Complementary User Entity Controls, or CUECs, are the controls that you, as a SaaS (or other services) company want your customer to have in place in order for them to properly use your service. Listing relevant CUECs is one component of a great System Description (or Section 3). If SOC 2 lingo wasn't mysterious enough, be careful that you don't confuse CUECs with complementary subservice organizations controls, defined and described further down in this post.
How to determine your CUECs
Start by reviewing the CUECs within the SOC 2 reports of your own service providers. If you have more than Security in scope, you will also want to add CUECs that address the other Trust Services Criteria (Confidentiality, Availability, Processing Integrity and Privacy) that you include in your report.
The following questions may also be helpful (not all questions will apply, but the answer will lead you to the creation of relevant CUEC):
Risk mitigation
- Is the customer responsible for their own set of policies and procedures related to information security in their environment?
- Do customers need to assess risks related to the implementation of your service?
Logical and physical access
- Should your customer have their own set of Logical Access controls that relate to user provisioning, role-based access, user deprovisioning, and user access reviews?
- Will your customer be responsible for setting up their own users on your system?
- Will they require their users to have a unique login ID and password?
- Are they responsible for setting up strong password parameters when using your service?
- How often should your customer review the access their users have to your system?
- Are they responsible for removing users that no longer need access?
- Do any of the subcomponents of your service need special access rules?

Network security measures
- Are your customers responsible for implementing their own IT Security controls (such as antivirus, vulnerability scanning and pen tests)?
- Do customers need to identify an approved point of contact to interact with you?
- If there were to be a breach or incident, are they required to alert you?
Change management
- Should your customer be responsible for following their own change management processes when they make a change to their instance of your system?
- Do customers need to set up their own development and production environments or accounts?
- Do customers need to initiate the application of patches to their instance?
System operations
- Are your customers responsible for their own data storage, backup, and data restoration processes?
- Do customers need to configure their own instance?
Monitoring
- Do customers need to turn on or configure any kind of logging in order to effectively use your service(s)?
Your list of CUECs may look like this: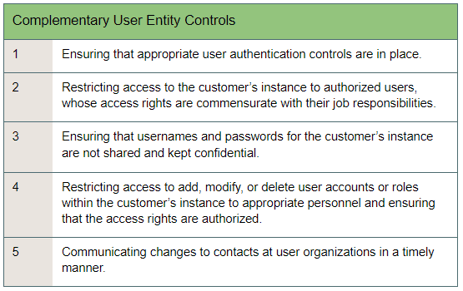
What are complementary subservice organization controls?
Complementary subservice organizations controls refer to the SOC 2 controls that you expect one of your service providers to perform. Even though they may be performed by another entity, they are still relevant and applicable to your system. Think of it this way - if one of your service providers failed to perform a backup control, or had control deficiencies with a change management control, their errors could impact your system.
The easiest way to approach complementary subservice organization controls is to methodically scan through all of the SOC 2 Criteria and Principles (that are in scope) and then identify any controls that are performed by others according to each category. Place these controls in one column (a summary of the controls is fine) and then in a second column note the associated Trust Services Criteria reference number. For example: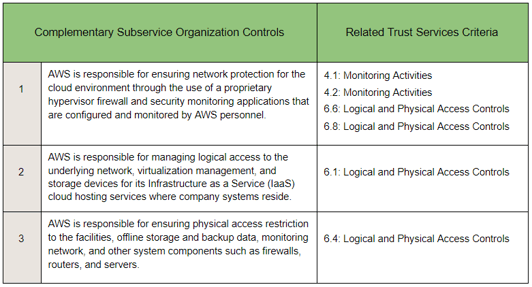
It is common for organizations to rely on their subservice provider(s) to:
- Manage logical access to their systems where your data or instances reside
- Implement physical and environmental safeguards, especially if the provider is performing data center services
- Restrict access to sensitive network components they manage
- Perform backups
The takeaway
Think of your Complementary User Entity Controls in terms of what security practices your customers must be responsible for. When writing your CUECs, make sure that the language you are using is specific, but not so technical that it could be confusing for some of your customers. Think of the complementary subservice organization controls as the controls that you are ‘outsourcing’ to your service provider.
.jpg?width=1448&height=726&name=Screen%20Shot%202023-02-09%20at%202.57.5-min%20(1).jpg)












