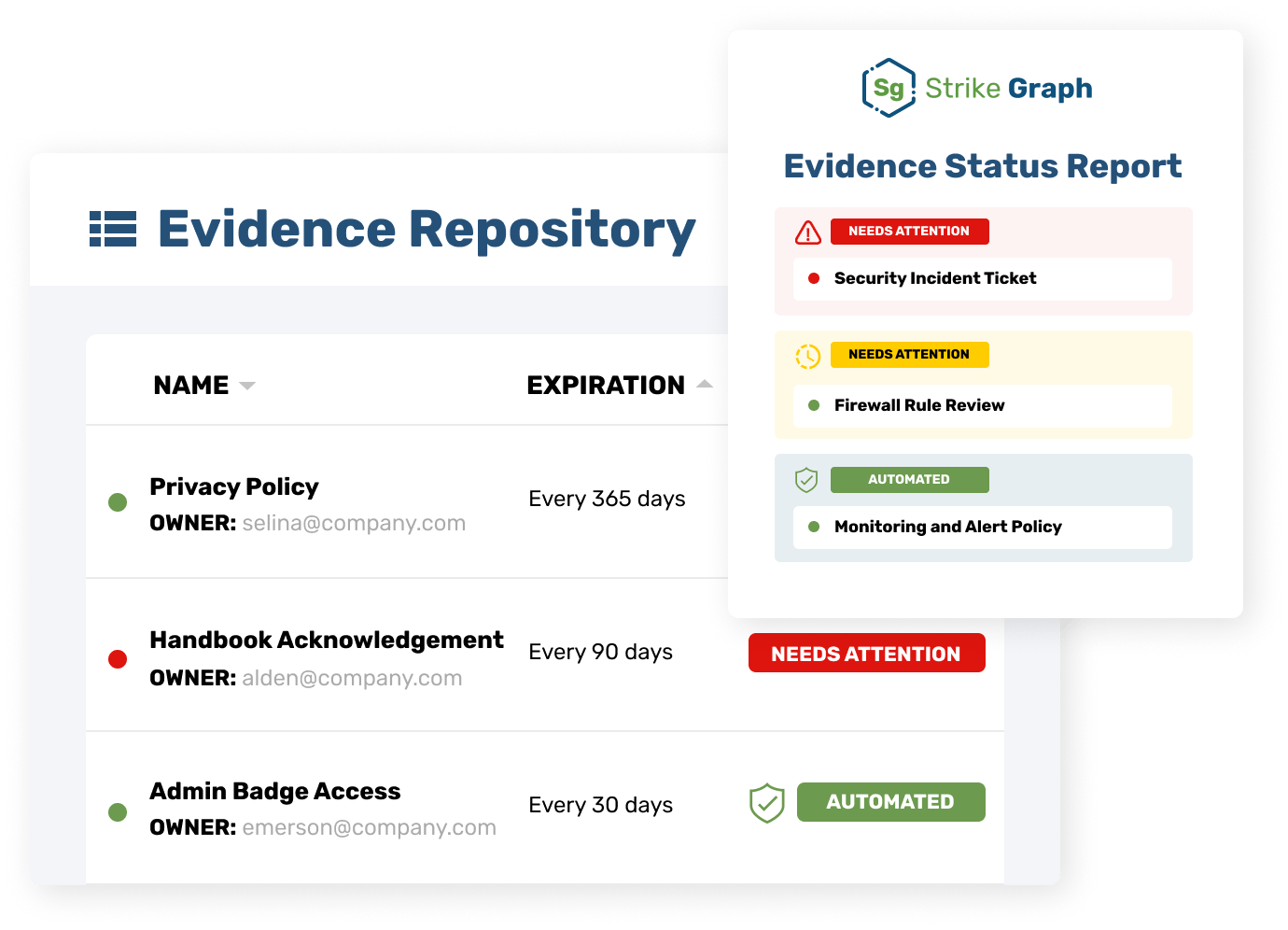
A strong foundation to build on
Traditional approaches to SOC 2 compliance are a 1:1 effort. You spend a lot of time and energy fulfilling requirements, you reach compliance, and that’s it. With Strike Graph, the controls and evidence you produce as part of the SOC 2 process allow you to maintain compliance easily, and they can be cross-applied to future cybersecurity certifications. One investment produces ongoing returns.
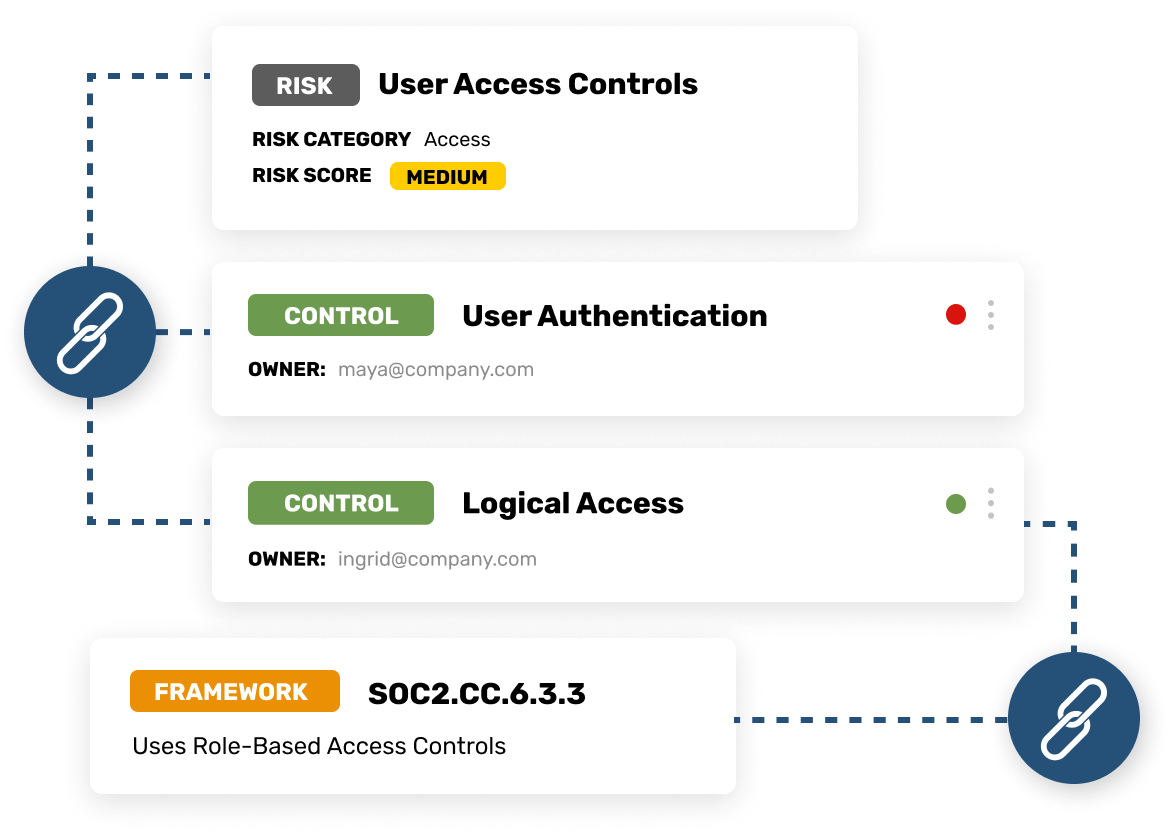
Packed with
useful features
penetration testing
support
Design
Operate
Certify
Our customers are SOC 2 compliant and stress free.





Thank you Strike Graph for my organization passing SOC 2!
I couldn't have pulled together everything needed for our SOC 2 audit in a short period of time without Strikegraph. I was able within a few weeks to complete a Risk Assessment using the tool, select the associated controls to mitigate the risks, and assign the controls to team members. I can't say enough about the ease of the interface …
Read more on G2.com
Debra B., Information Security Director at RedSeal
Strike Graph makes our cybersecurity compliance journey easy and successful.
Strike Graph's risk assessment helped us intelligently identify the cybersecurity controls we need for a successful SOC 2 audit. Without their support, we would have needed a consultant. The Strike Graph platform provides intelligence and flexibility so we can easily customize our cybersecurity compliance to our real-world needs.
Read more on G2.com
Executive sponsor, Information Technology and Services
Strike Graph is critical to our SOC 2 audit success
Strike Graph is the complete package — it is a practical and simple solution for tracking controls, assessing where we are at risk, and compiling audit evidence. … We highly recommend this product to anyone undergoing the security audit process.
Lauren L., Operations Manager
Join the hundreds of companies that rely on Strike Graph for SOC 2 compliance.
.png?width=800&height=118&name=whylabs-logo-for-light-background%20(1).png)

%20(1).png?width=476&height=200&name=Voxology-Logo%20(1)%20(1).png)
What is a SOC 3 report, and do I need one?
If you want to trumpet your data security successes far and wide, a SOC 3 report may be right for you. Unlike the SOC 2 report, which includes sensitive company operational and financial information, a SOC 3 report offers a high-level overview of your security posture — perfect for broad audiences. And, since it's based on your SOC 2 audit, it's a simple add-on with big benefits.

Dig into the details.
Learn the difference between SOC 2 Type 1 and SOC 2 Type 2, how to build a SOC 2 controls list, which Trust Services Criteria are required, and more.
What is the SOC framework?
SOC stands for System and Organization Controls. In common usage, the term SOC 2 refers to a report issued by an independent Certified Public Accountant (CPA) stating that an organization's data management practices are meeting a set of criteria issued by the AICPA. A SOC 2 is one of the most common attestations that service organizations can obtain, and it is becoming a requirement for security-conscious enterprises that rely on cloud service providers.
What are Trust Services Criteria (TSC)?
The SOC framework is based on five main Trust Services Criteria (TSC):
- Security — Also known as common criteria, a collection of both operational and security criteria
- Availability — How the system stays up and running
- Processing Integrity — How data is manipulated to produce the correct or expected result
- Confidentiality — How data is kept secret
- Privacy — How personal data is kept secret and protected
Unlike more prescriptive frameworks, such as PCI DSS and ISO 27001, SOC 2 allows organizations to identify relevant controls and show how they are meeting each criterion.
That said, nearly every SOC 2 must include the Security, or Common, TSC: control environment, communication and information, risk assessment, monitoring activities, control activities, logical and physical access controls, system operations, change management, and risk mitigation.
Strike Graph’s platform covers 100 percent of the TSC to ensure you can achieve the scope of SOC 2 that your buyers require.
Does my company need a SOC 2?
Any technology service provider or organization that stores, processes, or transmits customer data can benefit from a SOC 2 attestation. This includes managed service providers, banking and financial services, software as a service (SaaS) providers, data centers, cloud storage providers, and any other company that stores or collects data.
Being SOC 2 compliant demonstrates to customers that your organization has adopted a robust security program to protect their customer data in the cloud. The SOC 2 report gives your company a competitive advantage, helping you win and close deals faster.
What’s the difference between SOC 1, SOC 2 (Type 1 and Type 2), and SOC 3?
Addresses outsourced financial controls
One of the most common attestations that service organizations can obtain. It is becoming a requirement for security-conscious enterprises that rely on cloud service providers
Requires an audit evaluating a particular point in time. The auditor will assess the design of your company’s controls and decide whether they adequately cover the appropriate criteria
Adds an additional audit to assess whether controls have been operating over a period of time
Public-facing SOC 2 report
What is the timeline for a SOC 2 Type 2?
Type 2 audits are defined by their monitoring periods, meaning the "timeline" for these audits hinges on whether there is sufficient evidence of control operations throughout the entire period in question. Typically, for a Type 2 audit, a minimum of three months of operational data is required. So, if you establish the necessary security controls within the first month and then proceed to gather evidence proving they're effectively operational over the following three months, your organization should then be in a strong position to undergo a Type 2 audit.
Who conducts Strike Graph's SOC 2 audits?
The AICPA guidance on valid SOC 2 audits requires that a Certified Public Accountant, in good standing, performs the final assurance in the SOC 2 report (Section 2). Strike Graph works in partnership with a group of CPAs who are registered and peer reviewed so that our SOC 2 audits meet all AICPA requirements. Strike Graph supports our CPA partners with cybersecurity experts that are ISO certified and ISACA certified CISA and CISSP-credentialed auditors. Our valid registration of our CPA partners is available upon request.
Can’t find the answer you’re looking for? Contact our team!
Additional SOC 2 Resources
Check out more helpful guides from the Strike Graph team!

Additional SOC 2 Resources
Check out more helpful guides from the Strike Graph team!
Still have questions?
We’d love to give you a test drive.
Schedule a demo and one of our knowledgeable team members will be happy to walk you through Strike Graph’s SOC 2 compliance process.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)







